Dean Ta
Joint Optimization of Trajectory, Propulsion and Thrust Powers for Covert UAV-on-UAV Video Tracking and Surveillance
Dec 22, 2020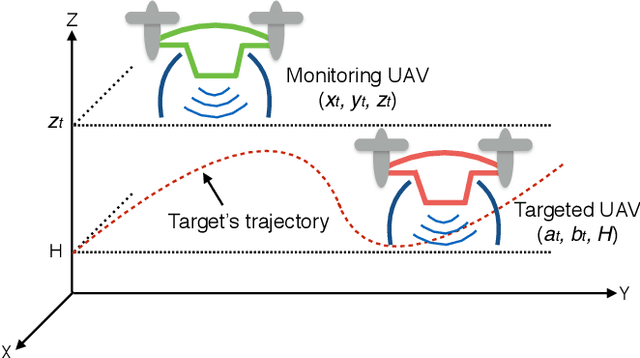
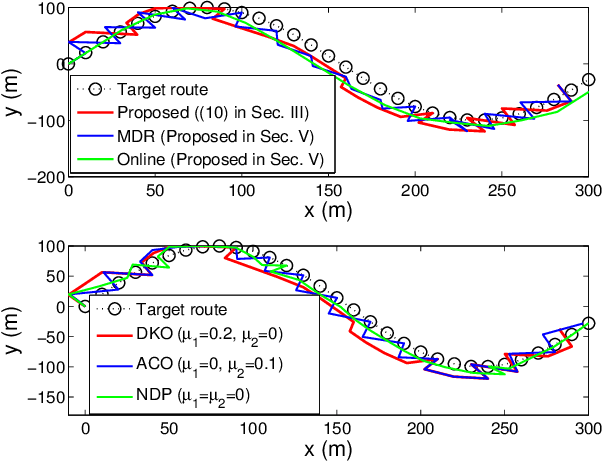
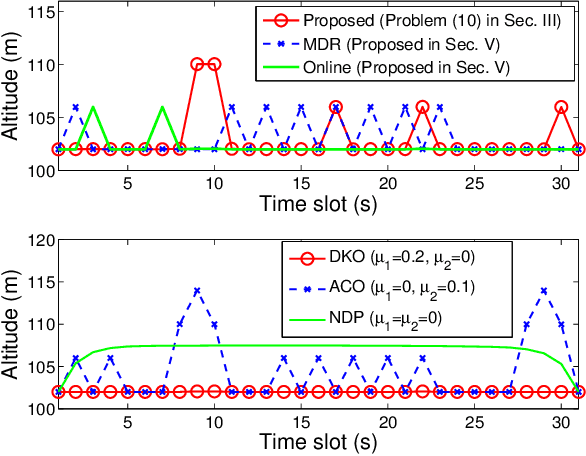
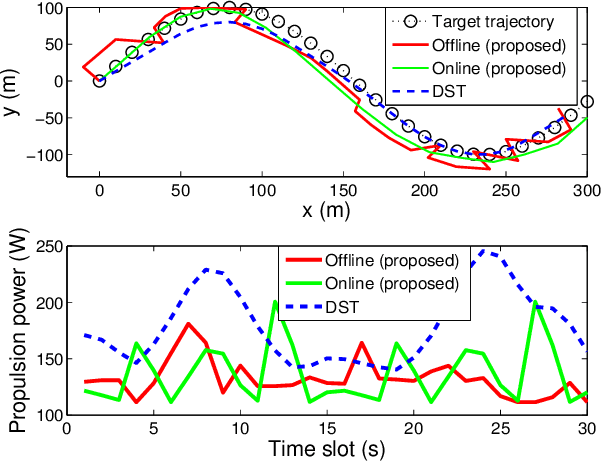
Abstract:Autonomous tracking of suspicious unmanned aerial vehicles (UAVs) by legitimate monitoring UAVs (or monitors) can be crucial to public safety and security. It is non-trivial to optimize the trajectory of a monitor while conceiving its monitoring intention, due to typically non-convex propulsion and thrust power functions. This paper presents a novel framework to jointly optimize the propulsion and thrust powers, as well as the 3D trajectory of a solar-powered monitor which conducts covert, video-based, UAV-on-UAV tracking and surveillance. A multi-objective problem is formulated to minimize the energy consumption of the monitor and maximize a weighted sum of distance keeping and altitude changing, which measures the disguising of the monitor. Based on the practical power models of the UAV propulsion, thrust and hovering, and the model of the harvested solar power, the problem is non-convex and intangible for existing solvers. We convexify the propulsion power by variable substitution, and linearize the solar power. With successive convex approximation, the resultant problem is then transformed with tightened constraints and efficiently solved by the proximal difference-of-convex algorithm with extrapolation in polynomial time. The proposed scheme can be also applied online. Extensive simulations corroborate the merits of the scheme, as compared to baseline schemes with partial or no disguising.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge