Hui-Ming Wang
Anti-Jamming Sensing with Distributed Reconfigurable Intelligent Metasurface Antennas
Aug 07, 2025Abstract:The utilization of radio frequency (RF) signals for wireless sensing has garnered increasing attention. However, the radio environment is unpredictable and often unfavorable, the sensing accuracy of traditional RF sensing methods is often affected by adverse propagation channels from the transmitter to the receiver, such as fading and noise. In this paper, we propose employing distributed Reconfigurable Intelligent Metasurface Antennas (RIMSA) to detect the presence and location of objects where multiple RIMSA receivers (RIMSA Rxs) are deployed on different places. By programming their beamforming patterns, RIMSA Rxs can enhance the quality of received signals. The RF sensing problem is modeled as a joint optimization problem of beamforming pattern and mapping of received signals to sensing outcomes. To address this challenge, we introduce a deep reinforcement learning (DRL) algorithm aimed at calculating the optimal beamforming patterns and a neural network aimed at converting received signals into sensing outcomes. In addition, the malicious attacker may potentially launch jamming attack to disrupt sensing process. To enable effective sensing in interferenceprone environment, we devise a combined loss function that takes into account the Signal to Interference plus Noise Ratio (SINR) of the received signals. The simulation results show that the proposed distributed RIMSA system can achieve more efficient sensing performance and better overcome environmental influences than centralized implementation. Furthermore, the introduced method ensures high-accuracy sensing performance even under jamming attack.
Hidden Backdoor Attack against Deep Learning-Based Wireless Signal Modulation Classifiers
Jun 19, 2023Abstract:Recently, DL has been exploited in wireless communications such as modulation classification. However, due to the openness of wireless channel and unexplainability of DL, it is also vulnerable to adversarial attacks. In this correspondence, we investigate a so called hidden backdoor attack to modulation classification, where the adversary puts elaborately designed poisoned samples on the basis of IQ sequences into training dataset. These poisoned samples are hidden because it could not be found by traditional classification methods. And poisoned samples are same to samples with triggers which are patched samples in feature space. We show that the hidden backdoor attack can reduce the accuracy of modulation classification significantly with patched samples. At last, we propose activation cluster to detect abnormal samples in training dataset.
Sequential Anomaly Detection Against Demodulation Reference Signal Spoofing in 5G NR
Dec 02, 2022Abstract:In fifth generation (5G) new radio (NR), the demodulation reference signal (DMRS) is employed for channel estimation as part of coherent demodulation of the physical uplink shared channel. However, DMRS spoofing poses a serious threat to 5G NR since inaccurate channel estimation will severely degrade the decoding performance. In this correspondence, we propose to exploit the spatial sparsity structure of the channel to detect the DMRS spoofing, which is motivated by the fact that the spatial sparsity structure of the channel will be significantly impacted if the DMRS spoofing happens. We first extract the spatial sparsity structure of the channel by solving a sparse feature retrieval problem, then propose a sequential sparsity structure anomaly detection method to detect DMRS spoofing. In simulation experiments, we exploit clustered delay line based channel model from 3GPP standards for verifications. Numerical results show that our method outperforms both the subspace dimension based and energy detector based methods.
Physical Layer Security for NOMA-Enabled Multi-Access Edge Computing Wireless Networks
Jul 03, 2021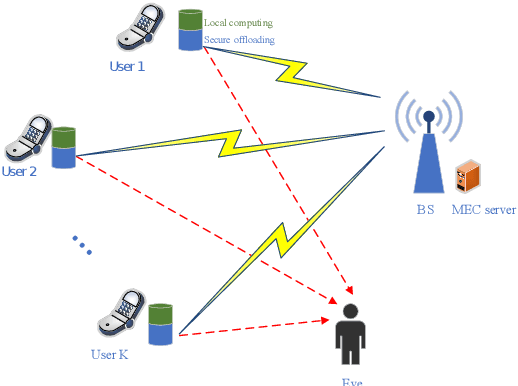
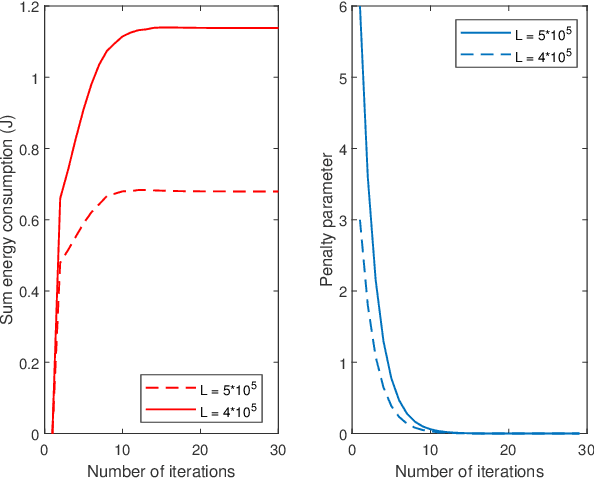
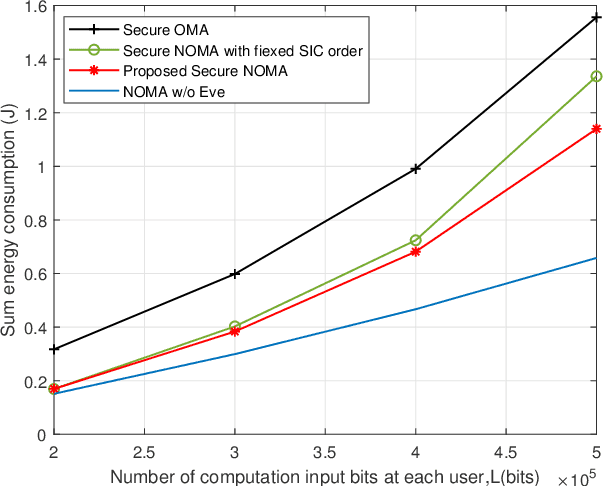
Abstract:Multi-access edge computing (MEC) has been regarded as a promising technique for enhancing computation capabilities for wireless networks. In this paper, we study physical layer security in an MEC system where multiple users offload partial of their computation tasks to a base station simultaneously based on non-orthogonal multiple access (NOMA), in the presence of a malicious eavesdropper. Secrecy outage probability is adopted to measure the security performance of the computation offloading against eavesdropping attacks. We aim to minimize the sum energy consumption of all the users, subject to constraints in terms of the secrecy offloading rate, the secrecy outage probability, and the decoding order of NOMA. Although the original optimization problem is non-convex and challenging to solve, we put forward an efficient algorithm based on sequential convex approximation and penalty dual decomposition. Numerical results are eventually provided to validate the convergence of the proposed algorithm and its superior energy efficiency with secrecy requirements.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge