Zhen Ma
Active RIS-Aided Anti-Jamming Wireless Communications: A Stackelberg Game Perspective
Dec 19, 2025Abstract:The pervasive threat of jamming attacks, particularly from adaptive jammers capable of optimizing their strategies, poses a significant challenge to the security and reliability of wireless communications. This paper addresses this issue by investigating anti-jamming communications empowered by an active reconfigurable intelligent surface. The strategic interaction between the legitimate system and the adaptive jammer is modeled as a Stackelberg game, where the legitimate user, acting as the leader, proactively designs its strategy while anticipating the jammer's optimal response. We prove the existence of the Stackelberg equilibrium and derive it using a backward induction method. Particularly, the jammer's optimal strategy is embedded into the leader's problem, resulting in a bi-level optimization that jointly considers legitimate transmit power, transmit/receive beamformers, and active reflection. We tackle this complex, non-convex problem by using a block coordinate descent framework, wherein subproblems are iteratively solved via convex relaxation and successive convex approximation techniques. Simulation results demonstrate the significant superiority of the proposed active RIS-assisted scheme in enhancing legitimate transmissions and degrading jamming effects compared to baseline schemes across various scenarios. These findings highlight the effectiveness of combining active RIS technology with a strategic game-theoretic framework for anti-jamming communications.
Inversion of biological strategies in engineering technology: in case underwater soft robot
Apr 16, 2025Abstract:This paper proposes a biomimetic design framework based on biological strategy inversion, aiming to systematically map solutions evolved in nature to the engineering field. By constructing a "Function-Behavior-Feature-Environment" (F-B-Cs in E) knowledge model, combined with natural language processing (NLP) and multi-criteria decision-making methods, it achieves efficient conversion from biological strategies to engineering solutions. Using underwater soft robot design as a case study, the effectiveness of the framework in optimizing drive mechanisms, power distribution, and motion pattern design is verified. This research provides scalable methodological support for interdisciplinary biomimetic innovation.
Improved ICNN-LSTM Model Classification Based on Attitude Sensor Data for Hazardous State Assessment of Magnetic Adhesion Climbing Wall Robots
Dec 30, 2024



Abstract:Magnetic adhesion tracked climbing robots are widely utilized in high-altitude inspection, welding, and cleaning tasks due to their ability to perform various operations against gravity on vertical or inclined walls. However, during operation, the robot may experience overturning torque caused by its own weight and load, which can lead to the detachment of magnetic plates and subsequently pose safety risks. This paper proposes an improved ICNN-LSTM network classification method based on Micro-Electro-Mechanical Systems (MEMS) attitude sensor data for real-time monitoring and assessment of hazardous states in magnetic adhesion tracked climbing robots. Firstly, a data acquisition strategy for attitude sensors capable of capturing minute vibrations is designed. Secondly, a feature extraction and classification model combining an Improved Convolutional Neural Network (ICNN) with a Long Short-Term Memory (LSTM) network is proposed. Experimental validation demonstrates that the proposed minute vibration sensing method achieves significant results, and the proposed classification model consistently exhibits high accuracy compared to other models. The research findings provide effective technical support for the safe operation of climbing robots
Augmented Reality on the Large Scene Based on a Markerless Registration Framework
Mar 07, 2020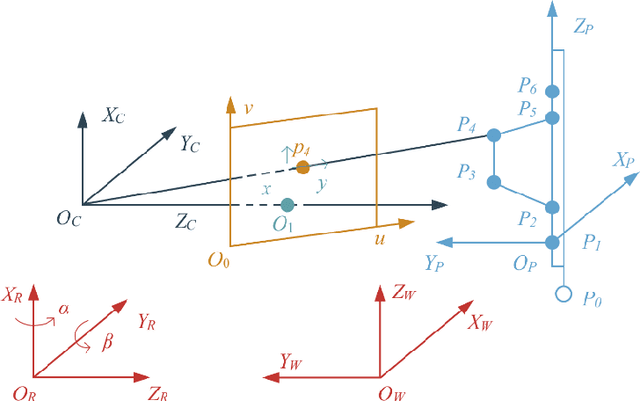
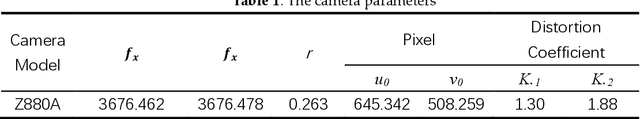
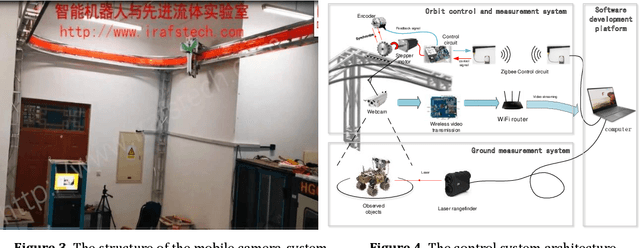
Abstract:In this paper, a mobile camera positioning method based on forward and inverse kinematics of robot is proposed, which can realize far point positioning of imaging position and attitude tracking in large scene enhancement. Orbit precision motion through the framework overhead cameras and combining with the ground system of sensor array object such as mobile robot platform of various sensors, realize the good 3 d image registration, solve any artifacts that is mobile robot in the large space position initialization problem, effectively implement the large space no marks augmented reality, human-computer interaction, and information summary. Finally, the feasibility and effectiveness of the method are verified by experiments.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge