Muhammad Ismail
Clustered Scheduling and Communication Pipelining For Efficient Resource Management Of Wireless Federated Learning
Jun 15, 2022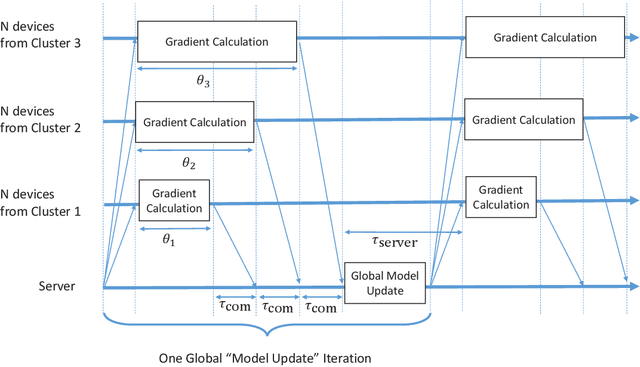
Abstract:This paper proposes using communication pipelining to enhance the wireless spectrum utilization efficiency and convergence speed of federated learning in mobile edge computing applications. Due to limited wireless sub-channels, a subset of the total clients is scheduled in each iteration of federated learning algorithms. On the other hand, the scheduled clients wait for the slowest client to finish its computation. We propose to first cluster the clients based on the time they need per iteration to compute the local gradients of the federated learning model. Then, we schedule a mixture of clients from all clusters to send their local updates in a pipelined manner. In this way, instead of just waiting for the slower clients to finish their computation, more clients can participate in each iteration. While the time duration of a single iteration does not change, the proposed method can significantly reduce the number of required iterations to achieve a target accuracy. We provide a generic formulation for optimal client clustering under different settings, and we analytically derive an efficient algorithm for obtaining the optimal solution. We also provide numerical results to demonstrate the gains of the proposed method for different datasets and deep learning architectures.
Joint Detection and Localization of Stealth False Data Injection Attacks in Smart Grids using Graph Neural Networks
Apr 24, 2021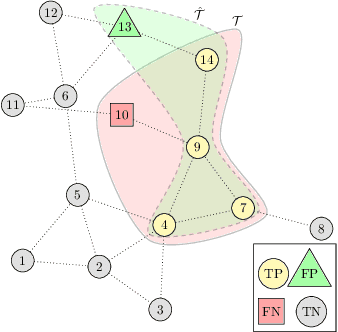
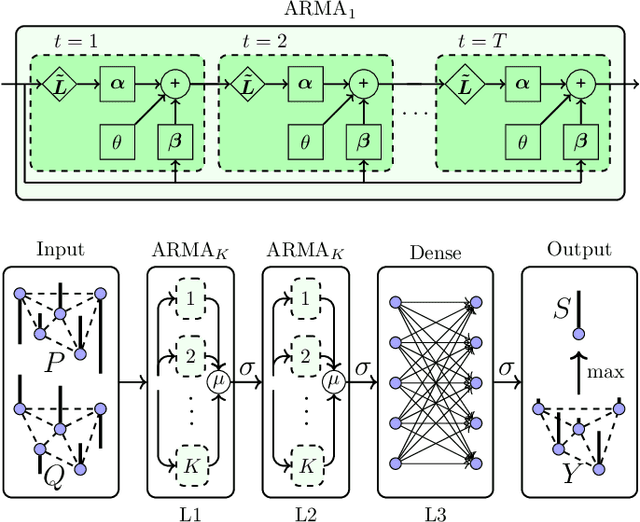
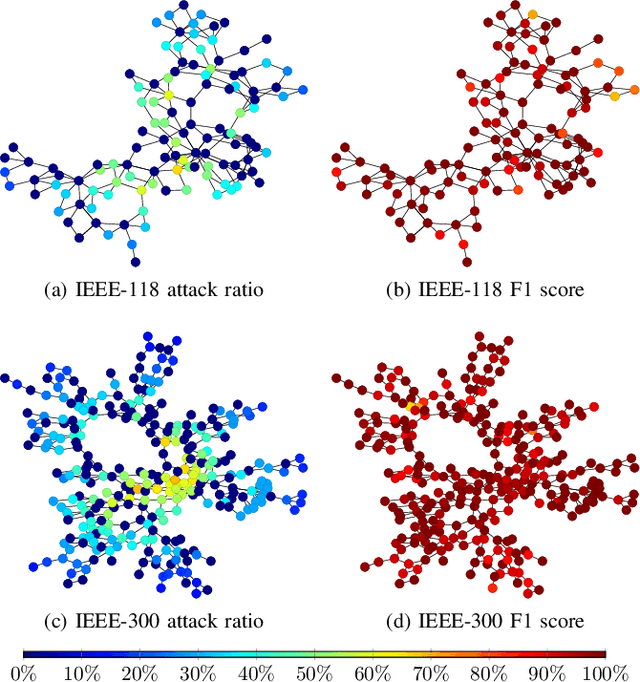
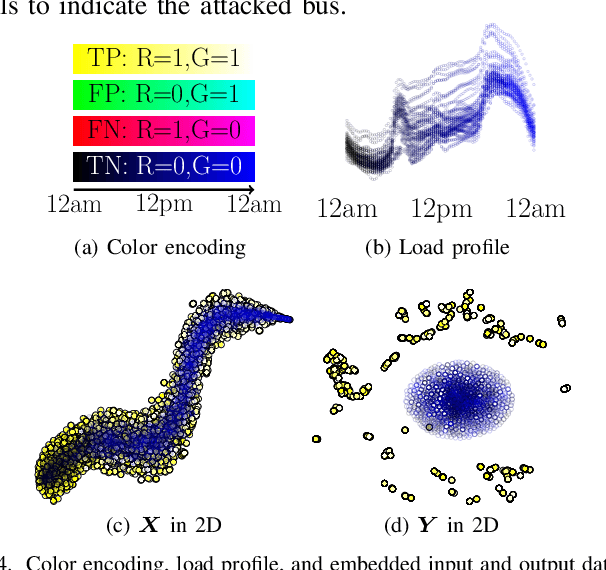
Abstract:False data injection attacks (FDIA) are becoming an active avenue of research as such attacks are more frequently encountered in power systems. Contrary to the detection of these attacks, less attention has been paid to identifying the attacked units of the grid. To this end, this work jointly studies detecting and localizing the stealth FDIA in modern power grids. Exploiting the inherent graph topology of power systems as well as the spatial correlations of smart meters' data, this paper proposes an approach based on the graph neural network (GNN) to identify the presence and location of the FDIA. The proposed approach leverages the auto-regressive moving average (ARMA) type graph convolutional filters which offer better noise robustness and frequency response flexibility compared to the polynomial type graph convolutional filters such as Chebyshev. To the best of our knowledge, this is the first work based on GNN that automatically detects and localizes FDIA in power systems. Extensive simulations and visualizations show that the proposed approach outperforms the available methods in both detection and localization FDIA for different IEEE test systems. Thus, the targeted areas in power grids can be identified and preventive actions can be taken before the attack impacts the grid.
Graph Neural Networks Based Detection of Stealth False Data Injection Attacks in Smart Grids
Apr 05, 2021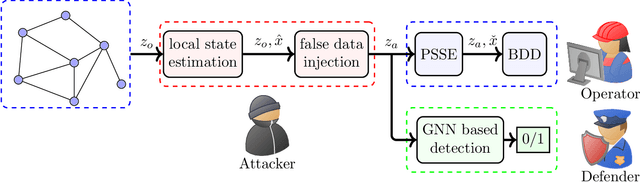
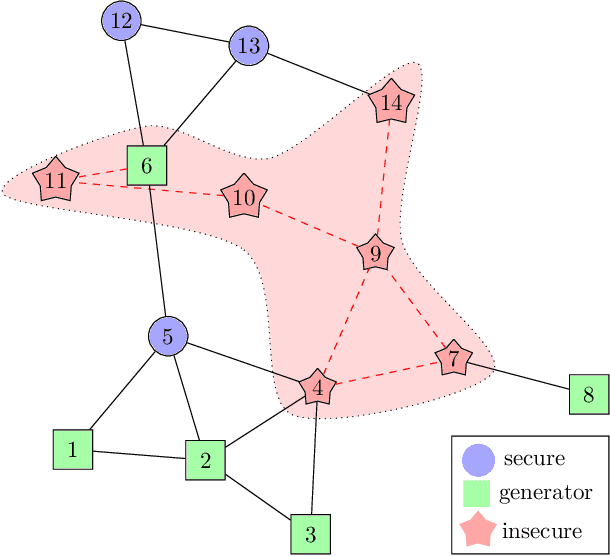
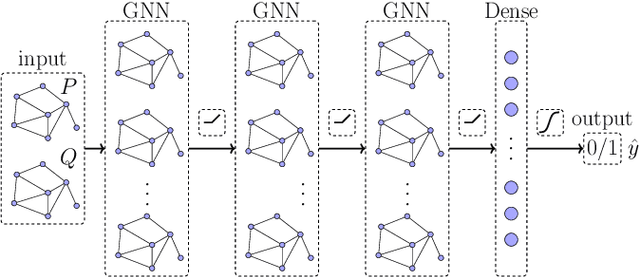
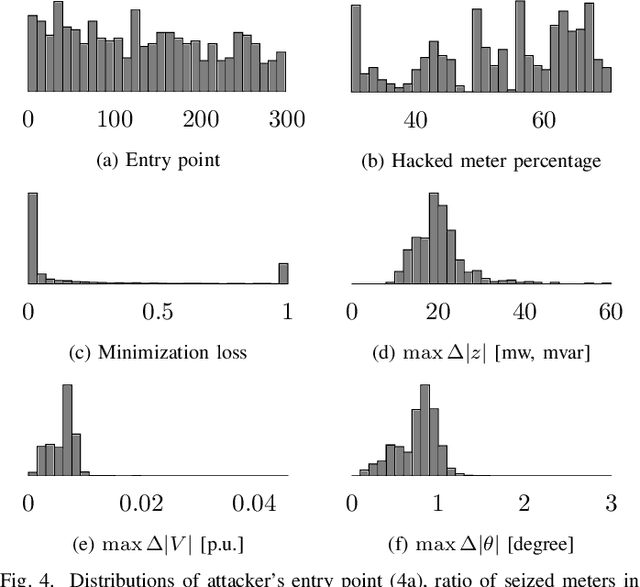
Abstract:False data injection attacks (FDIAs) represent a major class of attacks that aim to break the integrity of measurements by injecting false data into the smart metering devices in power grid. To the best of authors' knowledge, no study has attempted to design a detector that automatically models the underlying graph topology and spatially correlated measurement data of the smart grids to better detect cyber attacks. The contributions of this paper to detect and mitigate FDIAs are twofold. First, we present a generic, localized, and stealth (unobservable) attack generation methodology and a publicly accessible dataset for researchers to develop and test their algorithms. Second, we propose a Graph Neural Network (GNN) based, scalable and real-time detector of FDIAs that efficiently combines model-driven and data-driven approaches by incorporating the inherent physical connections of modern AC power grids and exploiting the spatial correlations of the measurement data. It is experimentally verified by comparing the proposed GNN based detector with the currently available FDIA detectors in literature that our algorithm outperforms the best available solutions by 6.21\%, 0.69\%, and 2.73\% in detection rate and by 3.65\%, 0.34\% and 1.38\% in F1 score for standard IEEE testbeds with 14, 118, and 300 buses, respectively.
Deep Recurrent Electricity Theft Detection in AMI Networks with Random Tuning of Hyper-parameters
Sep 06, 2018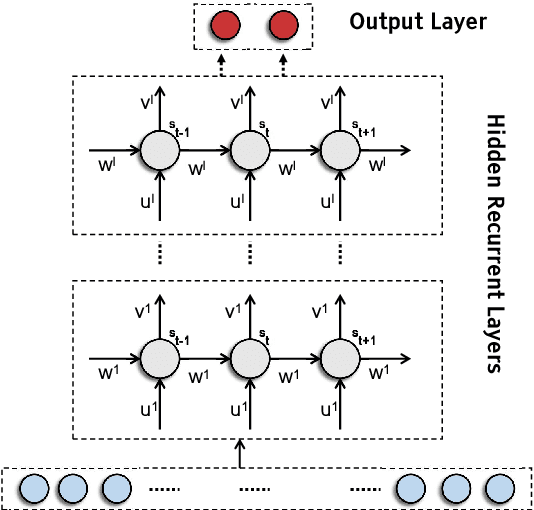
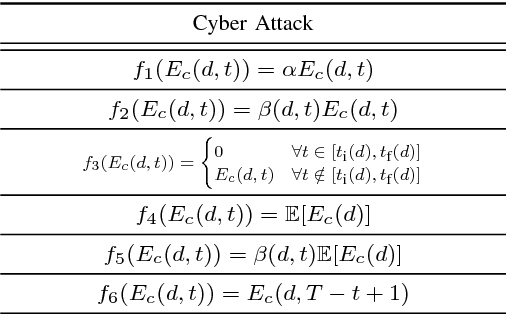
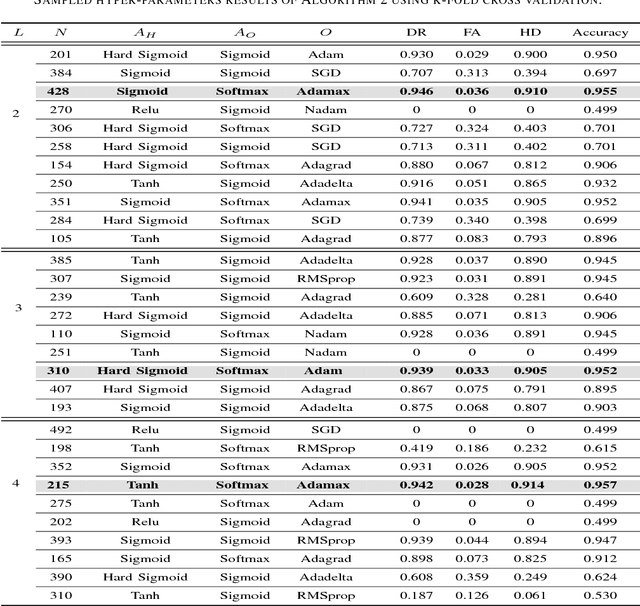
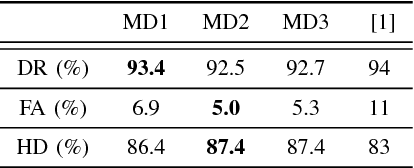
Abstract:Modern smart grids rely on advanced metering infrastructure (AMI) networks for monitoring and billing purposes. However, such an approach suffers from electricity theft cyberattacks. Different from the existing research that utilizes shallow, static, and customer-specific-based electricity theft detectors, this paper proposes a generalized deep recurrent neural network (RNN)-based electricity theft detector that can effectively thwart these cyberattacks. The proposed model exploits the time series nature of the customers' electricity consumption to implement a gated recurrent unit (GRU)-RNN, hence, improving the detection performance. In addition, the proposed RNN-based detector adopts a random search analysis in its learning stage to appropriately fine-tune its hyper-parameters. Extensive test studies are carried out to investigate the detector's performance using publicly available real data of 107,200 energy consumption days from 200 customers. Simulation results demonstrate the superior performance of the proposed detector compared with state-of-the-art electricity theft detectors.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge