Miroslav Voznak
Integration of TinyML and LargeML: A Survey of 6G and Beyond
May 20, 2025Abstract:The transition from 5G networks to 6G highlights a significant demand for machine learning (ML). Deep learning models, in particular, have seen wide application in mobile networking and communications to support advanced services in emerging wireless environments, such as smart healthcare, smart grids, autonomous vehicles, aerial platforms, digital twins, and the metaverse. The rapid expansion of Internet-of-Things (IoT) devices, many with limited computational capabilities, has accelerated the development of tiny machine learning (TinyML) and resource-efficient ML approaches for cost-effective services. However, the deployment of large-scale machine learning (LargeML) solutions require major computing resources and complex management strategies to support extensive IoT services and ML-generated content applications. Consequently, the integration of TinyML and LargeML is projected as a promising approach for future seamless connectivity and efficient resource management. Although the integration of TinyML and LargeML shows abundant potential, several challenges persist, including performance optimization, practical deployment strategies, effective resource management, and security considerations. In this survey, we review and analyze the latest research aimed at enabling the integration of TinyML and LargeML models for the realization of smart services and applications in future 6G networks and beyond. The paper concludes by outlining critical challenges and identifying future research directions for the holistic integration of TinyML and LargeML in next-generation wireless networks.
Security and Reliability Analysis of Satellite-Terrestrial Multi-Relay Networks with Imperfect CSI
Aug 23, 2022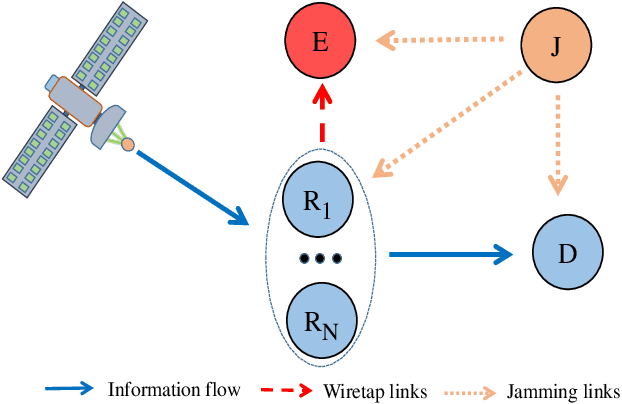
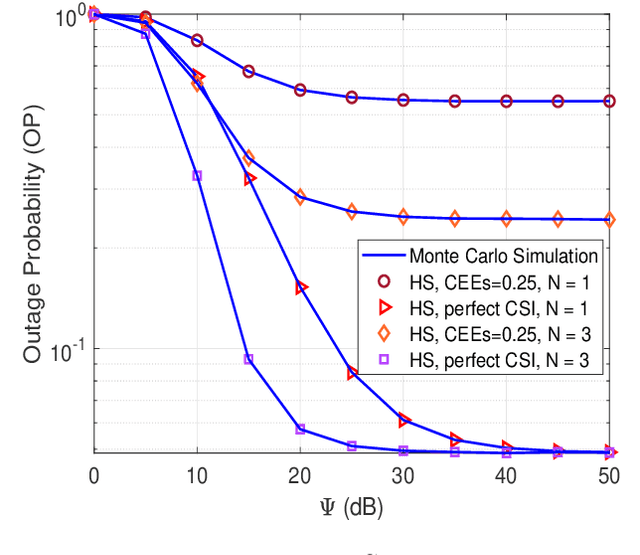
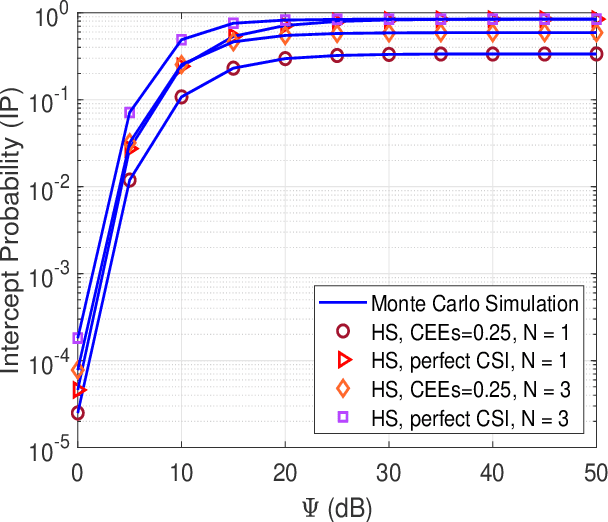
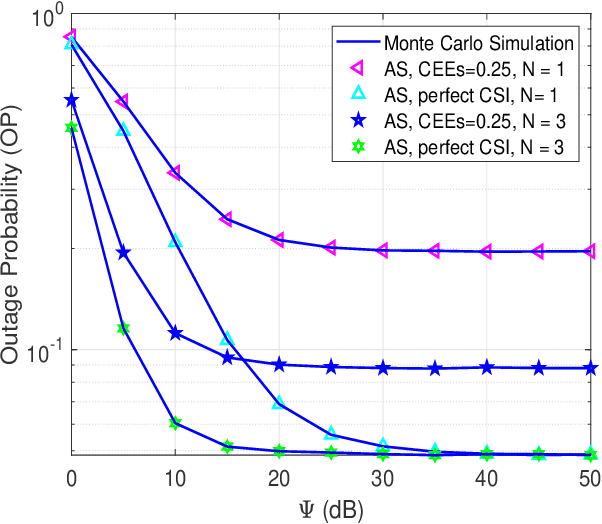
Abstract:This work investigates the security and reliability analysis for a novel satellite-terrestrial (SatTer) network. Specifically, a satellite attempts to transmit confidential information to a ground user (GU) via the support of multiple relay nodes in the presence of an eavesdropper that tries to overhear the information. A friendly jammer is deployed to improve the secure transmission between the satellite and the relays. Furthermore, satellite-to-relay generalized Rician fading channels and imperfect channel state information (CSI) are deployed to examine a general system model. In this context, the closed-formed expressions for the outage probability (OP) and intercept probability (IP) are derived corresponding to an amplify-and-forward (AF)-based relaying scheme, which is challenging and has not been studied before. Finally, the exactness of the mathematical analyses is validated through Monte Carlo simulations. Furthermore, the effects of various key parameters (e.g., channel estimation errors, satellite's transmit power, relay's transmit power, number of relays, and fading severity parameter) are examined.
Security-Reliability Trade-Off Analysis for SWIPT- and AF-Based IoT Networks with Friendly Jammers
Jun 09, 2022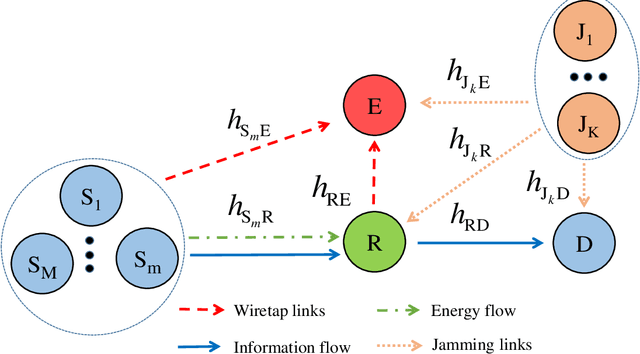
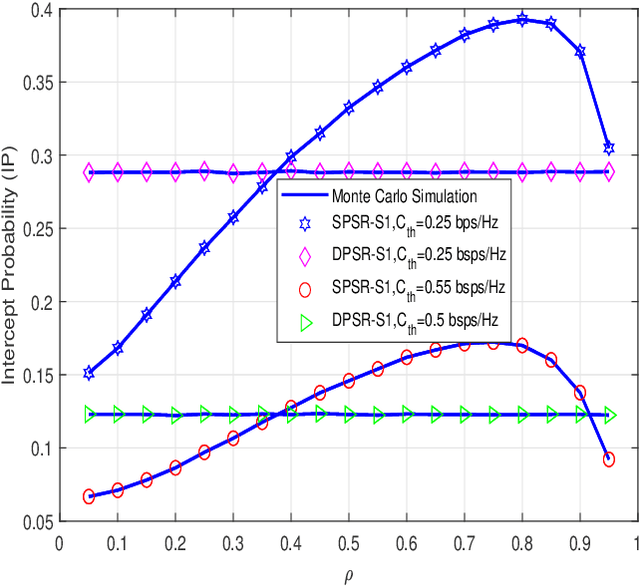
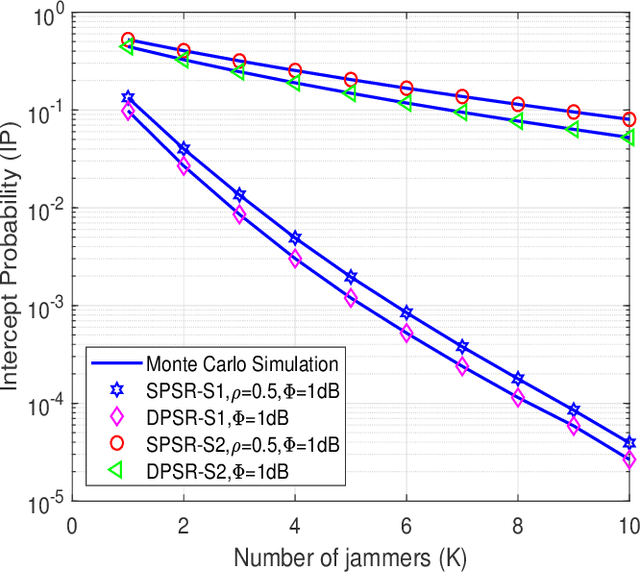
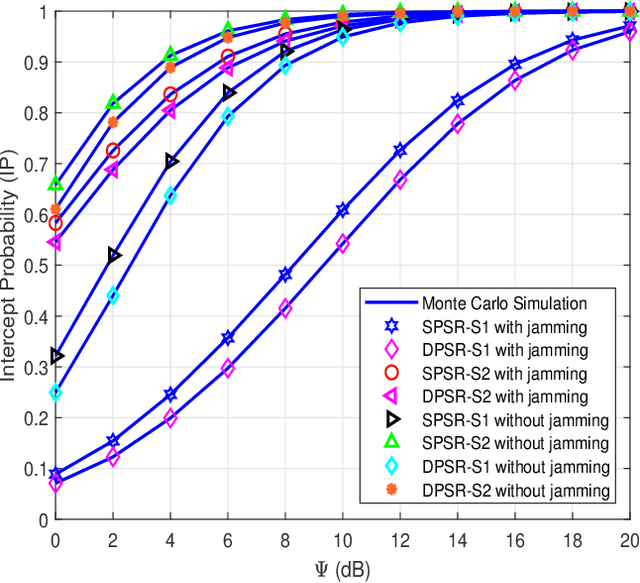
Abstract:Radio-frequency (RF) energy harvesting (EH) in wireless relaying networks has attracted considerable recent interest, especially for supplying energy to relay nodes in Internet-of-Things (IoT) systems to assist the information exchange between a source and a destination. Moreover, limited hardware, computational resources, and energy availability of IoT devices have raised various security challenges. To this end, physical layer security (PLS) has been proposed as an effective alternative to cryptographic methods for providing information security. In this study, we propose a PLS approach for simultaneous wireless information and power transfer (SWIPT)-based half-duplex (HD) amplify-and-forward (AF) relaying systems in the presence of an eavesdropper. Furthermore, we take into account both static power splitting relaying (SPSR) and dynamic power splitting relaying (DPSR) to thoroughly investigate the benefits of each one. To further enhance secure communication, we consider multiple friendly jammers to help prevent wiretapping attacks from the eavesdropper. More specifically, we provide a reliability and security analysis by deriving closed-form expressions of outage probability (OP) and intercept probability (IP), respectively, for both the SPSR and DPSR schemes. Then, simulations are also performed to validate our analysis and the effectiveness of the proposed schemes. Specifically, numerical results illustrate the non-trivial trade-off between reliability and security of the proposed system. In addition, we conclude from the simulation results that the proposed DPSR scheme outperforms the SPSR-based scheme in terms of OP and IP under the influences of different parameters on system performance.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge