Zakaria El Mrabet
Phishing Attacks Detection -- A Machine Learning-Based Approach
Jan 26, 2022Abstract:Phishing attacks are one of the most common social engineering attacks targeting users emails to fraudulently steal confidential and sensitive information. They can be used as a part of more massive attacks launched to gain a foothold in corporate or government networks. Over the last decade, a number of anti-phishing techniques have been proposed to detect and mitigate these attacks. However, they are still inefficient and inaccurate. Thus, there is a great need for efficient and accurate detection techniques to cope with these attacks. In this paper, we proposed a phishing attack detection technique based on machine learning. We collected and analyzed more than 4000 phishing emails targeting the email service of the University of North Dakota. We modeled these attacks by selecting 10 relevant features and building a large dataset. This dataset was used to train, validate, and test the machine learning algorithms. For performance evaluation, four metrics have been used, namely probability of detection, probability of miss-detection, probability of false alarm, and accuracy. The experimental results show that better detection can be achieved using an artificial neural network.
Deep Learning-Based Intrusion Detection System for Advanced Metering Infrastructure
Dec 31, 2019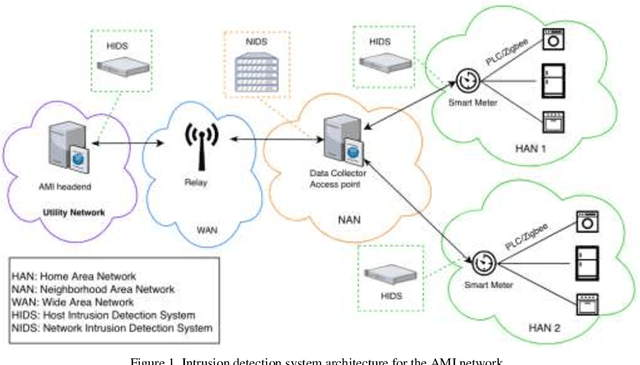
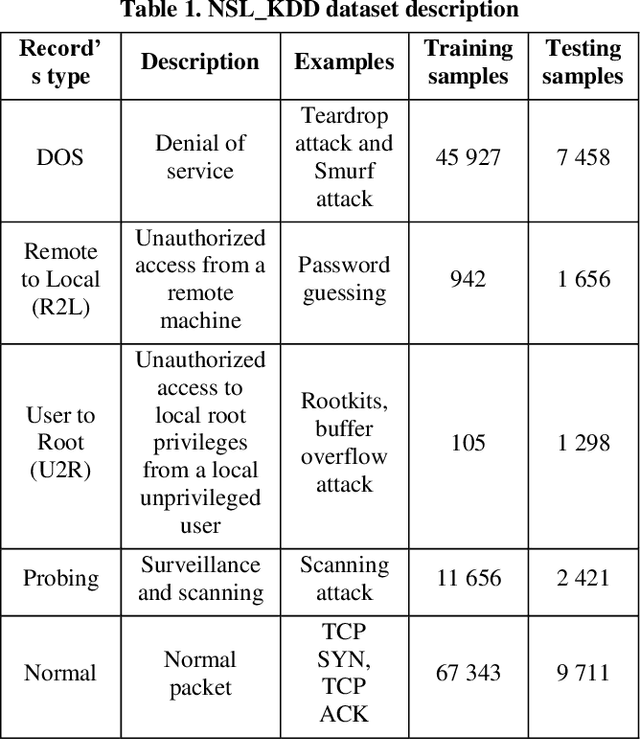
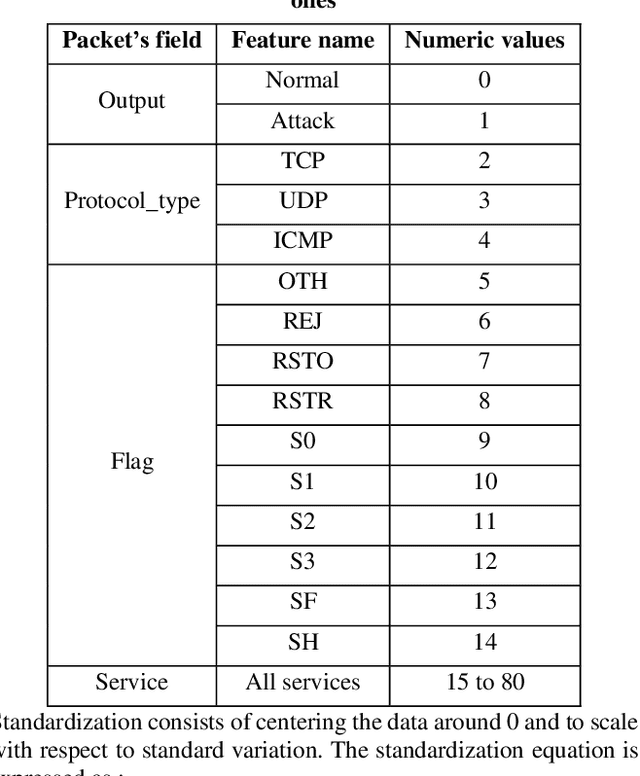
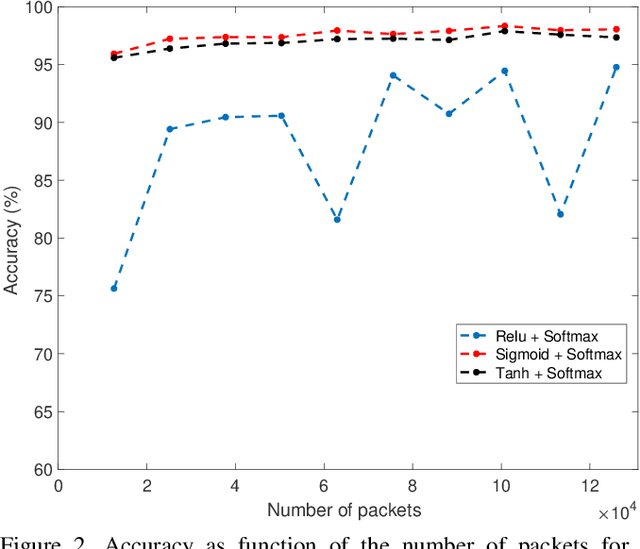
Abstract:Smart grid is an alternative solution of the conventional power grid which harnesses the power of the information technology to save the energy and meet today's environment requirements. Due to the inherent vulnerabilities in the information technology, the smart grid is exposed to a wide variety of threats that could be translated into cyber-attacks. In this paper, we develop a deep learning-based intrusion detection system to defend against cyber-attacks in the advanced metering infrastructure network. The proposed machine learning approach is trained and tested extensively on an empirical industrial dataset which is composed of several attack categories including the scanning, buffer overflow, and denial of service attacks. Then, an experimental comparison in terms of detection accuracy is conducted to evaluate the performance of the proposed approach with Naive Bayes, Support Vector Machine, and Random Forest. The obtained results suggest that the proposed approaches produce optimal results comparing to the other algorithms. Finally, we propose a network architecture to deploy the proposed anomaly-based intrusion detection system across the Advanced Metering Infrastructure network. In addition, we propose a network security architecture composed of two types of Intrusion detection system types, Host and Network-based, deployed across the Advanced Metering Infrastructure network to inspect the traffic and detect the malicious one at all the levels.
A Performance Comparison of Data Mining Algorithms Based Intrusion Detection System for Smart Grid
Dec 31, 2019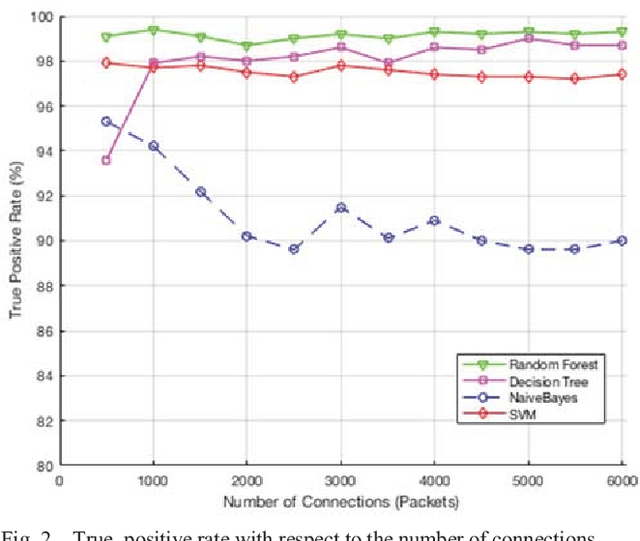
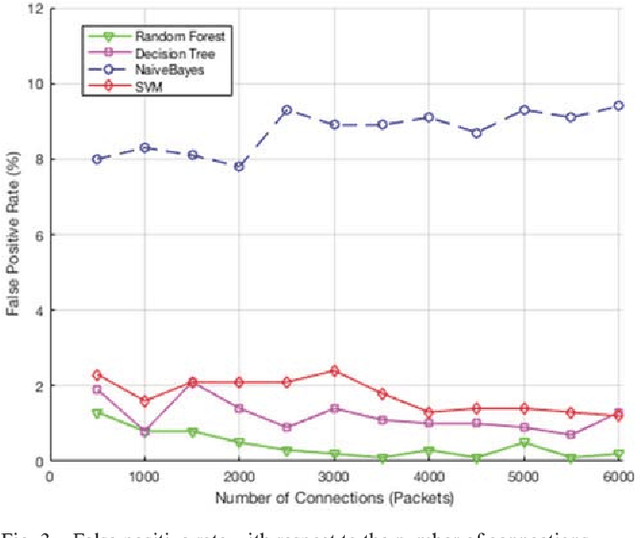
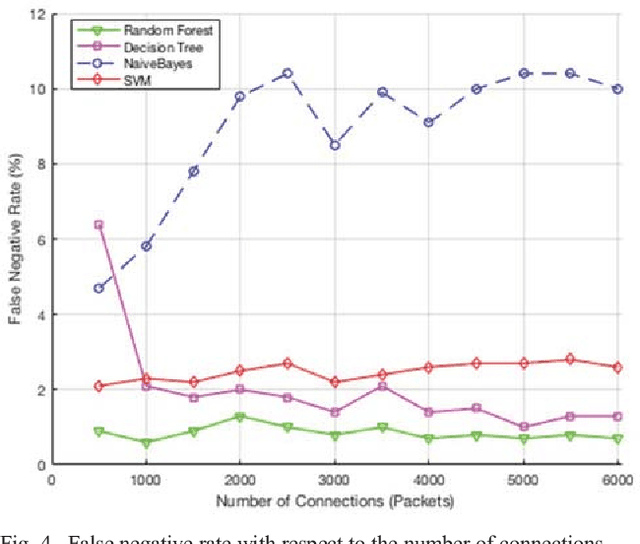
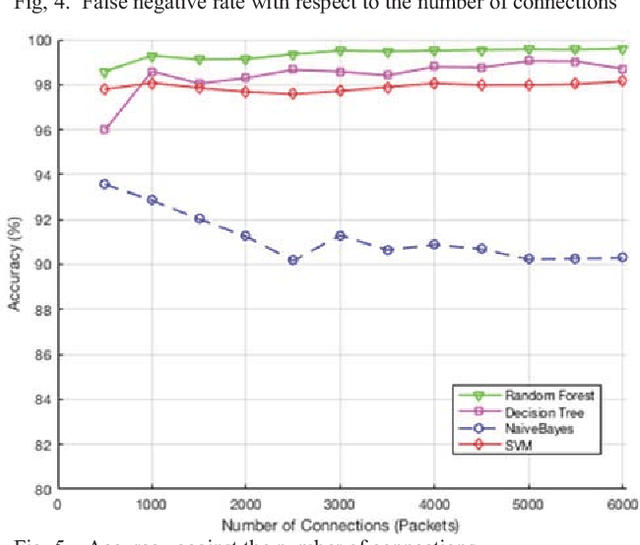
Abstract:Smart grid is an emerging and promising technology. It uses the power of information technologies to deliver intelligently the electrical power to customers, and it allows the integration of the green technology to meet the environmental requirements. Unfortunately, information technologies have its inherent vulnerabilities and weaknesses that expose the smart grid to a wide variety of security risks. The Intrusion detection system (IDS) plays an important role in securing smart grid networks and detecting malicious activity, yet it suffers from several limitations. Many research papers have been published to address these issues using several algorithms and techniques. Therefore, a detailed comparison between these algorithms is needed. This paper presents an overview of four data mining algorithms used by IDS in Smart Grid. An evaluation of performance of these algorithms is conducted based on several metrics including the probability of detection, probability of false alarm, probability of miss detection, efficiency, and processing time. Results show that Random Forest outperforms the other three algorithms in detecting attacks with higher probability of detection, lower probability of false alarm, lower probability of miss detection, and higher accuracy.
* 6 pages, 6 Figures
Primary User Emulation Attacks: A Detection Technique Based on Kalman Filter
Mar 08, 2019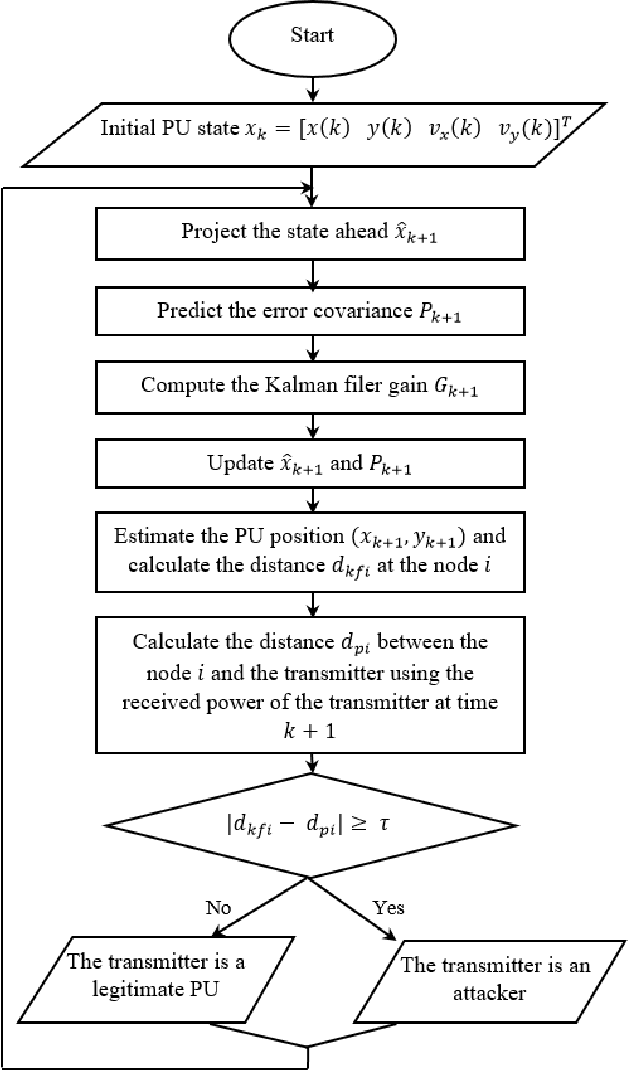
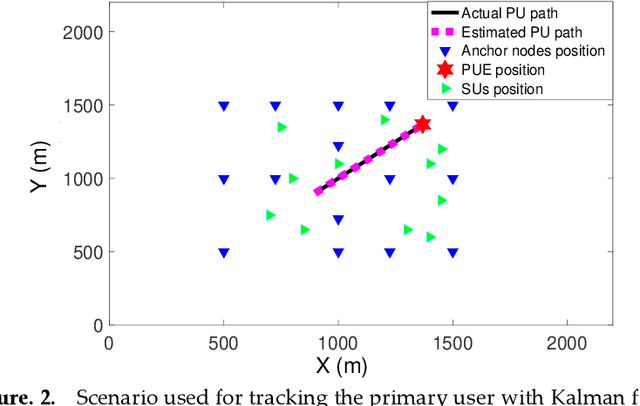
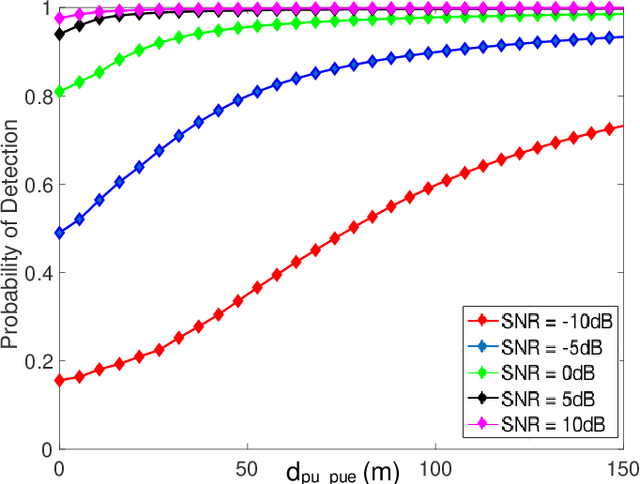
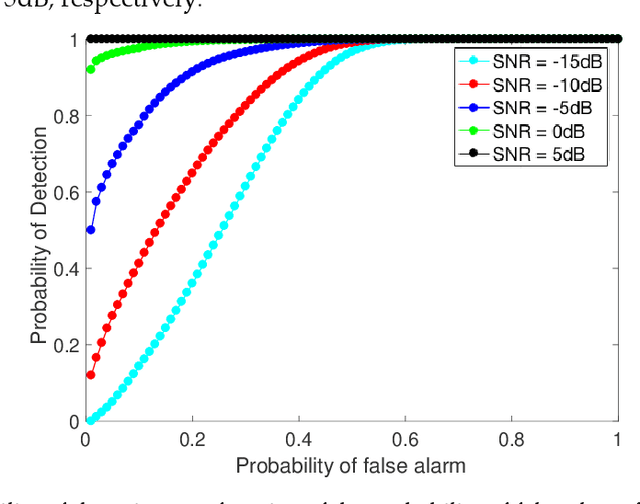
Abstract:Cognitive radio technology addresses the problem of spectrum scarcity by allowing secondary users to use the vacant spectrum bands without causing interference to the primary users. However, several attacks could disturb the normal functioning of the cognitive radio network. Primary user emulation attacks are one of the most severe attacks in which a malicious user emulates the primary user signal characteristics to either prevent other legitimate secondary users from accessing the idle channels or causing harmful interference to the primary users. There are several proposed approaches to detect the primary user emulation attackers. However, most of these techniques assume that the primary user location is fixed, which does not make them valid when the primary user is mobile. In this paper, we propose a new approach based on the Kalman filter framework for detecting the primary user emulation attacks with a non-stationary primary user. Several experiments have been conducted and the advantages of the proposed approach are demonstrated through the simulation results.
* 14 pages, 9 figures
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge