A Comparison between Network-Controlled Repeaters and Reconfigurable Intelligent Surfaces
Nov 13, 2022Hao Guo, Charitha Madapatha, Behrooz Makki, Boris Dortschy, Lei Bao, Magnus Åström, Tommy Svensson
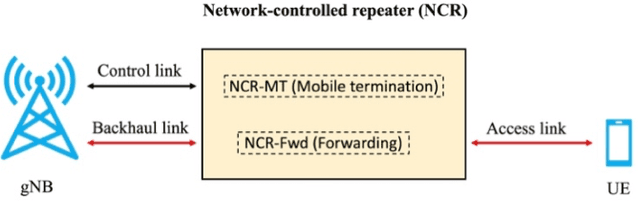
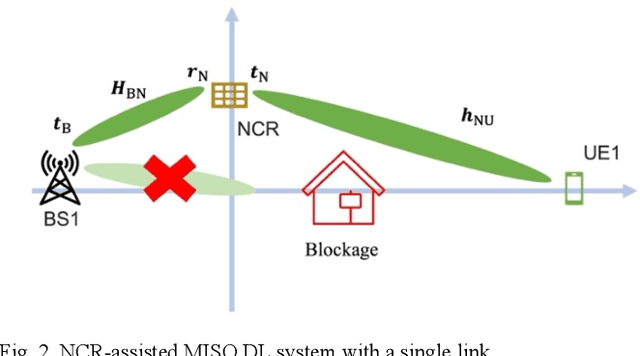
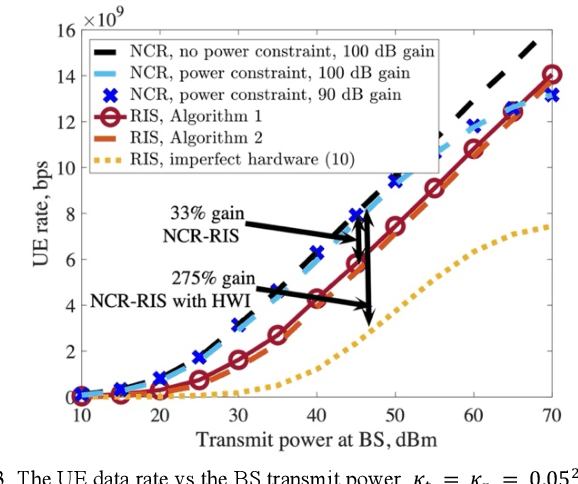
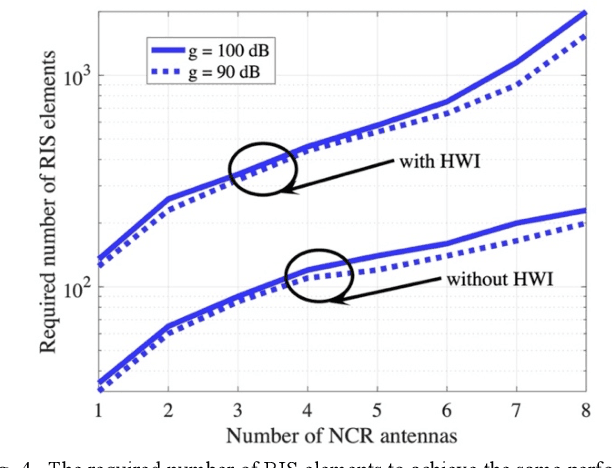
Network-controlled repeater (NCR) has been recently considered as a study-item in 3GPP Release 18, and the discussions are continuing in a work-item. In this paper, we introduce the concept of NCRs, as a possible low-complexity device to support for network densification and compare the performance of the NCRs with those achieved by reconfigurable intelligent surfaces (RISs). The results are presented for the cases with different beamforming methods and hardware impairment models of the RIS. Moreover, we introduce the objectives of the 3GPP Release 18 NCR work-item and study the effect of different parameters on the performance of NCR-assisted networks. As we show, with a proper deployment, the presence of NCRs/RISs can improve the network performance considerably.
NormSAGE: Multi-Lingual Multi-Cultural Norm Discovery from Conversations On-the-Fly
Oct 16, 2022Yi R. Fung, Tuhin Chakraborty, Hao Guo, Owen Rambow, Smaranda Muresan, Heng Ji
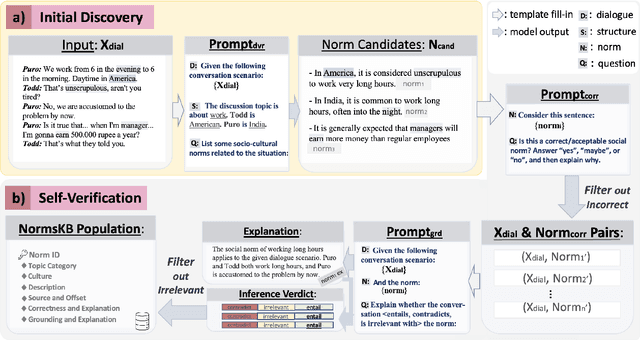
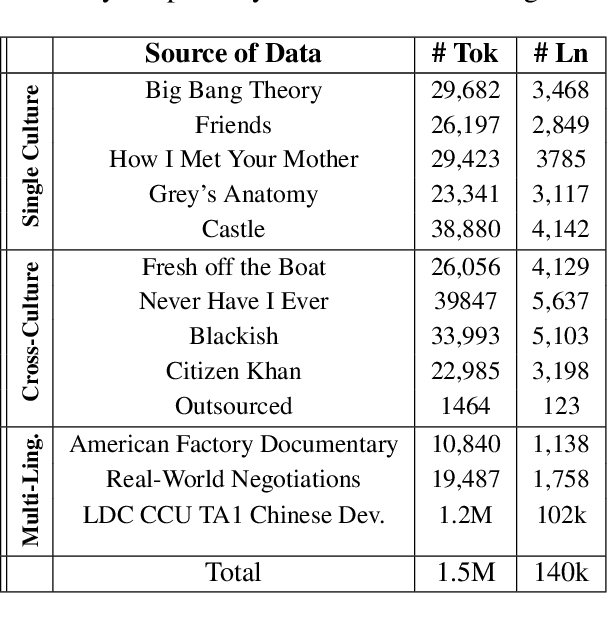
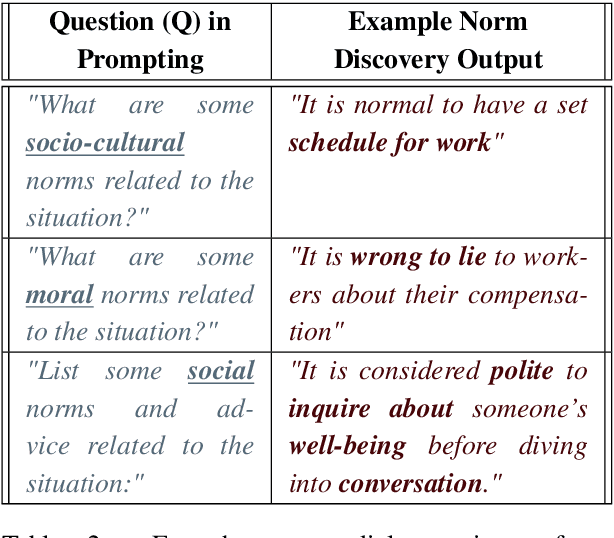
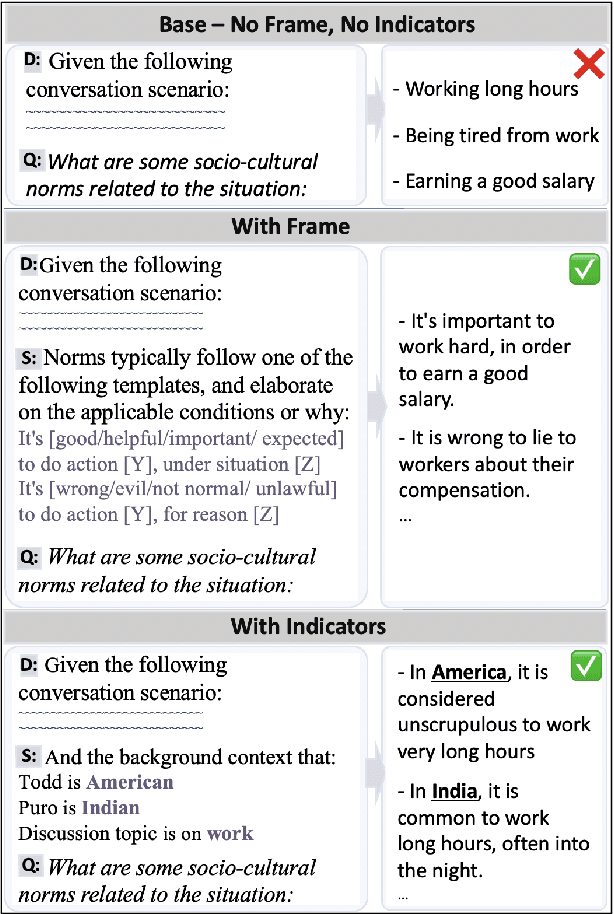
Norm discovery is important for understanding and reasoning about the acceptable behaviors and potential violations in human communication and interactions. We introduce NormSage, a framework for addressing the novel task of conversation-grounded multi-lingual, multi-cultural norm discovery, based on language model prompting and self-verification. NormSAGE leverages the expressiveness and implicit knowledge of the pretrained GPT-3 language model backbone, to elicit knowledge about norms through directed questions representing the norm discovery task and conversation context. It further addresses the risk of language model hallucination with a self-verification mechanism ensuring that the norms discovered are correct and are substantially grounded to their source conversations. Evaluation results show that our approach discovers significantly more relevant and insightful norms for conversations on-the-fly compared to baselines (>10+% in Likert scale rating). The norms discovered from Chinese conversation are also comparable to the norms discovered from English conversation in terms of insightfulness and correctness (<3% difference). In addition, the culture-specific norms are promising quality, allowing for 80% accuracy in culture pair human identification. Finally, our grounding process in norm discovery self-verification can be extended for instantiating the adherence and violation of any norm for a given conversation on-the-fly, with explainability and transparency. NormSAGE achieves an AUC of 95.4% in grounding, with natural language explanation matching human-written quality.
Constrained Deployment Optimization in Integrated Access and Backhaul Networks
Oct 11, 2022Charitha Madapatha, Behrooz Makki, Hao Guo, Tommy Svensson




Integrated access and backhaul (IAB) is one of the promising techniques for 5G networks and beyond (6G), in which the same node/hardware is used to provide both backhaul and cellular services in a multi-hop fashion. Due to the sensitivity of the backhaul links with high rate/reliability demands, proper network planning is needed to make the IAB network performing appropriately and as good as possible. In this paper, we study the effect of deployment optimization on the coverage of IAB networks. We concentrate on the cases where, due to either geographical or interference management limitations, unconstrained IAB node placement is not feasible in some areas. To that end, we propose various millimeter wave (mmWave) blocking-aware constrained deployment optimization approaches. Our results indicate that, even with limitations on deployment optimization, network planning boosts the coverage of IAB networks considerably.
Electromagnetic Field Exposure Avoidance thanks to Non-Intended User Equipment and RIS
Oct 07, 2022Hao Guo, Dinh-Thuy Phan-Huy, Tommy Svensson




On the one hand, there is a growing demand for high throughput which can be satisfied thanks to the deployment of new networks using massive multiple-input multiple-output (MIMO) and beamforming. On the other hand, in some countries or cities, there is a demand for arbitrarily low electromagnetic field exposure (EMFE) of people not concerned by the ongoing communication, which slows down the deployment of new networks. Recently, it has been proposed to take the opportunity, when designing the future 6th generation (6G), to offer, in addition to higher throughput, a new type of service: arbitrarily low EMFE. Recent works have shown that a reconfigurable intelligent surface (RIS), jointly optimized with the base station (BS) beamforming can improve the received throughput at the desired location whilst reducing EMFE everywhere. In this paper, we introduce a new concept of a non-intended user (NIU). An NIU is a user of the network who requests low EMFE when he/she is not downloading/uploading data. An NIU lets his/her device, called NIU equipment (NIUE), exchange some control signaling and pilots with the network, to help the network avoid exposing NIU to waves that are transporting data for another user of the network: the intended user (IU), whose device is called IU equipment (IUE). Specifically, we propose several new schemes to maximize the IU throughput under an EMFE constraint at the NIU (in practice, an interference constraint at the NIUE). Several propagation scenarios are investigated. Analytical and numerical results show that proper power allocation and beam optimization can remarkably boost the EMFE-constrained system's performance with limited complexity and channel information.
GReS: Graphical Cross-domain Recommendation for Supply Chain Platform
Sep 02, 2022Zhiwen Jing, Ziliang Zhao, Yang Feng, Xiaochen Ma, Nan Wu, Shengqiao Kang, Cheng Yang, Yujia Zhang, Hao Guo
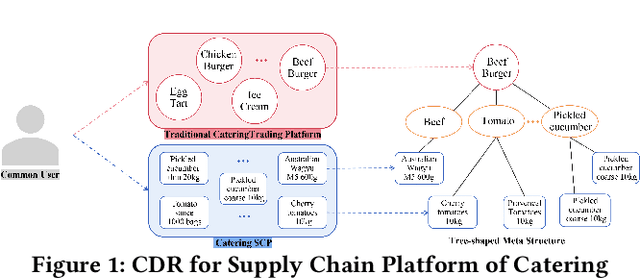
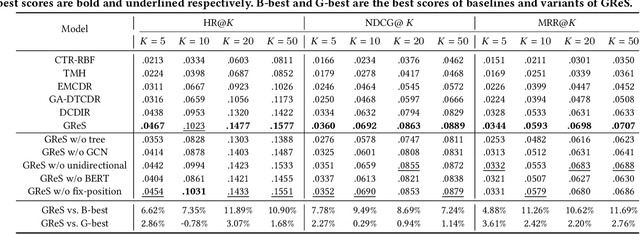
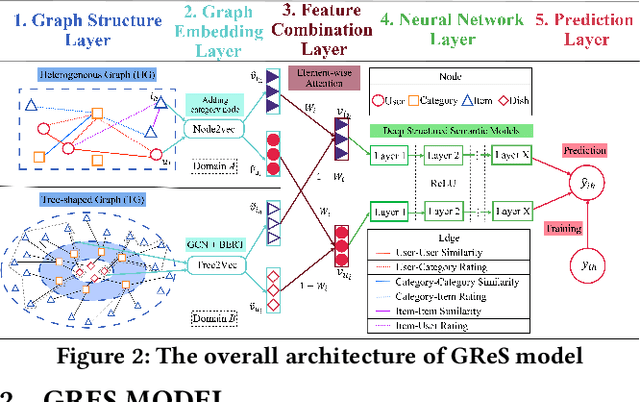
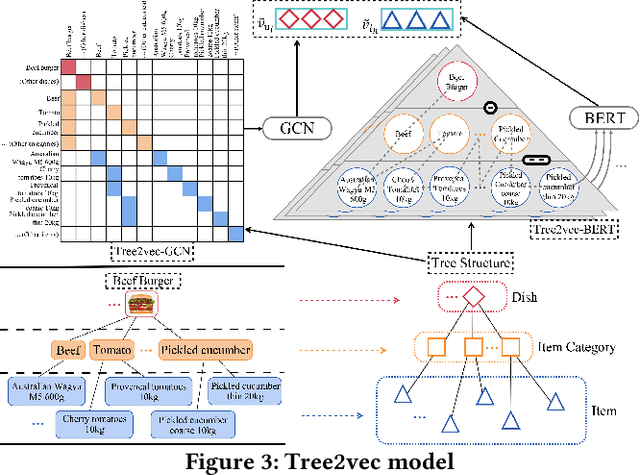
Supply Chain Platforms (SCPs) provide downstream industries with numerous raw materials. Compared with traditional e-commerce platforms, data in SCPs is more sparse due to limited user interests. To tackle the data sparsity problem, one can apply Cross-Domain Recommendation (CDR) which improves the recommendation performance of the target domain with the source domain information. However, applying CDR to SCPs directly ignores the hierarchical structure of commodities in SCPs, which reduce the recommendation performance. To leverage this feature, in this paper, we take the catering platform as an example and propose GReS, a graphical cross-domain recommendation model. The model first constructs a tree-shaped graph to represent the hierarchy of different nodes of dishes and ingredients, and then applies our proposed Tree2vec method combining GCN and BERT models to embed the graph for recommendations. Experimental results on a commercial dataset show that GReS significantly outperforms state-of-the-art methods in Cross-Domain Recommendation for Supply Chain Platforms.
Reinforcement Learning for Hardware Security: Opportunities, Developments, and Challenges
Aug 29, 2022Satwik Patnaik, Vasudev Gohil, Hao Guo, Jeyavijayan, Rajendran
Reinforcement learning (RL) is a machine learning paradigm where an autonomous agent learns to make an optimal sequence of decisions by interacting with the underlying environment. The promise demonstrated by RL-guided workflows in unraveling electronic design automation problems has encouraged hardware security researchers to utilize autonomous RL agents in solving domain-specific problems. From the perspective of hardware security, such autonomous agents are appealing as they can generate optimal actions in an unknown adversarial environment. On the other hand, the continued globalization of the integrated circuit supply chain has forced chip fabrication to off-shore, untrustworthy entities, leading to increased concerns about the security of the hardware. Furthermore, the unknown adversarial environment and increasing design complexity make it challenging for defenders to detect subtle modifications made by attackers (a.k.a. hardware Trojans). In this brief, we outline the development of RL agents in detecting hardware Trojans, one of the most challenging hardware security problems. Additionally, we outline potential opportunities and enlist the challenges of applying RL to solve hardware security problems.
ATTRITION: Attacking Static Hardware Trojan Detection Techniques Using Reinforcement Learning
Aug 26, 2022Vasudev Gohil, Hao Guo, Satwik Patnaik, Jeyavijayan, Rajendran
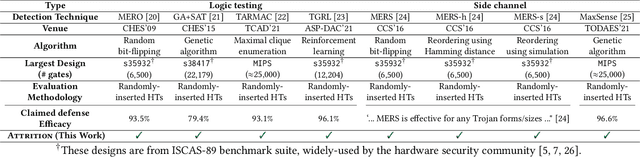
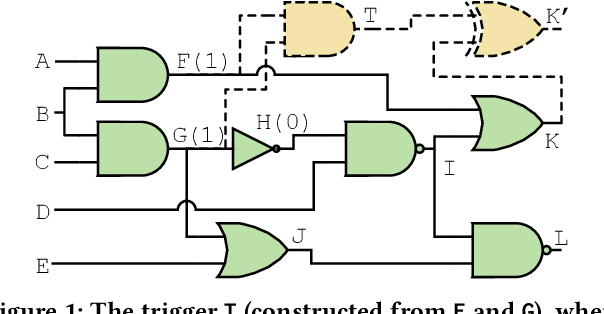
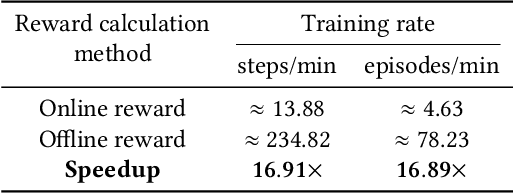
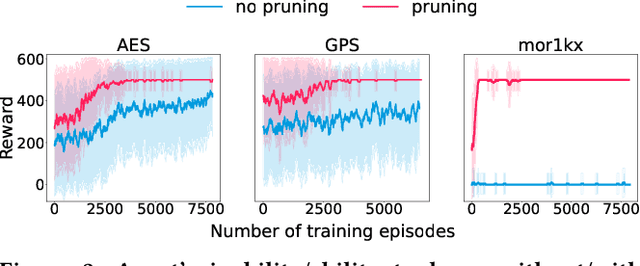
Stealthy hardware Trojans (HTs) inserted during the fabrication of integrated circuits can bypass the security of critical infrastructures. Although researchers have proposed many techniques to detect HTs, several limitations exist, including: (i) a low success rate, (ii) high algorithmic complexity, and (iii) a large number of test patterns. Furthermore, the most pertinent drawback of prior detection techniques stems from an incorrect evaluation methodology, i.e., they assume that an adversary inserts HTs randomly. Such inappropriate adversarial assumptions enable detection techniques to claim high HT detection accuracy, leading to a "false sense of security." Unfortunately, to the best of our knowledge, despite more than a decade of research on detecting HTs inserted during fabrication, there have been no concerted efforts to perform a systematic evaluation of HT detection techniques. In this paper, we play the role of a realistic adversary and question the efficacy of HT detection techniques by developing an automated, scalable, and practical attack framework, ATTRITION, using reinforcement learning (RL). ATTRITION evades eight detection techniques across two HT detection categories, showcasing its agnostic behavior. ATTRITION achieves average attack success rates of $47\times$ and $211\times$ compared to randomly inserted HTs against state-of-the-art HT detection techniques. We demonstrate ATTRITION's ability to evade detection techniques by evaluating designs ranging from the widely-used academic suites to larger designs such as the open-source MIPS and mor1kx processors to AES and a GPS module. Additionally, we showcase the impact of ATTRITION-generated HTs through two case studies (privilege escalation and kill switch) on the mor1kx processor. We envision that our work, along with our released HT benchmarks and models, fosters the development of better HT detection techniques.
DETERRENT: Detecting Trojans using Reinforcement Learning
Aug 26, 2022Vasudev Gohil, Satwik Patnaik, Hao Guo, Dileep Kalathil, Jeyavijayan, Rajendran
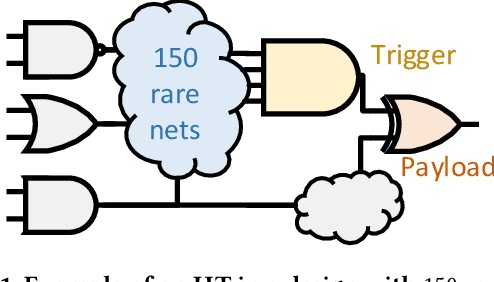
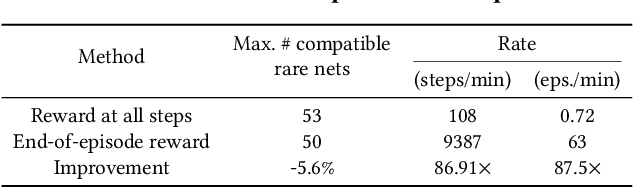
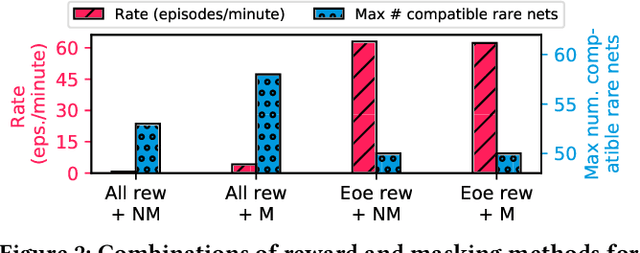
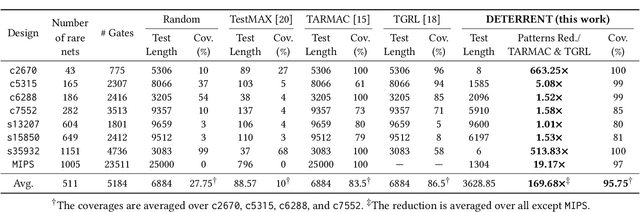
Insertion of hardware Trojans (HTs) in integrated circuits is a pernicious threat. Since HTs are activated under rare trigger conditions, detecting them using random logic simulations is infeasible. In this work, we design a reinforcement learning (RL) agent that circumvents the exponential search space and returns a minimal set of patterns that is most likely to detect HTs. Experimental results on a variety of benchmarks demonstrate the efficacy and scalability of our RL agent, which obtains a significant reduction ($169\times$) in the number of test patterns required while maintaining or improving coverage ($95.75\%$) compared to the state-of-the-art techniques.
A generalized regionalization framework for geographical modelling and its application in spatial regression
Jun 19, 2022Hao Guo, Andre Python, Yu Liu
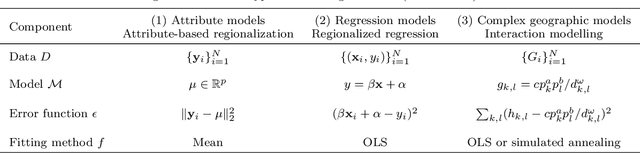
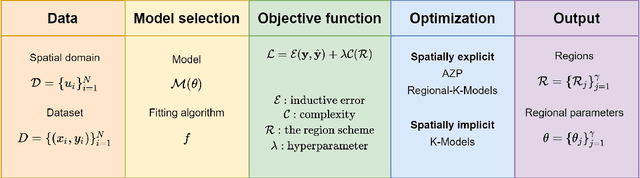
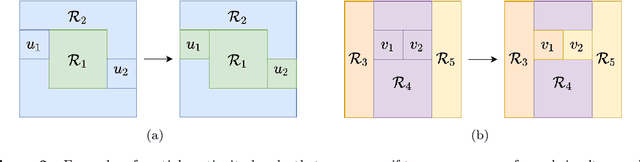
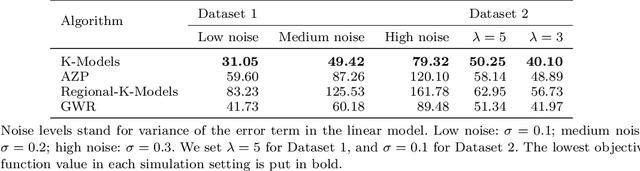
In presence of spatial heterogeneity, models applied to geographic data face a trade-off between producing general results and capturing local variations. Modelling at a regional scale may allow the identification of solutions that optimize both accuracy and generality. However, most current regionalization algorithms assume homogeneity in the attributes to delineate regions without considering the processes that generate the attributes. In this paper, we propose a generalized regionalization framework based on a two-item objective function which favors solutions with the highest overall accuracy while minimizing the number of regions. We introduce three regionalization algorithms, which extend previous methods that account for spatially constrained clustering. The effectiveness of the proposed framework is examined in regression experiments on both simulated and real data. The results show that a spatially implicit algorithm extended with an automatic post-processing procedure outperforms spatially explicit approaches. Our suggested framework contributes to better capturing the processes associated with spatial heterogeneity with potential applications in a wide range of geographical models.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge