Laura Pryor
Evaluation of a User Authentication Schema Using Behavioral Biometrics and Machine Learning
May 07, 2022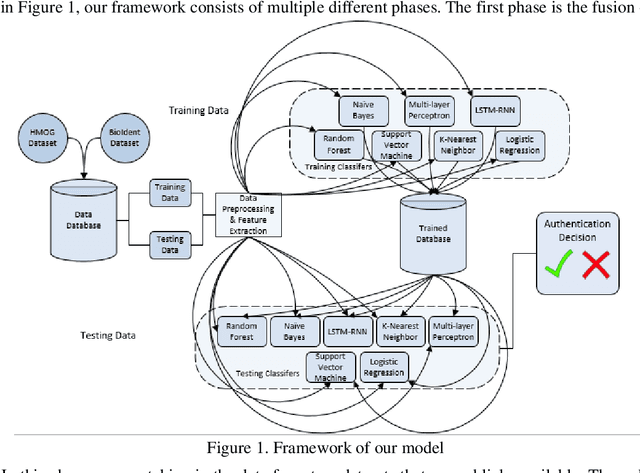
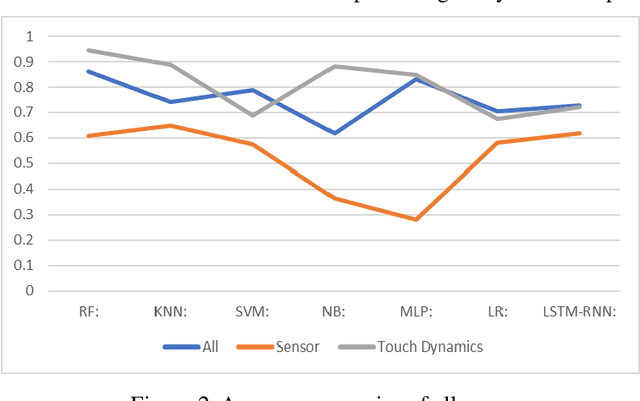
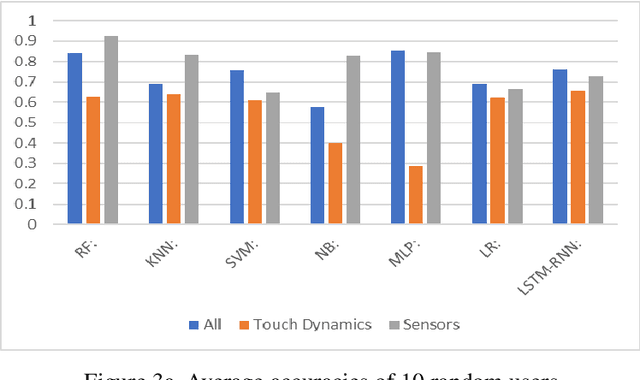
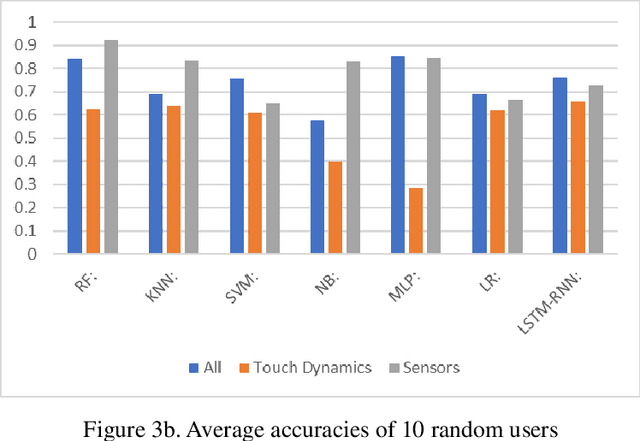
Abstract:The amount of secure data being stored on mobile devices has grown immensely in recent years. However, the security measures protecting this data have stayed static, with few improvements being done to the vulnerabilities of current authentication methods such as physiological biometrics or passwords. Instead of these methods, behavioral biometrics has recently been researched as a solution to these vulnerable authentication methods. In this study, we aim to contribute to the research being done on behavioral biometrics by creating and evaluating a user authentication scheme using behavioral biometrics. The behavioral biometrics used in this study include touch dynamics and phone movement, and we evaluate the performance of different single-modal and multi-modal combinations of the two biometrics. Using two publicly available datasets - BioIdent and Hand Movement Orientation and Grasp (H-MOG), this study uses seven common machine learning algorithms to evaluate performance. The algorithms used in the evaluation include Random Forest, Support Vector Machine, K-Nearest Neighbor, Naive Bayes, Logistic Regression, Multilayer Perceptron, and Long Short-Term Memory Recurrent Neural Networks, with accuracy rates reaching as high as 86%.
Exploration of Machine Learning Classification Models Used for Behavioral Biometrics Authentication
Apr 19, 2022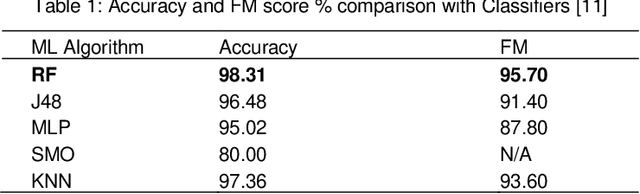
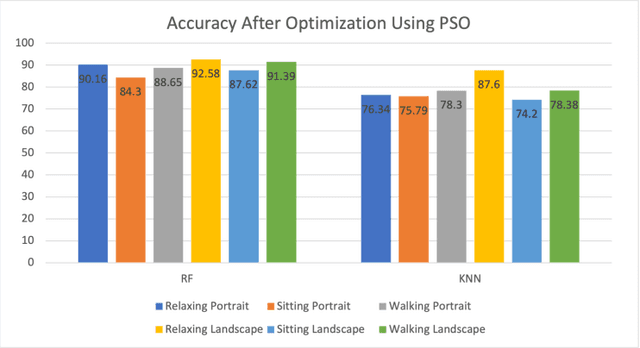
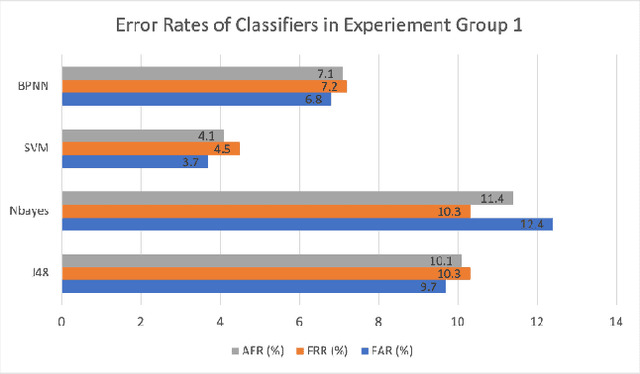
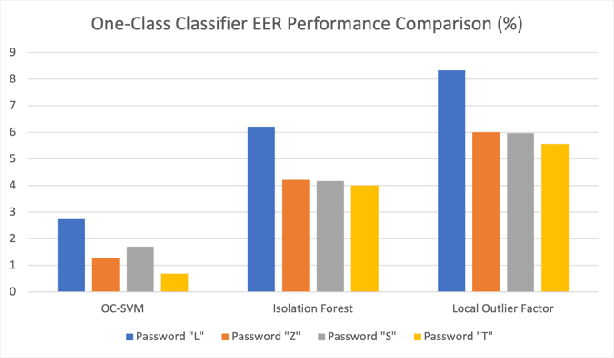
Abstract:Mobile devices have been manufactured and enhanced at growing rates in the past decades. While this growth has significantly evolved the capability of these devices, their security has been falling behind. This contrast in development between capability and security of mobile devices is a significant problem with the sensitive information of the public at risk. Continuing the previous work in this field, this study identifies key Machine Learning algorithms currently being used for behavioral biometric mobile authentication schemes and aims to provide a comprehensive review of these algorithms when used with touch dynamics and phone movement. Throughout this paper the benefits, limitations, and recommendations for future work will be discussed.
Hold On and Swipe: A Touch-Movement Based Continuous Authentication Schema based on Machine Learning
Jan 21, 2022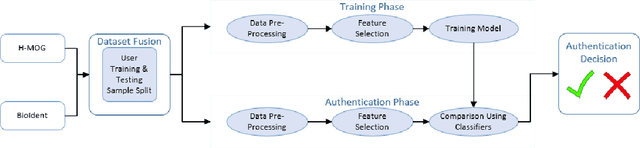
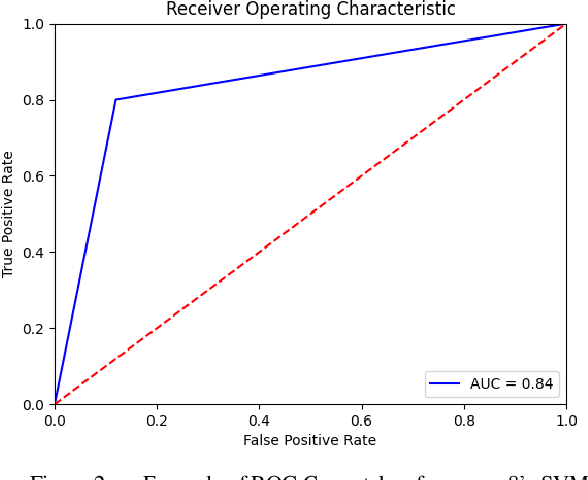
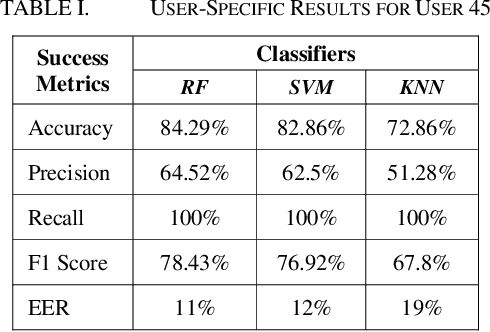
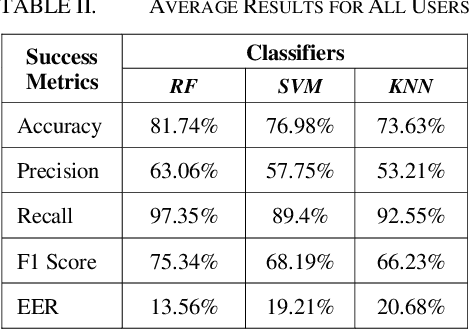
Abstract:In recent years the amount of secure information being stored on mobile devices has grown exponentially. However, current security schemas for mobile devices such as physiological biometrics and passwords are not secure enough to protect this information. Behavioral biometrics have been heavily researched as a possible solution to this security deficiency for mobile devices. This study aims to contribute to this innovative research by evaluating the performance of a multimodal behavioral biometric based user authentication scheme using touch dynamics and phone movement. This study uses a fusion of two popular publicly available datasets the Hand Movement Orientation and Grasp dataset and the BioIdent dataset. This study evaluates our model performance using three common machine learning algorithms which are Random Forest Support Vector Machine and K-Nearest Neighbor reaching accuracy rates as high as 82% with each algorithm performing respectively for all success metrics reported.
Machine Learning Algorithms In User Authentication Schemes
Oct 15, 2021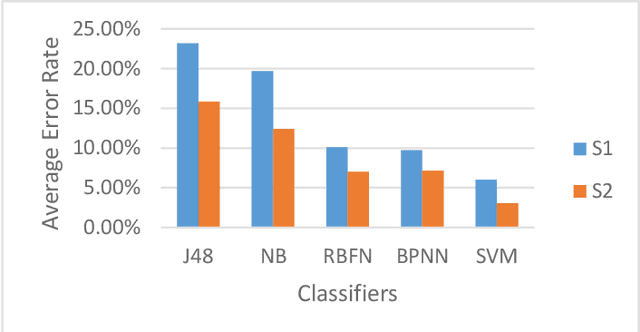
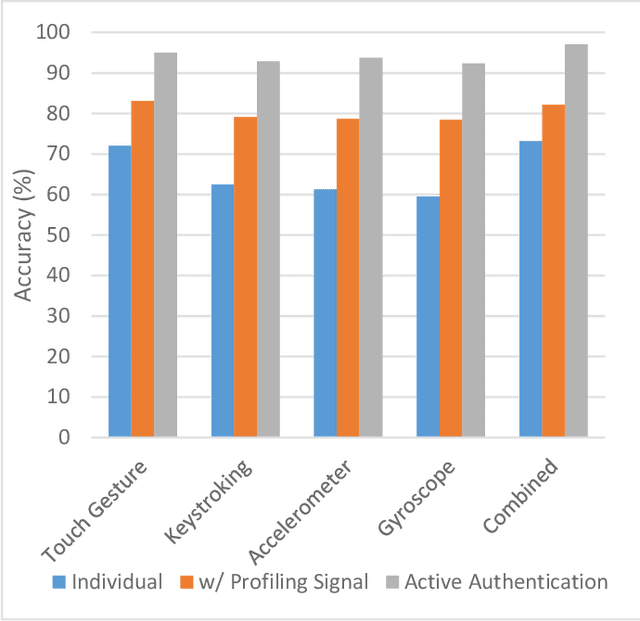
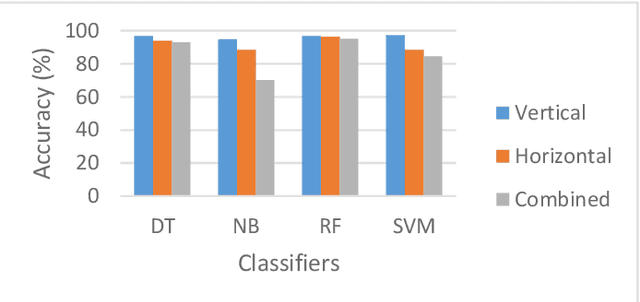
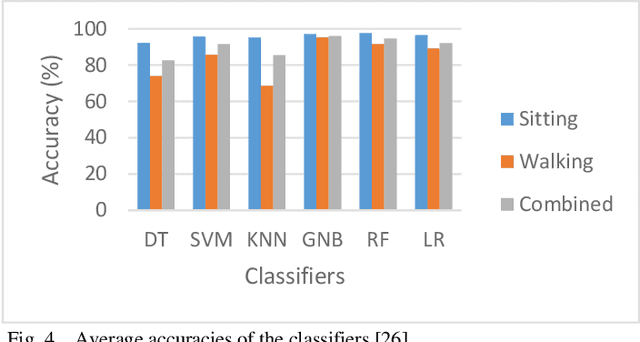
Abstract:In the past two decades, the number of mobile products being created by companies has grown exponentially. However, although these devices are constantly being upgraded with the newest features, the security measures used to protect these devices has stayed relatively the same over the past two decades. The vast difference in growth patterns between devices and their security is opening up the risk for more and more devices to easily become infiltrated by nefarious users. Working off of previous work in the field, this study looks at the different Machine Learning algorithms used in user authentication schemes involving touch dynamics and device movement. This study aims to give a comprehensive overview of the current uses of different machine learning algorithms that are frequently used in user authentication schemas involving touch dynamics and device movement. The benefits, limitations, and suggestions for future work will be thoroughly discussed throughout this paper.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge