Saif Al-Kuwari
Towards City-Scale Quantum Timing: Wireless Synchronization via Quantum Hubs
Dec 23, 2025
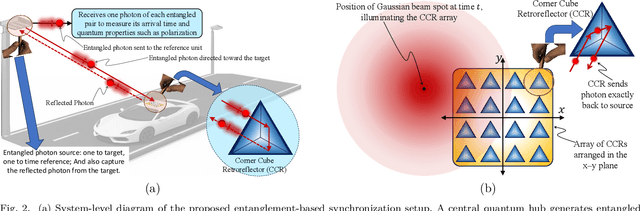
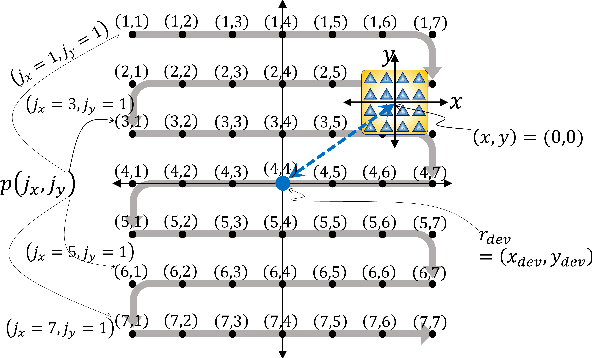
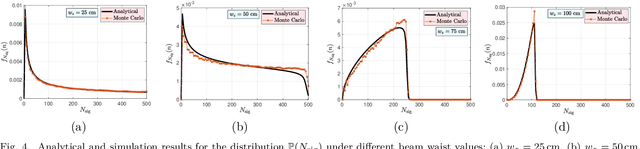
Abstract:This paper presents a novel wireless quantum synchronization framework tailored for city-scale deployment using entangled photon pairs and passive corner cube retroreflector (CCR) arrays. A centralized quantum hub emits entangled photons, directing one toward a target device and the other toward a local reference unit. The target, equipped with a planar CCR array, reflects the incoming photon without active circuitry, enabling secure round-trip quantum measurements for sub-nanosecond synchronization and localization. We develop a comprehensive analytical model that captures key physical-layer phenomena, including Gaussian beam spread, spatial misalignment, atmospheric turbulence, and probabilistic photon generation. A closed-form expression is derived for the single-photon detection probability under Gamma-Gamma fading, and its distribution is used to model photon arrival events and synchronization error. Moreover, we analyze the impact of background photons, SPAD detector jitter, and quantum generation randomness on synchronization accuracy and outage probability. Simulation results confirm the accuracy of the analytical models and reveal key trade-offs among beam waist, CCR array size, and background light. The proposed architecture offers a low-power, infrastructure-free solution for secure timing in next-generation smart cities.
CV Quantum Communications with Angular Rejection Filtering: Modeling and Security Analysis
Dec 19, 2025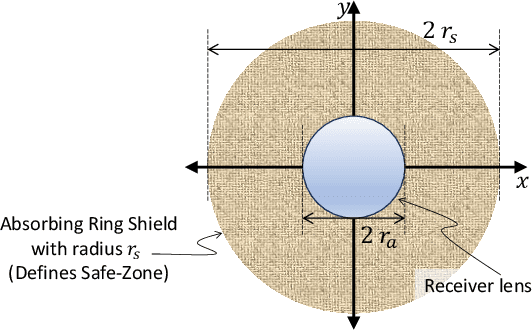
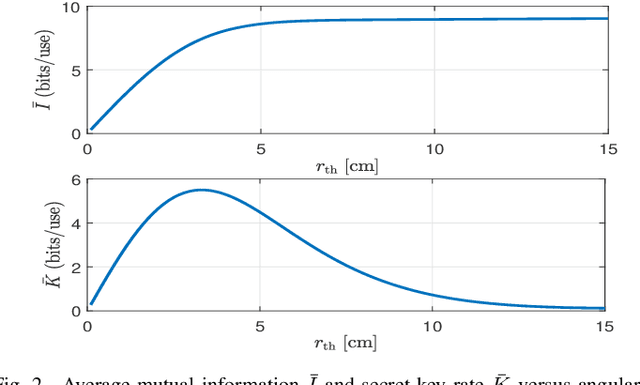
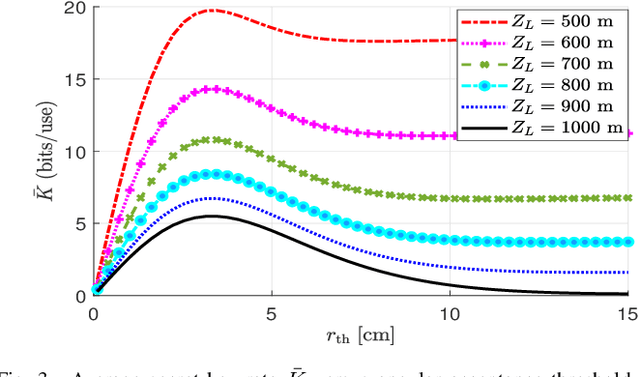
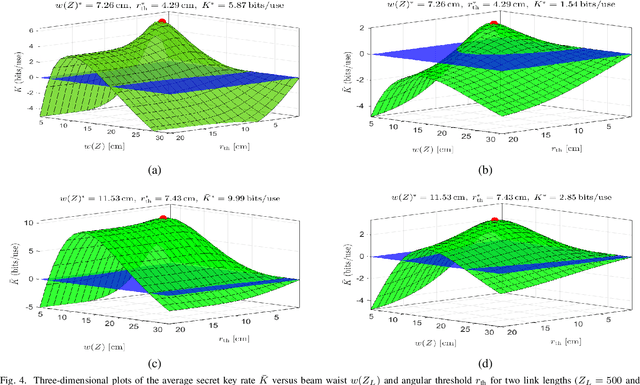
Abstract:Continuous-variable quantum key distribution (CVQKD) over free-space optical links is a promising approach for secure communication, but its performance is limited by turbulence, pointing errors, and angular leakage that can be exploited by an eavesdropper. To mitigate this, we consider an angular rejection filter that defines a safe-zone at the receiver and blocks signals from outside the desired cone. A system and channel model is developed including turbulence, misalignment, and safe-zone effects, and information theoretic metrics are derived to evaluate security. Simulation results show that the safe zone significantly reduces information leakage and that careful tuning of beam waist, angular threshold, and aperture size is essential for maximizing the secret key rate. Larger apertures improve performance but increase receiver size, while longer links require sub 100 urad alignment accuracy. These results highlight safe-zone enforcement and parameter optimization as effective strategies for practical and secure CV-QKD.
Physical Limits of Entanglement-Based Quantum Key Distribution over Long-Distance Satellite Links
Jun 25, 2025Abstract:Entanglement-based quantum key distribution (QKD) protocols, such as E91 and BBM92, offer strong information-theoretic security and are naturally suited for satellite-to-satellite QKD (SatQKD) links. However, implementing these protocols over long-distance inter-satellite free-space optical (FSO) channels poses critical physical-layer challenges that are not addressed in the existing literature. In particular, photon losses due to beam divergence, pointing errors, and background noise can severely degrade the key generation rate and quantum bit error rate (QBER), especially under narrow receiver field-of-view (FoV) constraints. This paper presents a comprehensive performance analysis of entanglement-based inter-satellite QKD, focusing on photon-level modeling and the impact of practical impairments. We develop analytical expressions for signal detection probabilities, background photon influence, multi-pair emissions, and QBER, incorporating key parameters such as link distance, transmitter tracking jitter, receiver misalignment, and photon pair generation rate. Simulation results reveal the nonlinear sensitivity of system performance to tracking error and FoV limitations, and highlight optimal parameter regimes that jointly maximize secret key rate while maintaining QBER below acceptable thresholds. The proposed model provides actionable design insights for reliable and efficient deployment of entanglement-based SatQKD systems.
QSVM-QNN: Quantum Support Vector Machine Based Quantum Neural Network Learning Algorithm for Brain-Computer Interfacing Systems
May 20, 2025Abstract:A brain-computer interface (BCI) system enables direct communication between the brain and external devices, offering significant potential for assistive technologies and advanced human-computer interaction. Despite progress, BCI systems face persistent challenges, including signal variability, classification inefficiency, and difficulty adapting to individual users in real time. In this study, we propose a novel hybrid quantum learning model, termed QSVM-QNN, which integrates a Quantum Support Vector Machine (QSVM) with a Quantum Neural Network (QNN), to improve classification accuracy and robustness in EEG-based BCI tasks. Unlike existing models, QSVM-QNN combines the decision boundary capabilities of QSVM with the expressive learning power of QNN, leading to superior generalization performance. The proposed model is evaluated on two benchmark EEG datasets, achieving high accuracies of 0.990 and 0.950, outperforming both classical and standalone quantum models. To demonstrate real-world viability, we further validated the robustness of QNN, QSVM, and QSVM-QNN against six realistic quantum noise models, including bit flip and phase damping. These experiments reveal that QSVM-QNN maintains stable performance under noisy conditions, establishing its applicability for deployment in practical, noisy quantum environments. Beyond BCI, the proposed hybrid quantum architecture is generalizable to other biomedical and time-series classification tasks, offering a scalable and noise-resilient solution for next-generation neurotechnological systems.
QFDNN: A Resource-Efficient Variational Quantum Feature Deep Neural Networks for Fraud Detection and Loan Prediction
Apr 28, 2025



Abstract:Social financial technology focuses on trust, sustainability, and social responsibility, which require advanced technologies to address complex financial tasks in the digital era. With the rapid growth in online transactions, automating credit card fraud detection and loan eligibility prediction has become increasingly challenging. Classical machine learning (ML) models have been used to solve these challenges; however, these approaches often encounter scalability, overfitting, and high computational costs due to complexity and high-dimensional financial data. Quantum computing (QC) and quantum machine learning (QML) provide a promising solution to efficiently processing high-dimensional datasets and enabling real-time identification of subtle fraud patterns. However, existing quantum algorithms lack robustness in noisy environments and fail to optimize performance with reduced feature sets. To address these limitations, we propose a quantum feature deep neural network (QFDNN), a novel, resource efficient, and noise-resilient quantum model that optimizes feature representation while requiring fewer qubits and simpler variational circuits. The model is evaluated using credit card fraud detection and loan eligibility prediction datasets, achieving competitive accuracies of 82.2% and 74.4%, respectively, with reduced computational overhead. Furthermore, we test QFDNN against six noise models, demonstrating its robustness across various error conditions. Our findings highlight QFDNN potential to enhance trust and security in social financial technology by accurately detecting fraudulent transactions while supporting sustainability through its resource-efficient design and minimal computational overhead.
Benchmarking Online Object Trackers for Underwater Robot Position Locking Applications
Feb 23, 2025



Abstract:Autonomously controlling the position of Remotely Operated underwater Vehicles (ROVs) is of crucial importance for a wide range of underwater engineering applications, such as in the inspection and maintenance of underwater industrial structures. Consequently, studying vision-based underwater robot navigation and control has recently gained increasing attention to counter the numerous challenges faced in underwater conditions, such as lighting variability, turbidity, camera image distortions (due to bubbles), and ROV positional disturbances (due to underwater currents). In this paper, we propose (to the best of our knowledge) a first rigorous unified benchmarking of more than seven Machine Learning (ML)-based one-shot object tracking algorithms for vision-based position locking of ROV platforms. We propose a position-locking system that processes images of an object of interest in front of which the ROV must be kept stable. Then, our proposed system uses the output result of different object tracking algorithms to automatically correct the position of the ROV against external disturbances. We conducted numerous real-world experiments using a BlueROV2 platform within an indoor pool and provided clear demonstrations of the strengths and weaknesses of each tracking approach. Finally, to help alleviate the scarcity of underwater ROV data, we release our acquired data base as open-source with the hope of benefiting future research.
SentiQNF: A Novel Approach to Sentiment Analysis Using Quantum Algorithms and Neuro-Fuzzy Systems
Dec 17, 2024



Abstract:Sentiment analysis is an essential component of natural language processing, used to analyze sentiments, attitudes, and emotional tones in various contexts. It provides valuable insights into public opinion, customer feedback, and user experiences. Researchers have developed various classical machine learning and neuro-fuzzy approaches to address the exponential growth of data and the complexity of language structures in sentiment analysis. However, these approaches often fail to determine the optimal number of clusters, interpret results accurately, handle noise or outliers efficiently, and scale effectively to high-dimensional data. Additionally, they are frequently insensitive to input variations. In this paper, we propose a novel hybrid approach for sentiment analysis called the Quantum Fuzzy Neural Network (QFNN), which leverages quantum properties and incorporates a fuzzy layer to overcome the limitations of classical sentiment analysis algorithms. In this study, we test the proposed approach on two Twitter datasets: the Coronavirus Tweets Dataset (CVTD) and the General Sentimental Tweets Dataset (GSTD), and compare it with classical and hybrid algorithms. The results demonstrate that QFNN outperforms all classical, quantum, and hybrid algorithms, achieving 100% and 90% accuracy in the case of CVTD and GSTD, respectively. Furthermore, QFNN demonstrates its robustness against six different noise models, providing the potential to tackle the computational complexity associated with sentiment analysis on a large scale in a noisy environment. The proposed approach expedites sentiment data processing and precisely analyses different forms of textual data, thereby enhancing sentiment classification and insights associated with sentiment analysis.
Performance Analysis of Underwater Acoustic Channel Amid Jamming by Random Jammers
May 05, 2024



Abstract:Underwater communication networks are increasingly popularized by various important maritime applications. However, this also leads to an increased threat landscape. This letter presents the first study that considers jamming attacks by random jammers present in the surroundings of legitimate transceivers in underwater acoustic communication systems. We investigate the impact of jamming attacks on various performance parameters of the legitimate underwater acoustic communication link. In particular, we investigate the legitimate link using stochastic geometry for important performance parameters, namely coverage probability, average rate, and energy efficiency of the link between two legitimate nodes, i.e., underwater and surface nodes. We then derive and present tractable expressions for these performance parameters. Finally, we performed a Monte Carlo simulation to validate our analysis. We plot the performance metrics against the transmit power, and jamming power for different intensities of the jammers in shallow, mid, and deep water scenarios. Results reveal that on average, jamming in deep water has a relatively high impact on the performance of legitimate link than in shallow water.
On the Potential of Re-configurable Intelligent Surface (RIS)-assisted Physical Layer Authentication (PLA)
May 02, 2024Abstract:Re-configurable Intelligent Surfaces (RIS) technology is increasingly becoming a potential component for next-generation wireless networks, offering enhanced performance in terms of throughput, spectral, and energy efficiency. However, the broadcast nature of RIS-assisted wireless communication makes it vulnerable to malicious attacks at the physical layer. At the same time, physical layer authentication is gaining popularity as a solution to secure wireless networks, thwarting different attacks such as cloning, spoofing, and impersonation by using the random features of the physical layer. In this paper, we investigate RIS-assisted wireless communication systems to unlock the potential of using RIS for physical layer authentication (PLA). In particular, we exploit two distinct features of the physical layer: pathloss and channel impulse response (CIR) for PLA in RIS-assisted wireless communication. We construct hypothesis tests for the estimated features and derive closed-form error expressions. Further, we consider the critical error, i.e., missed detection, as our objective function to minimize by optimizing the phase shift of the RIS pannel. We compare the performance of our proposed mechanisms with PLA schemes using the same features but with no RIS. Furthermore, we thoroughly evaluate our proposed schemes using performance metrics such as the probability of false alarm (PFA), the probability of missed detection (PMD), and the receiver operating characteristic (ROC) curves. The results demonstrate a clear positive impact of RIS on PLA, as it effectively reduces PMD values to zero when determining the optimal phase shift.
Hybrid PLS-ML Authentication Scheme for V2I Communication Networks
Aug 28, 2023



Abstract:Vehicular communication networks are rapidly emerging as vehicles become smarter. However, these networks are increasingly susceptible to various attacks. The situation is exacerbated by the rise in automated vehicles complicates, emphasizing the need for security and authentication measures to ensure safe and effective traffic management. In this paper, we propose a novel hybrid physical layer security (PLS)-machine learning (ML) authentication scheme by exploiting the position of the transmitter vehicle as a device fingerprint. We use a time-of-arrival (ToA) based localization mechanism where the ToA is estimated at roadside units (RSUs), and the coordinates of the transmitter vehicle are extracted at the base station (BS).Furthermore, to track the mobility of the moving legitimate vehicle, we use ML model trained on several system parameters. We try two ML models for this purpose, i.e., support vector regression and decision tree. To evaluate our scheme, we conduct binary hypothesis testing on the estimated positions with the help of the ground truths provided by the ML model, which classifies the transmitter node as legitimate or malicious. Moreover, we consider the probability of false alarm and the probability of missed detection as performance metrics resulting from the binary hypothesis testing, and mean absolute error (MAE), mean square error (MSE), and coefficient of determination $\text{R}^2$ to further evaluate the ML models. We also compare our scheme with a baseline scheme that exploits the angle of arrival at RSUs for authentication. We observe that our proposed position-based mechanism outperforms the baseline scheme significantly in terms of missed detections.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge