Remixing Functionally Graded Structures: Data-Driven Topology Optimization with Multiclass Shape Blending
Dec 01, 2021Yu-Chin Chan, Daicong Da, Liwei Wang, Wei Chen
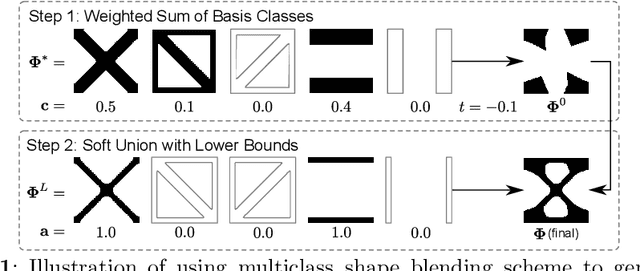
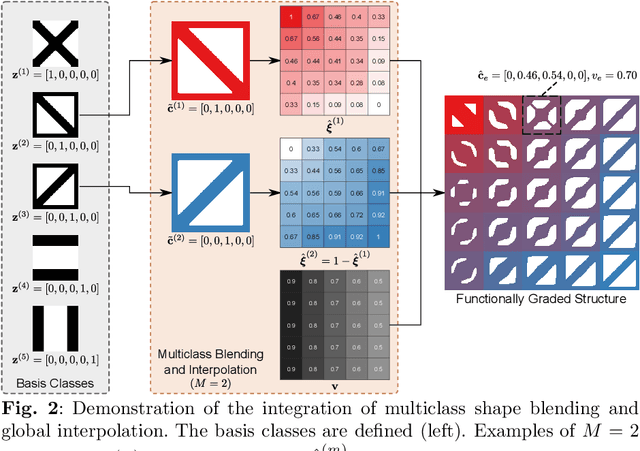
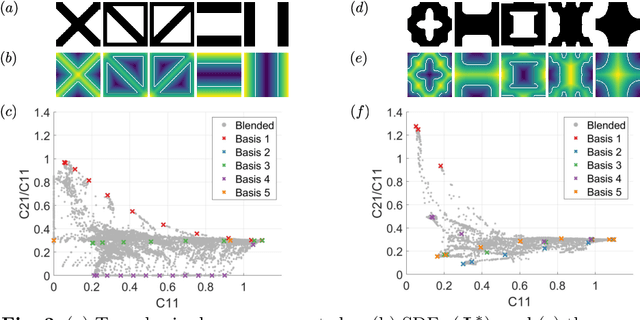
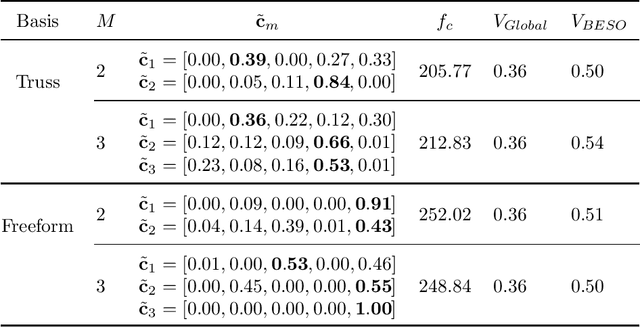
To create heterogeneous, multiscale structures with unprecedented functionalities, recent topology optimization approaches design either fully aperiodic systems or functionally graded structures, which compete in terms of design freedom and efficiency. We propose to inherit the advantages of both through a data-driven framework for multiclass functionally graded structures that mixes several families, i.e., classes, of microstructure topologies to create spatially-varying designs with guaranteed feasibility. The key is a new multiclass shape blending scheme that generates smoothly graded microstructures without requiring compatible classes or connectivity and feasibility constraints. Moreover, it transforms the microscale problem into an efficient, low-dimensional one without confining the design to predefined shapes. Compliance and shape matching examples using common truss geometries and diversity-based freeform topologies demonstrate the versatility of our framework, while studies on the effect of the number and diversity of classes illustrate the effectiveness. The generality of the proposed methods supports future extensions beyond the linear applications presented.
Bounding Queue Length Violation Probability of Joint Channel and Buffer Aware Transmission
Nov 23, 2021Lintao Li, Wei Chen, Khaled B. Letaief
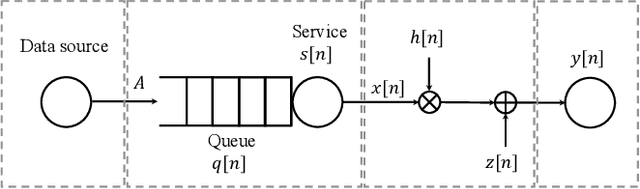
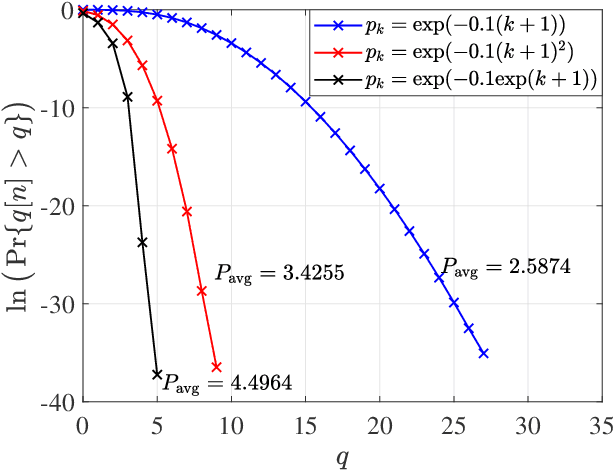
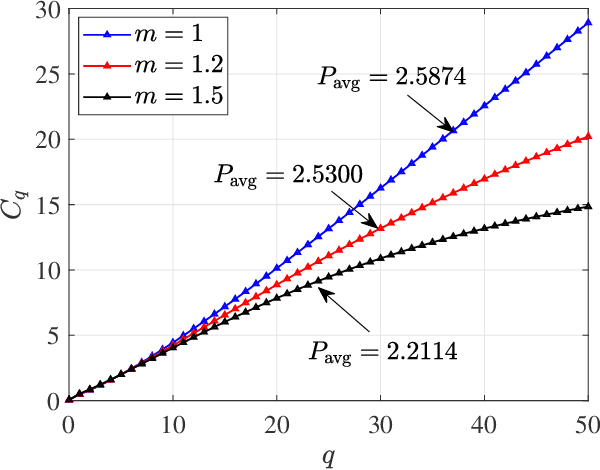
Queue length violation probability, i.e., the tail distribution of the queue length, is a widely used statistical quality-of-service (QoS) metric in wireless communications. Characterizing and optimizing the queue length violation probability have great significance in time sensitive networking (TSN) and ultra reliable and low-latency communications (URLLC). However, it still remains an open problem. In this paper, we put our focus on the analysis of the tail distribution of the queue length from the perspective of cross-layer design in wireless link transmission. We find that, under the finite average power consumption constraint, the queue length violation probability can achieve zero with diversity gains, while it can have a linear-decay-rate exponent according to large deviation theory (LDT) with limited receiver sensitivity. Besides, we find that the arbitrary-decay-rate queue length tail distribution with the finite average power consumption exists in the Rayleigh fading channel. Then, we generalize the sufficient conditions for the communication system belonging to these three scenarios, respectively. Moreover, we apply the above results to analyze the wireless link transmission in the Nakagami-m fading channel. Numerical results with approximation validate our analysis.
CCSL: A Causal Structure Learning Method from Multiple Unknown Environments
Nov 18, 2021Wei Chen, Yunjin Wu, Ruichu Cai, Yueguo Chen, Zhifeng Hao
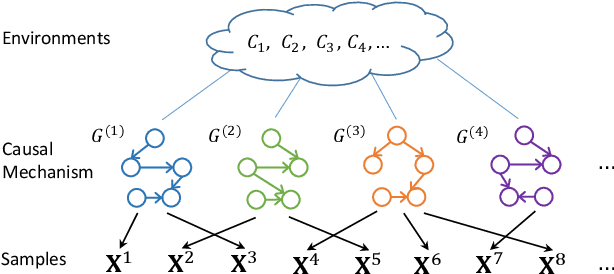
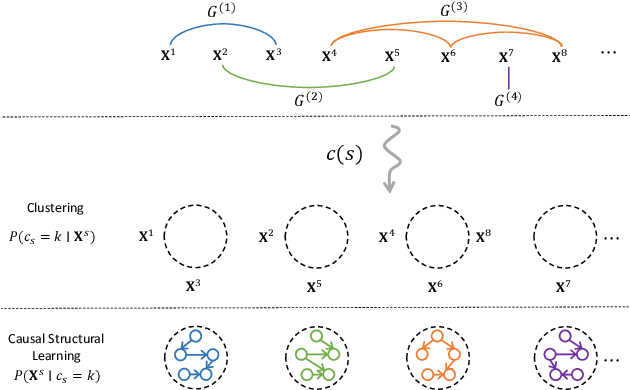
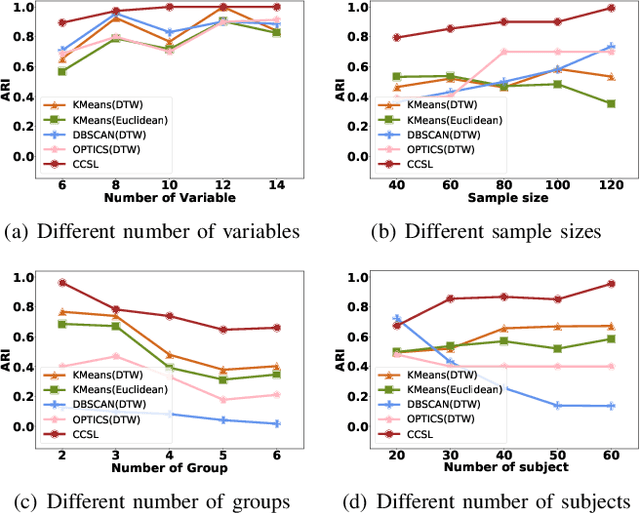
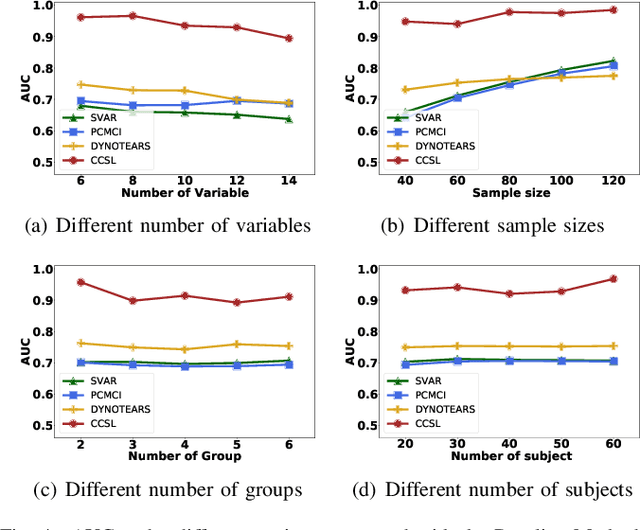
Most existing causal structure learning methods require data to be independent and identically distributed (i.i.d.), which often cannot be guaranteed when the data come from different environments. Some previous efforts try to tackle this problem in two independent stages, i.e., first discovering i.i.d. clusters from non-i.i.d. samples, then learning the causal structures from different groups. This straightforward solution ignores the intrinsic connections between the two stages, that is both the clustering stage and the learning stage should be guided by the same causal mechanism. Towards this end, we propose a unified Causal Cluster Structures Learning (named CCSL) method for causal discovery from non-i.i.d. data. This method simultaneously integrates the following two tasks: 1) clustering subjects with the same causal mechanism; 2) learning causal structures from the samples of subjects. Specifically, for the former, we provide a Causality-related Chinese Restaurant Process to cluster samples based on the similarity of the causal structure; for the latter, we introduce a variational-inference-based approach to learn the causal structures. Theoretical results provide identification of the causal model and the clustering model under the linear non-Gaussian assumption. Experimental results on both simulated and real-world data further validate the correctness and effectiveness of the proposed method.
Queue Length Violation Probability of Joint Channel and Buffer Aware Transmission
Nov 12, 2021Lintao Li, Wei Chen, Khaled B. Letaief



Queue length violation probability, i.e., the tail distribution of the queue length, is a widely used statistical quality-of-service (QoS) metric in wireless communications. Many previous works conducted tail distribution analysis on the control policies with the assumption that the condition of the large deviations theory (LDT) is satisfied. LDT indicates that the tail distribution of the queue length has a linear-decay-rate exponent. However, there are many control policies which do not meet that assumption, while the optimal control policy may be included in these policies. In this paper, we put our focus on the analysis of the tail distribution of the queue length from the perspective of cross-layer design in wireless link transmission. Specifically, we divide the wireless link transmission systems into three scenarios according to the decay rate of the queue-length tail distribution with the finite average power consumption. A heuristic policy is conceived to prove that the arbitrary-decay-rate tail distribution with the finite average power consumption exists in Rayleigh fading channels. Based on this heuristic policy, we generalize the analysis to Nakagami-m fading channels. Numerical results with approximation validate our analysis.
The Hardness Analysis of Thompson Sampling for Combinatorial Semi-bandits with Greedy Oracle
Nov 08, 2021Fang Kong, Yueran Yang, Wei Chen, Shuai Li
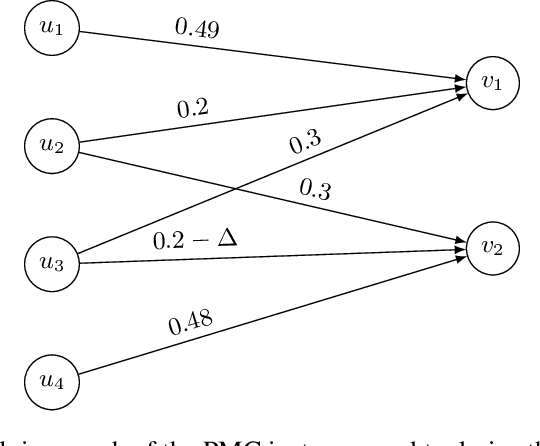
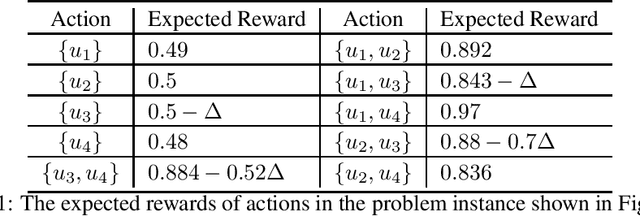
Thompson sampling (TS) has attracted a lot of interest in the bandit area. It was introduced in the 1930s but has not been theoretically proven until recent years. All of its analysis in the combinatorial multi-armed bandit (CMAB) setting requires an exact oracle to provide optimal solutions with any input. However, such an oracle is usually not feasible since many combinatorial optimization problems are NP-hard and only approximation oracles are available. An example (Wang and Chen, 2018) has shown the failure of TS to learn with an approximation oracle. However, this oracle is uncommon and is designed only for a specific problem instance. It is still an open question whether the convergence analysis of TS can be extended beyond the exact oracle in CMAB. In this paper, we study this question under the greedy oracle, which is a common (approximation) oracle with theoretical guarantees to solve many (offline) combinatorial optimization problems. We provide a problem-dependent regret lower bound of order $\Omega(\log T/\Delta^2)$ to quantify the hardness of TS to solve CMAB problems with greedy oracle, where $T$ is the time horizon and $\Delta$ is some reward gap. We also provide an almost matching regret upper bound. These are the first theoretical results for TS to solve CMAB with a common approximation oracle and break the misconception that TS cannot work with approximation oracles.
Mean-Field Approximation based Scheduling for Broadcast Channels with Massive Receivers
Nov 05, 2021Changkun Li, Wei Chen, Khaled B. Letaief
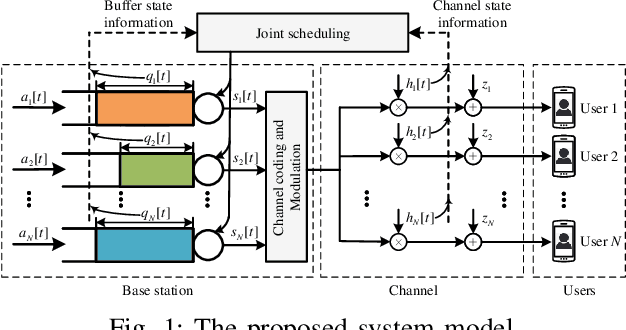
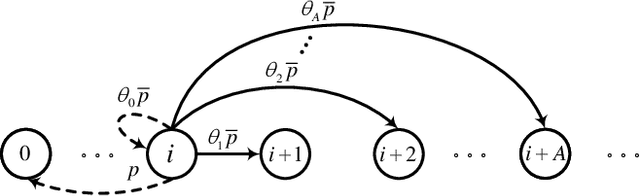
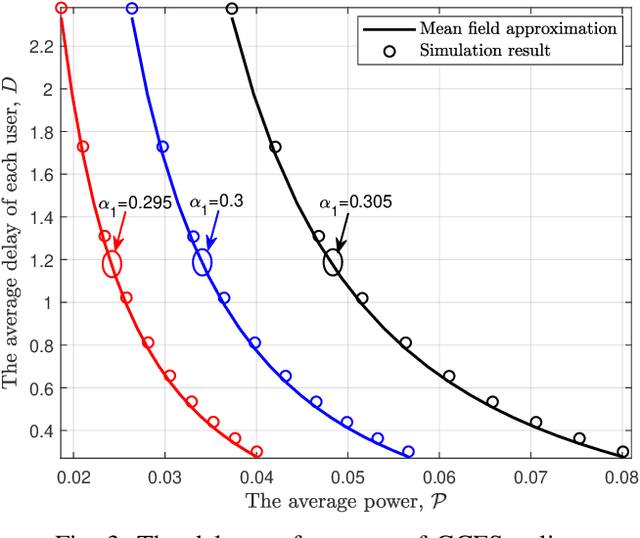
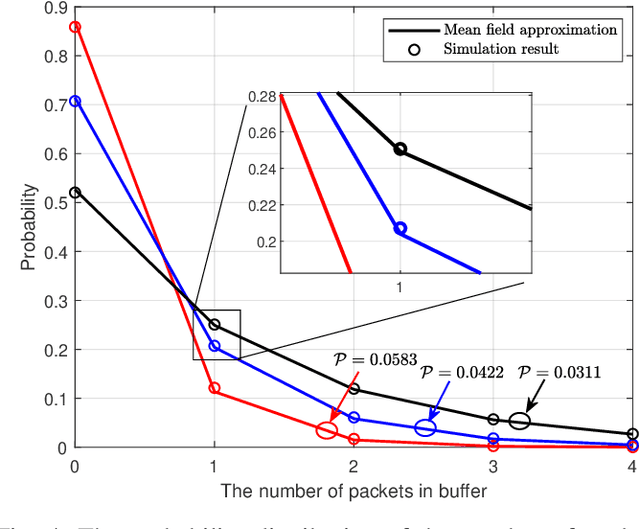
The emerging Industrial Internet of Things (IIoT) is driving an ever increasing demand for providing low latency services to massive devices over wireless channels. As a result, how to assure the quality-of-service (QoS) for a large amount of mobile users is becoming a challenging issue in the envisioned sixth-generation (6G) network. In such networks, the delay-optimal wireless access will require a joint channel and queue aware scheduling, whose complexity increases exponentially with the number of users. In this paper, we adopt the mean field approximation to conceive a buffer-aware multi-user diversity or opportunistic access protocol, which serves all backlogged packets of a user if its channel gain is beyond a threshold. A theoretical analysis and numerical results will demonstrate that not only the cross-layer scheduling policy is of low complexity but is also asymptotically optimal for a huge number of devices.
Optimizing Information-theoretical Generalization Bounds via Anisotropic Noise in SGLD
Nov 03, 2021Bohan Wang, Huishuai Zhang, Jieyu Zhang, Qi Meng, Wei Chen, Tie-Yan Liu
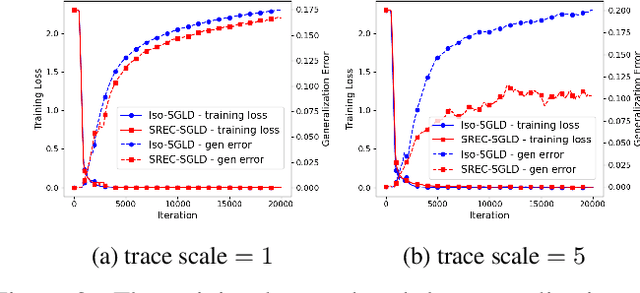
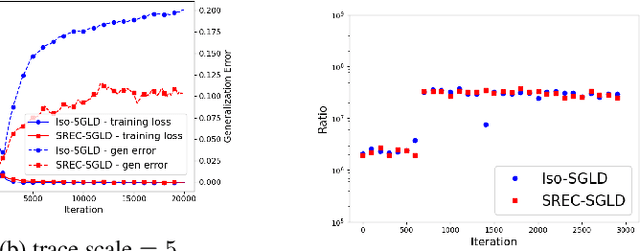
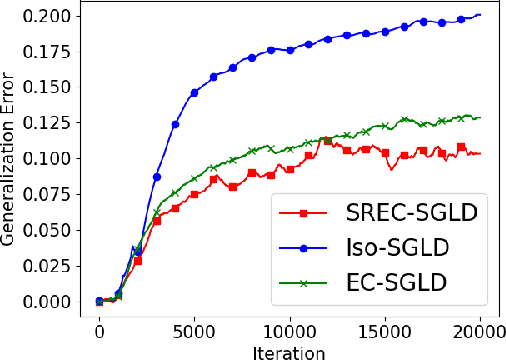
Recently, the information-theoretical framework has been proven to be able to obtain non-vacuous generalization bounds for large models trained by Stochastic Gradient Langevin Dynamics (SGLD) with isotropic noise. In this paper, we optimize the information-theoretical generalization bound by manipulating the noise structure in SGLD. We prove that with constraint to guarantee low empirical risk, the optimal noise covariance is the square root of the expected gradient covariance if both the prior and the posterior are jointly optimized. This validates that the optimal noise is quite close to the empirical gradient covariance. Technically, we develop a new information-theoretical bound that enables such an optimization analysis. We then apply matrix analysis to derive the form of optimal noise covariance. Presented constraint and results are validated by the empirical observations.
Indiscriminate Poisoning Attacks Are Shortcuts
Nov 01, 2021Da Yu, Huishuai Zhang, Wei Chen, Jian Yin, Tie-Yan Liu
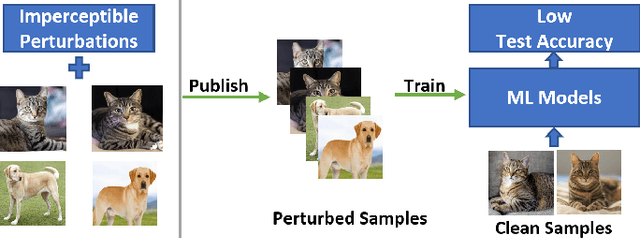
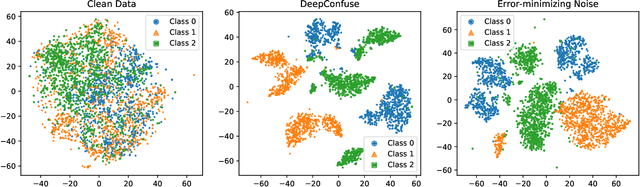
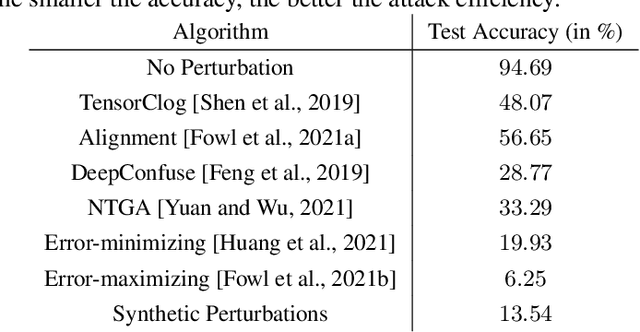

Indiscriminate data poisoning attacks, which add imperceptible perturbations to training data to maximize the test error of trained models, have become a trendy topic because they are thought to be capable of preventing unauthorized use of data. In this work, we investigate why these perturbations work in principle. We find that the perturbations of advanced poisoning attacks are almost \textbf{linear separable} when assigned with the target labels of the corresponding samples, which hence can work as \emph{shortcuts} for the learning objective. This important population property has not been unveiled before. Moreover, we further verify that linear separability is indeed the workhorse for poisoning attacks. We synthesize linear separable data as perturbations and show that such synthetic perturbations are as powerful as the deliberately crafted attacks. Our finding suggests that the \emph{shortcut learning} problem is more serious than previously believed as deep learning heavily relies on shortcuts even if they are of an imperceptible scale and mixed together with the normal features. This finding also suggests that pre-trained feature extractors would disable these poisoning attacks effectively.
Collaborative Pure Exploration in Kernel Bandit
Oct 29, 2021Yihan Du, Wei Chen, Yuko Yuroki, Longbo Huang
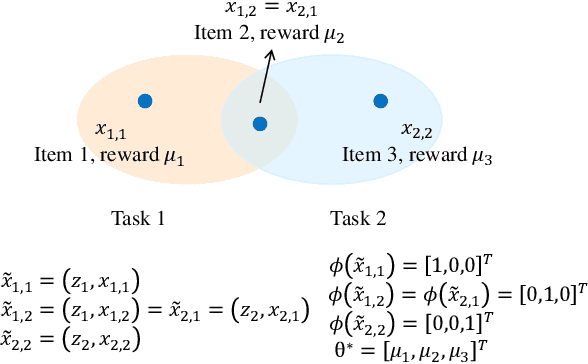
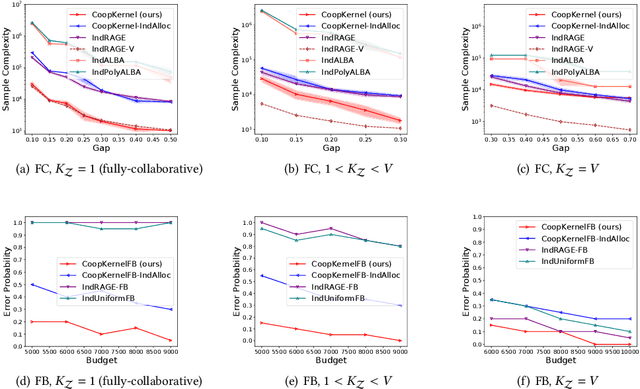
In this paper, we formulate a Collaborative Pure Exploration in Kernel Bandit problem (CoPE-KB), which provides a novel model for multi-agent multi-task decision making under limited communication and general reward functions, and is applicable to many online learning tasks, e.g., recommendation systems and network scheduling. We consider two settings of CoPE-KB, i.e., Fixed-Confidence (FC) and Fixed-Budget (FB), and design two optimal algorithms CoopKernelFC (for FC) and CoopKernelFB (for FB). Our algorithms are equipped with innovative and efficient kernelized estimators to simultaneously achieve computation and communication efficiency. Matching upper and lower bounds under both the statistical and communication metrics are established to demonstrate the optimality of our algorithms. The theoretical bounds successfully quantify the influences of task similarities on learning acceleration and only depend on the effective dimension of the kernelized feature space. Our analytical techniques, including data dimension decomposition, linear structured instance transformation and (communication) round-speedup induction, are novel and applicable to other bandit problems. Empirical evaluations are provided to validate our theoretical results and demonstrate the performance superiority of our algorithms.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge