Ankit Dubey
Secrecy Performance of a Keyhole-based Multi-user System with Multiple Eavesdroppers
Apr 03, 2025Abstract:This paper investigates the secrecy performance of a keyhole-aided multi-user communication network in the presence of multiple eavesdroppers. The communication happens through the same keyhole for legitimate users and eavesdroppers. In this context, the secrecy performance is evaluated for a user scheduling technique by obtaining the exact closed-form expression of secrecy outage probability (SOP). Further, a simplified asymptotic SOP expression is derived assuming high signal-to-noise ratio (SNR) scenario for a better understanding of the impact of system parameters. The effect of the keyhole parameters, number of users, number of eavesdroppers, and threshold secrecy rate on the SOP performance are also investigated for the considered system model. In the high-SNR regime, the asymptotic SOP saturates to a constant value and does not depend on the keyhole parameter and the channel parameter of the source-to-keyhole channel.
Secrecy Analysis of CSI Ratio-Based Transmitter Selection with Unreliable Backhaul
Jun 04, 2024Abstract:This paper explores the secrecy performance of a multi-transmitter system with unreliable backhaul links. To improve secrecy, we propose a novel transmitter selection (TS) scheme that selects a transmitter with the maximum ratio of the destination channel power gain to the eavesdropping channel power gain. The backhaul reliability factor is incorporated with the distribution of the channel power gain through the utilization of a mixture distribution. We evaluate the non-zero secrecy rate (NZR) and the secrecy outage probability (SOP) as well as their asymptotes in two scenarios of backhaul activity knowledge, where it is available and where it is unavailable. The results illustrate that because of the unreliable backhaul, the proposed destination-to-eavesdropper channel power gain ratio-based TS scheme is constrained in terms of secrecy performance. However, performance enhancements are observed when the backhaul knowledge activity is utilized. Furthermore, the proposed scheme outperforms all the sub-optimal TS schemes and achieves nearly optimal performance without requiring noise power or the evaluation of the exact secrecy rate measurement.
Opportunistic User Scheduling for Secure RIS-aided Wireless Communications
Mar 05, 2024Abstract:In this paper, we provide expressions for the secrecy outage probability (SOP) for suboptimal and optimal opportunistic scheduling schemes in a reconfigurable intelligent surface (RIS) aided system with multiple eavesdroppers in approximate closed form. A suboptimal scheduling (SS) scheme is analyzed, which is used when the channel state information (CSI) of the eavesdropping links is unavailable, and the optimal scheduling (OS) scheme is also analyzed, which is used when the global CSI is available. For each scheme, we provide a simplified expression for the SOP in the high signal-to-noise ratio (SNR) regime to demonstrate its behavior as a function of the key system parameters. At high SNR, the SOP saturates to a constant level which decreases exponentially with the number of RIS elements in the SS scheme and with the product of the number of RIS elements and the number of users in the OS scheme. We compare the performance of the opportunistic user scheduling schemes with that of a non-orthogonal multiple access (NOMA) based scheduling scheme which chooses a pair of users in each time slot for scheduling and we show that the opportunistic schemes outperform the NOMA-based scheme. We also derive a closed-form expression for the SOP of a decode-and-forward (DF) relay-aided scheduling scheme in order to compare it with that of the RIS-aided system. It is found that the RIS-aided system outperforms the relay-aided systems when the number of RIS elements is sufficiently large. An increased number of RIS elements is required to outperform the relay-aided system at higher operating frequencies.
Destination Scheduling for Secure Pinhole-Based Power-Line Communication
Jun 06, 2023



Abstract:We propose an optimal destination scheduling scheme to improve the physical layer security (PLS) of a power-line communication (PLC) based Internet-of-Things system in the presence of an eavesdropper. We consider a pinhole (PH) architecture for a multi-node PLC network to capture the keyhole effect in PLC. The transmitter-to-PH link is shared between the destinations and an eavesdropper which correlates all end-to-end links. The individual channel gains are assumed to follow independent log-normal statistics. Furthermore, the additive impulsive noise at each node is modeled by an independent Bernoulli-Gaussian process. Exact computable expressions for the average secrecy capacity (ASC) and the probability of intercept (POI) performance over many different networks are derived. Approximate closed-form expressions for the asymptotic ASC and POI are also provided. We find that the asymptotic ASC saturates to a constant level as transmit power increases. We observe that the PH has an adverse effect on the ASC. Although the shared link affects the ASC, it has no effect on the POI. We show that by artificially controlling the impulsive to background noise power ratio and its arrival rate at the receivers, the secrecy performance can be improved.
Secrecy of Opportunistic User Scheduling in RIS-Aided Systems: A Comparison with NOMA Scheduling
Jun 05, 2023Abstract:In this paper, we propose an opportunistic user scheduling scheme in a multi-user reconfigurable intelligent surface (RIS) aided wireless system to improve secrecy. We derive the secrecy outage probability (SOP) and its asymptotic expression in approximate closed form. The asymptotic analysis shows that the SOP does not depend on the transmitter-to-RIS distance and saturates to a fixed value depending on the ratio of the path loss of the RIS-to-destination and RIS-to-eavesdropper links and the number of users at high signal-to-noise ratio. It is shown that increasing the number of RIS elements leads to an exponential decrease in the SOP. We also compare our scheme with that of a non-orthogonal multiple access (NOMA) scheduling scheme, which chooses a pair of users to schedule in each time slot. The comparison shows that the SOP of all of the NOMA users is compromised, and that our proposed scheduling scheme has better performance.
Transmitter Selection for Secrecy Against Colluding Eavesdroppers with Backhaul Uncertainty
Jan 02, 2023



Abstract:In this paper, the secrecy performance of a multi-transmitter system with unreliable wireless backhaul links in the presence of multiple colluding eavesdroppers is considered. To improve the secrecy performance, two sub-optimal and optimal transmitter selection schemes are proposed. A generalized approach for the secrecy performance analysis is adopted to integrate the backhaul link reliability factor with the channel signal-to-noise ratio (SNR) through a mixture distribution depending on whether the backhaul reliability knowledge is unavailable or available. Non-zero secrecy rate (NZSR), secrecy outage probability (SOP), and ergodic secrecy rate (ESR) are evaluated for each selection schemes via a unified channel SNR ratio distribution based approach. Simplified asymptotic expressions are provided in each case to elucidate the infulence of the system parameters and of the backhaul reliability factor. We observe that the unreliable backhaul limits the secrecy performance of transmitter selection schemes by saturating the NZSR and SOP performance and by reducing the rate of change of the ESR with SNR. The performance improves when the knowledge of backhaul link activity is utilized, and the improvement is most noticeable when the backhaul is highly unreliable. We also observe that while the secrecy performance degrades with an increasing number of eavesdroppers, neither the asymptotic saturation value of the NZSR and SOP nor the rate of ESR improvement with SNR depends on the number of eavesdroppers.
Ergodic Secrecy Rate of Optimal Source-Destination Pair Selection in Frequency-Selective Fading
Aug 30, 2022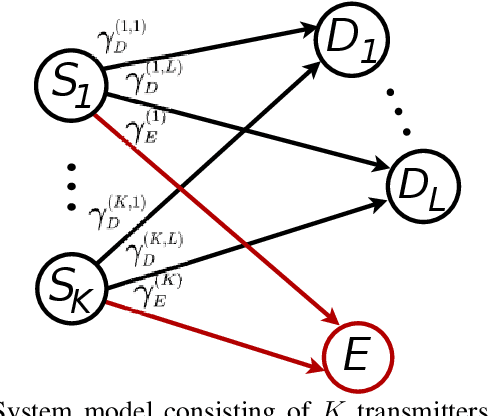
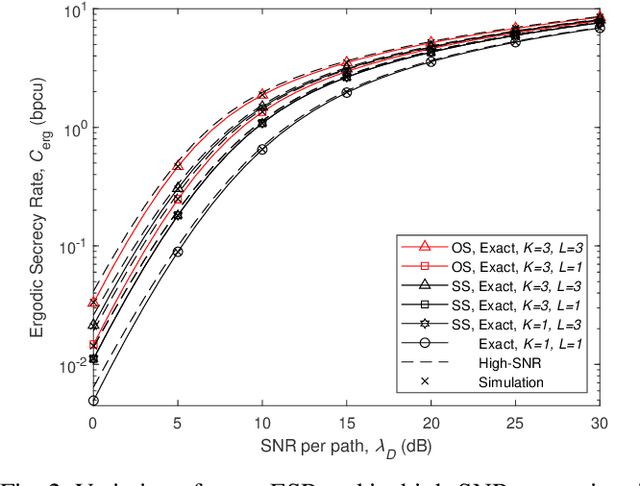
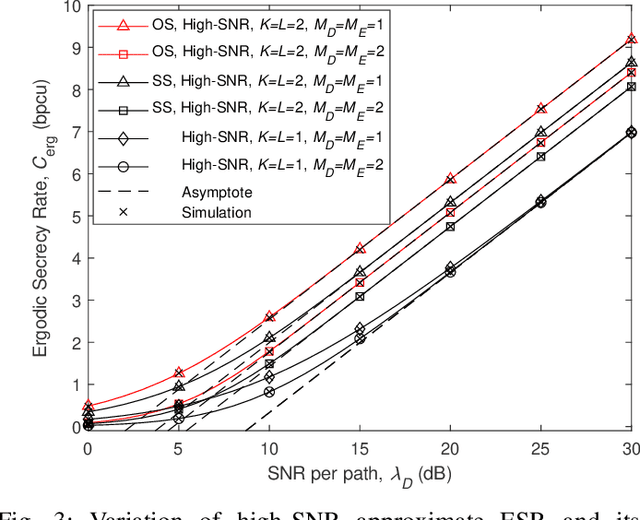
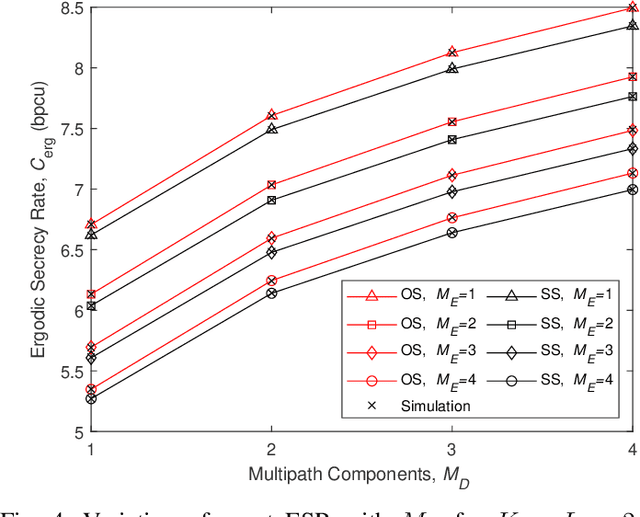
Abstract:Node selection is a simple technique to achieve diversity and thereby enhance the physical layer security in future wireless communication systems which require low complexity. High-speed data transmission often encounters frequency selective fading. In this context, we evaluate the exact closed-form expression for the ergodic secrecy rate (ESR) of the optimal source-destination pair selection scheme with single-carrier cyclic-prefix modulation, where the destination and eavesdropper channels both exhibit independent frequency selective fading with an arbitrary number of multipath components. A simplified analysis in the high-SNR scenario along with an asymptotic analysis is also provided. We also derive and compare the corresponding results for the sub-optimal source-destination pair selection scheme. We show that our analysis produces the corresponding ESR results under narrowband independent Nakagami-$m$ fading channel with any arbitrary integer parameter $m$. The effect of transmitters, destination and eavesdropping paths correlation on the ESR is also demonstrated. Our solution approach is general and can be used to find the ESR of a wider variety of transmitter selection schemes.
Optimal Friendly Jamming and Transmit Power Allocation in RIS-assisted Secure Communication
Aug 02, 2022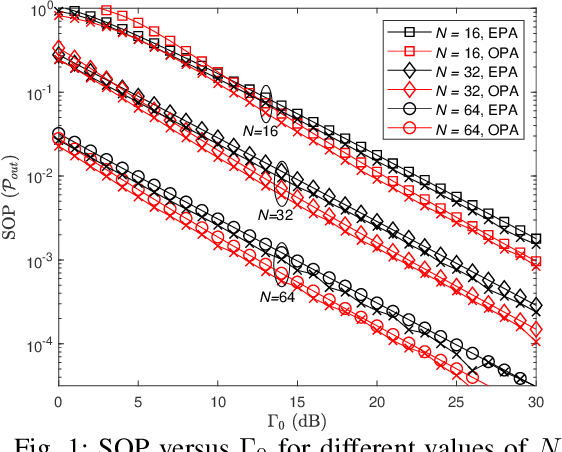
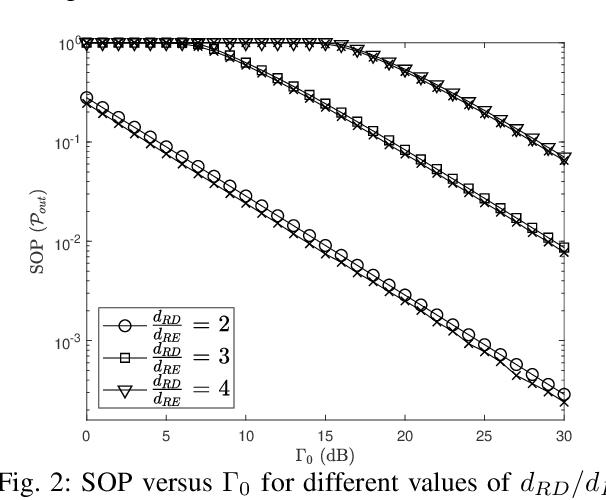
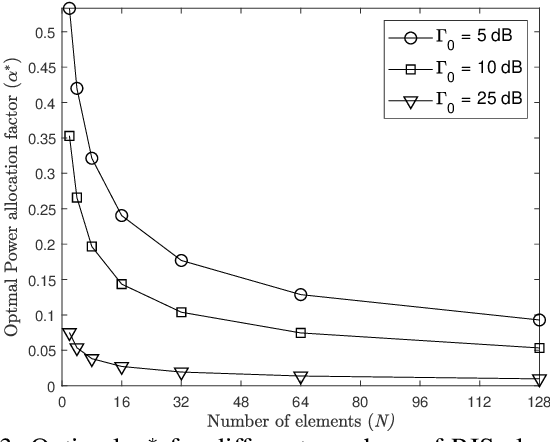
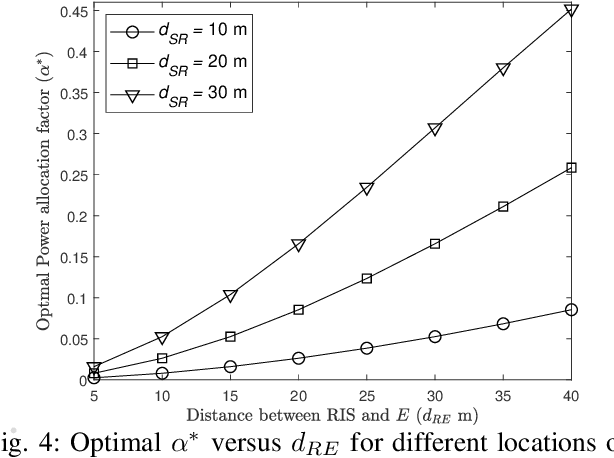
Abstract:This paper analyzes the secrecy performance of a reconfigurable intelligent surface (RIS) assisted wireless communication system with a friendly jammer in the presence of an eavesdropper. The friendly jammer enhances the secrecy by introducing artificial noise towards the eavesdropper without degrading the reception at the destination. Approximate secrecy outage probability (SOP) is derived in closed form. We also provide a simpler approximate closed-form expression for the SOP in order to understand the effect of system parameters on the performance and to find the optimal power allocation for the transmitter and jammer. The optimal transmit and jamming power allocation factor is derived by minimizing the SOP assuming a total power constraint. It is shown that the SOP performance is significantly improved by the introduction of the jammer and a gain of approximately $3$ dB is achieved at an SOP of $10^{-4}$ by optimally allocating power compared to the case of equal power allocation.
Incremental Relaying for Power Line Communication: Performance Analysis and Power Allocation
Mar 09, 2021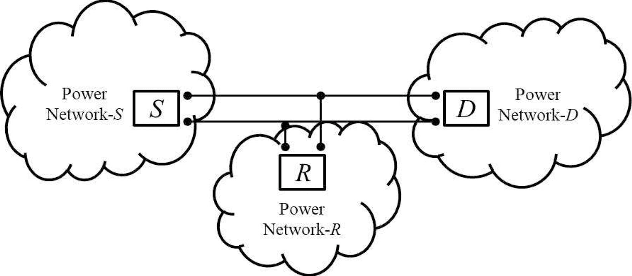
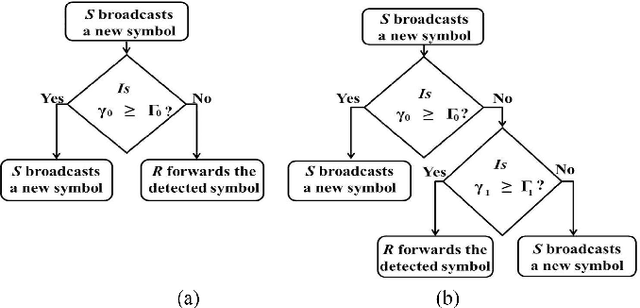
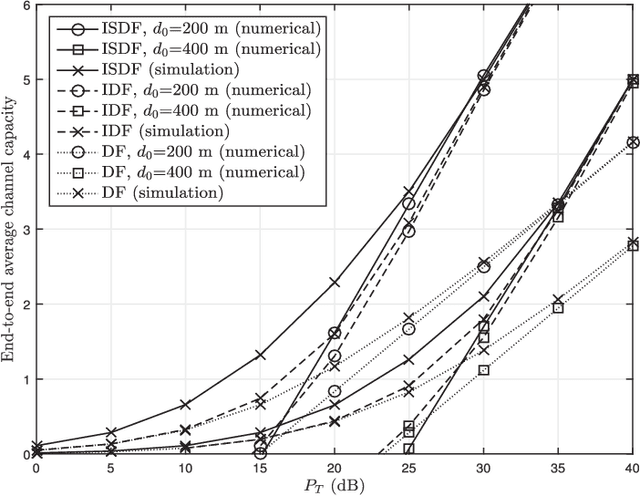
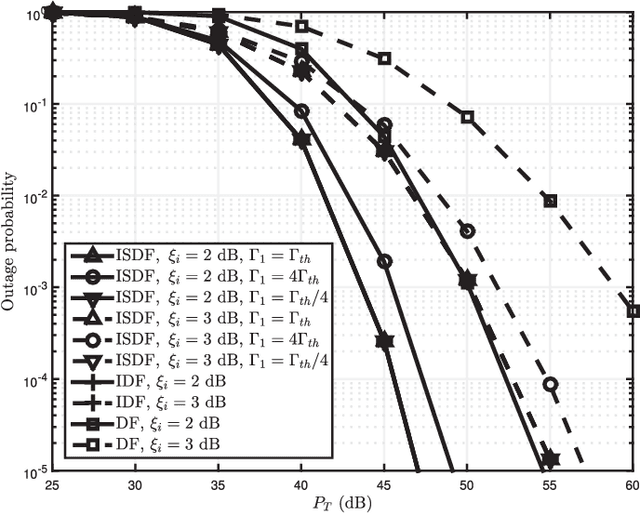
Abstract:In this paper, incremental decode-and-forward (IDF) and incremental selective decode-and-forward (ISDF) relaying are proposed to improve the spectral efficiency of power line communication. Contrary to the traditional decode-and-forward (DF) relaying, IDF and ISDF strategies utilize the relay only if the direct link ceases to attain a certain information rate, thereby improving the spectral efficiency. The path gain through the power line is assumed to be log-normally distributed with high distance-dependent attenuation and the additive noise is from a Bernoulli-Gaussian process. Closed-form expressions for the outage probability, and approximate closed-form expressions for the end-to-end average channel capacity and the average bit error rate for binary phase-shift keying are derived. Furthermore, a closed-form expression for the fraction of times the relay is in use is derived as a measure of the spectral efficiency. Comparative analysis of IDF and ISDF with traditional DF relaying is presented. It is shown that IDF is a specific case of ISDF and can obtain optimal spectral efficiency without compromising the outage performance. By employing power allocation to minimize the outage probability, it is realized that the power should be allocated in accordance with the inter-node distances and channel parameters.
Transmitter Selection for Secrecy in a Frequency Selective Fading Channel with Unreliable Backhaul
Feb 17, 2021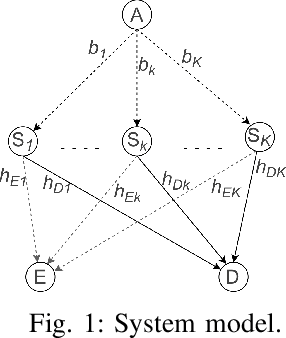
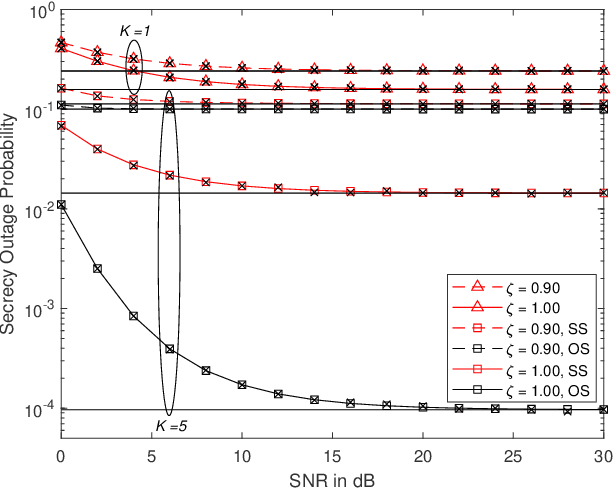
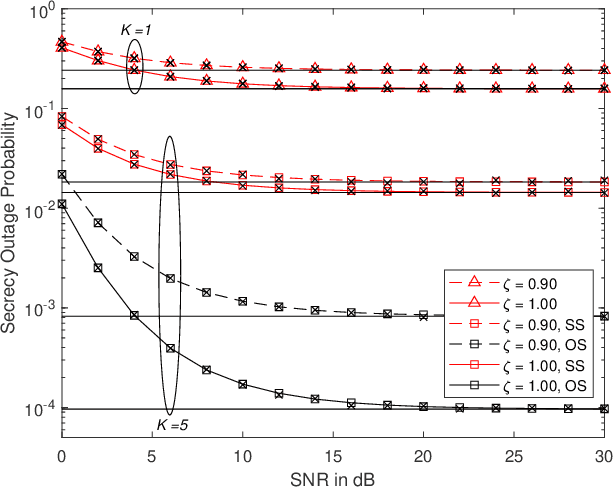
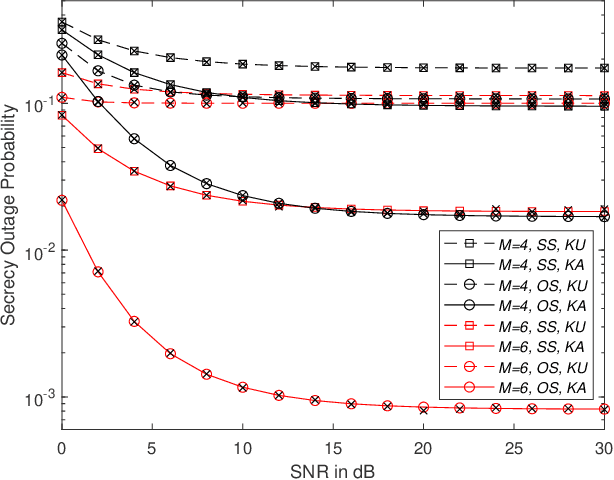
Abstract:In this paper, a communication network using single carrier with cyclic prefix modulation over frequency selective channels is considered, where an access point provides connectivity to a legitimate destination through multiple transmitters with unreliable backhaul links in the presence of an eavesdropper. A sub-optimal and an optimal transmitter selection scheme are proposed to improve the secrecy of the system, depending on whether the active backhaul channel knowledge is available a priori or not. The secrecy outage probability (SOP) and its asymptotic limit are presented in closed-form. This provides some insights regarding how knowledge of the active backhaul links affects the secrecy performance of the network. Our results show that the optimal transmitter selection scheme obtains a larger benefit than the sub-optimal scheme from the knowledge of the active backhaul links, resulting in a significantly improved system performance; however, the sub-optimal transmitter selection scheme can reduce the complexity and feedback overhead.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge