Steven Rivetti
On the Impact of Channel Aging and Doppler-Affected Clutter on OFDM ISAC Systems
Jan 08, 2026Abstract:The temporal evolution of the propagation environment plays a central role in integrated sensing and communication (ISAC) systems. A slow-time evolution manifests as channel aging in communication links, while a fast-time one is associated with structured clutter with non-zero Doppler. Nevertheless, the joint impact of these two phenomena on ISAC performance has been largely overlooked. This addresses this research gap in a network utilizing orthogonal frequency division multiplexing waveforms. Here, a base station simultaneously serves multiple user equipment (UE) devices and performs monostatic sensing. Channel aging is captured through an autoregressive model with exponential correlation decay. In contrast, clutter is modeled as a collection of uncorrelated, coherent patches with non-zero Doppler, resulting in a Kronecker-separable covariance structure. We propose an aging-aware channel estimator that uses prior pilot observations to estimate the time-varying UE channels, characterized by a non-isotropic multipath fading structure. The clutter's structure enables a novel low-complexity sensing pipeline: clutter statistics are estimated from raw data and subsequently used to suppress the clutter's action, after which target parameters are extracted through range-angle and range-velocity maps. We evaluate the influence of frame length and pilot history on channel estimation accuracy and demonstrate substantial performance gains over block fading in low-to-moderate mobility regimes. The sensing pipeline is implemented in a clutter-dominated environment, demonstrating that effective clutter suppression can be achieved under practical configurations. Furthermore, our results show that dedicated sensing streams are required, as communication beams provide insufficient range resolution.
Millimeter-Wave Joint Radar and Communications With an RIS-Integrated Array
Apr 13, 2025Abstract:In the context of the joint radar and communications (JRC) framework, reconfigurable intelligent surfaces (RISs) emerged as a promising technology for their ability to shape the propagation environment by adjusting their phase-shift coefficients. However, achieving perfect synchronization and effective collaboration between access points (APs) and RISs is crucial to successful operation. This paper investigates the performance of a bistatic JRC network operating in the millimeter-wave (mmWave) frequency band, where the receiving AP is equipped with an RIS-integrated array. This system simultaneously serves multiple UEs while estimating the position of a target with limited prior knowledge of its position. To achieve this, we optimize both the power allocation of the transmitted waveform and the RIS phase-shift matrix to minimize the position error bound (PEB) of the target. At the same time, we ensure that the UEs achieve an acceptable level of spectral efficiency. The numerical results show that an RIS-integrated array, even with a small number of receiving antennas, can achieve high localization accuracy. Additionally, optimized phase-shifts significantly improve the localization accuracy in comparison to a random phase-shift configuration.
Clutter-Aware Target Detection for ISAC in a Millimeter-Wave Cell-Free Massive MIMO System
Nov 13, 2024



Abstract:In this paper, we investigate the performance of an integrated sensing and communication (ISAC) system within a cell-free massive multiple-input multiple-output (MIMO) system. Each access point (AP) operates in the millimeter-wave (mmWave) frequency band. The APs jointly serve the user equipments (UEs) in the downlink while simultaneously detecting a target through dedicated sensing beams, which are directed toward a reconfigurable intelligent surface (RIS). Although the AP-RIS, RIS-target, and AP-target channels have both line-of-sight (LoS) and non-line-of-sight (NLoS) parts, it is assumed only knowledge of the LoS paths is available. A key contribution of this study is the consideration of clutter, which degrades the target detection if not handled. We propose an algorithm to alternatively optimize the transmit power allocation and the RIS phase-shift matrix, maximizing the target signal-to-clutter-plus-noise ratio (SCNR) while ensuring a minimum signal-to-interference-plus-noise ratio (SINR) for the UEs. Numerical results demonstrate that exploiting clutter subspace significantly enhances detection probability, particularly at high clutter-to-noise ratios, and reveal that an increased number of transmit side clusters impair detection performance. Finally, we highlight the performance gains achieved using a dedicated sensing stream.
Destructive and constructive RIS beamforming in an ISAC-multi-user MIMO network
Apr 17, 2024



Abstract:Integrated sensing and communication (ISAC) has already established itself as a promising solution to the spectrum scarcity problem, even more so when paired with a reconfigurable intelligent surface (RIS) as RISs can shape the propagation environment by adjusting their phase-shift coefficients. Albeit the potential performance gain, a RIS also poses a security threat to the system: in this paper, we explore both sides of the RIS presence in a multi-user MIMO (multiple-input multiple-output) ISAC network. We first develop an alternating optimization algorithm, obtaining the active and passive beamforming vectors maximizing the sensing signal-to-noise ratio (SNR) under minimum signal-to-interference-plus-noise ratio (SINR) constraints for the communication users and finite power budget. We also investigate the destructive potential of RIS by devising a RIS phase-shift optimization algorithm that minimizes sensing SNR while preserving the same minimum communication SINR previously guaranteed by the system. We further investigate the impact of the RIS's individual element failures on the system performances. The simulation results show that the RIS performance-boosting potential is as good as its destructive one and that both of our optimization strategies show some resilience towards the investigated impairments.
Malicious Reconfigurable Intelligent Surfaces: How Impactful can Destructive Beamforming be?
Feb 20, 2024


Abstract:Reconfigurable intelligent surfaces (RISs) have demonstrated significant potential for enhancing communication system performance if properly configured. However, a RIS might also pose a risk to the network security. In this letter, we explore the impact of a malicious RIS on a multi-user multiple-input single-output (MISO) system when the system is unaware of the RIS's malicious intentions. The objective of the malicious RIS is to degrade the \ac{SNR} of a specific \ac{UE}, with the option of preserving the SNR of the other UEs, making the attack harder to detect. To achieve this goal, we derive the optimal RIS phase-shift pattern, assuming perfect channel state information (CSI) at the hacker. We then relax this assumption by introducing CSI uncertainties and subsequently determine the RIS's phase-shift pattern using a robust optimization approach. Our simulations reveal a direct proportionality between the performance degradation caused by the malicious RIS and the number of reflective elements, along with resilience toward CSI uncertainties.
Secure Spatial Signal Design for ISAC in a Cell-Free MIMO Network
Jan 23, 2024



Abstract:In this paper, we study a cell-free multiple-input multiple-output network equipped with integrated sensing and communication (ISAC) access points (APs). The distributed APs are used to jointly serve the communication needs of user equipments (UEs) while sensing a target, assumed to be an eavesdropper (Eve). To increase the system's robustness towards said Eve, we develop an ISAC waveform model that includes artificial noise (AN) aimed at degrading the Eve channel quality. The central processing unit receives the observations from each AP and calculates the optimal precoding and AN covariance matrices by solving a semi-definite relaxation of a constrained Cramer-Rao bound (CRB) minimization problem. Simulation results highlight an underlying trade-off between sensing and communication performances: in particular, the UEs signal-to-noise and interference ratio and the maximum Eve's signal to noise ratio are directly proportional to the CRB. Furthermore, the optimal AN covariance matrix is rank-1 and has a peak in the eve's direction, leading to a surprising inverse-proportionality between the UEs-Eve distance and optimal-CRB magnitude.
Spatial Signal Design for Positioning via End-to-End Learning
Sep 26, 2022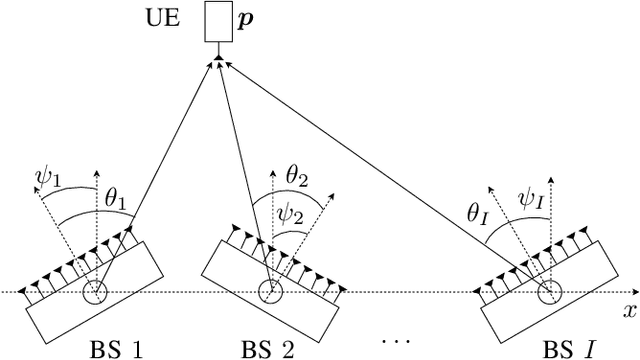
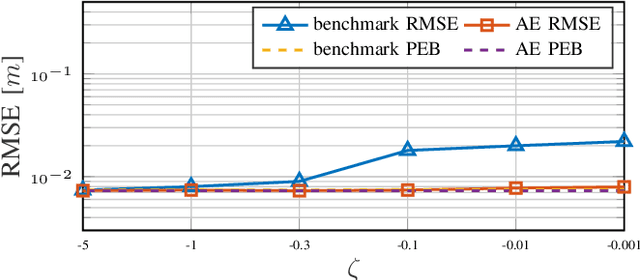

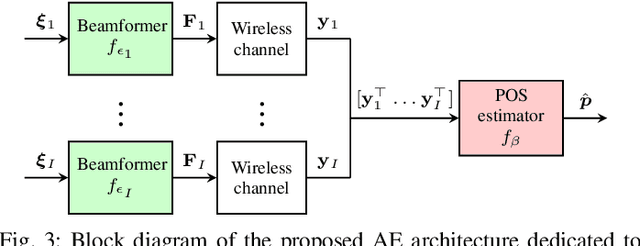
Abstract:This letter considers the problem of end-to-end learning for joint optimization of transmitter precoding and receiver processing for mmWave downlink positioning. Considering a multiple-input single-output (MISO) scenario, we propose a novel autoencoder (AE) architecture to estimate user-equipment(UE) position with multiple base-stations (BSs) and demonstrate that end-to-end learning can match model-based design, both for angle of departure (AoD) and position estimation, under ideal conditions without model deficits and outperform it in the presence of hardware impairments.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge