Ravikant Saini
Untrusted NOMA with Imperfect SIC: Outage Performance Analysis and Optimization
Aug 17, 2023



Abstract:Non-orthogonal multiple access (NOMA) has come to the fore as a spectral-efficient technique for fifth-generation and beyond communication networks. We consider the downlink of a NOMA system with untrusted users. In order to consider a more realistic scenario, imperfect successive interference cancellation is assumed at the receivers during the decoding process. Since pair outage probability (POP) ensures a minimum rate guarantee to each user, it behaves as a measure of the quality of service for the pair of users. With the objective of designing a reliable communication protocol, we derive the closed-form expression of POP. Further, we find the optimal power allocation that minimizes the POP. Lastly, numerical results have been presented which validate the exactness of the analysis, and reveal the effect of various key parameters on achieved pair outage performance. In addition, we benchmark optimal power allocation against equal and fixed power allocations with respect to POP. The results indicate that optimal power allocation results in improved communication reliability.
Secrecy Outage Probability Analysis for Downlink Untrusted NOMA Under Practical SIC Error
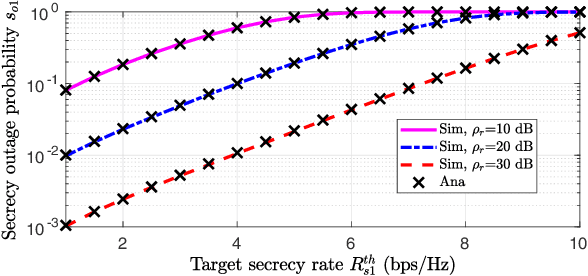
Aug 17, 2023Abstract:Non-orthogonal multiple access (NOMA) serves multiple users simultaneously via the same resource block by exploiting superposition coding at the transmitter and successive interference cancellation (SIC) at the receivers. Under practical considerations, perfect SIC may not be achieved. Thus, residual interference (RI) occurs inevitably due to imperfect SIC. In this work, we first propose a novel model for characterizing RI to provide a more realistic secrecy performance analysis of a downlink NOMA system under imperfect SIC at receivers. In the presence of untrusted users, NOMA has an inherent security flaw. Therefore, for this untrusted users' scenario, we derive new analytical expressions of secrecy outage probability (SOP) for each user in a two-user untrusted NOMA system by using the proposed RI model. To further shed light on the obtained results and obtain a deeper understanding, a high signal-to-noise ratio approximation of the SOPs is also obtained. Lastly, numerical investigations are provided to validate the accuracy of the desired analytical results and present valuable insights into the impact of various system parameters on the secrecy rate performance of the secure NOMA communication system.
Novel Outage-Aware NOMA Protocol for Secrecy Fairness Maximization Among Untrusted Users
Mar 31, 2021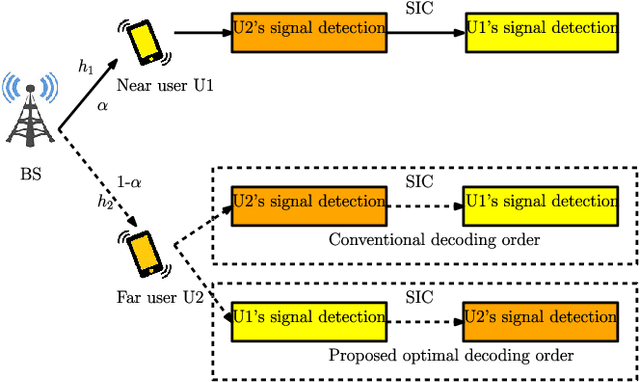
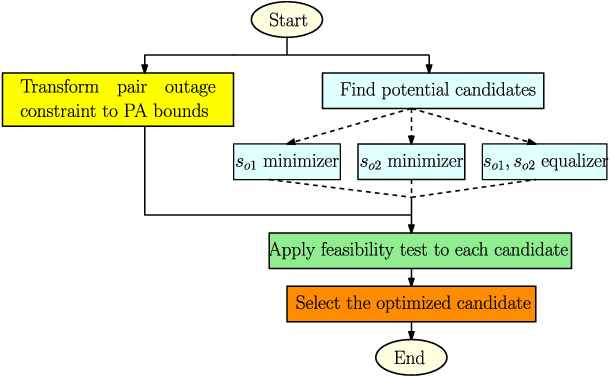
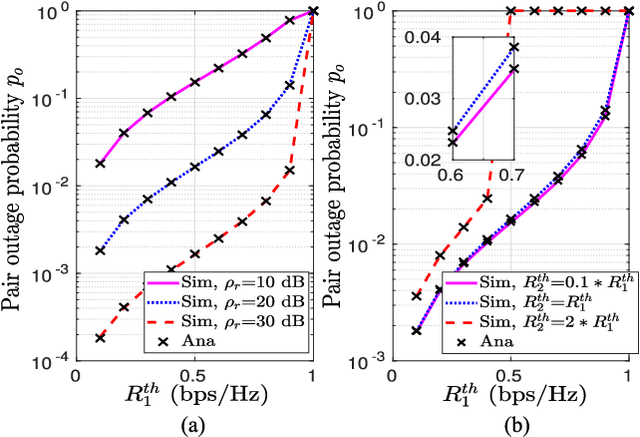
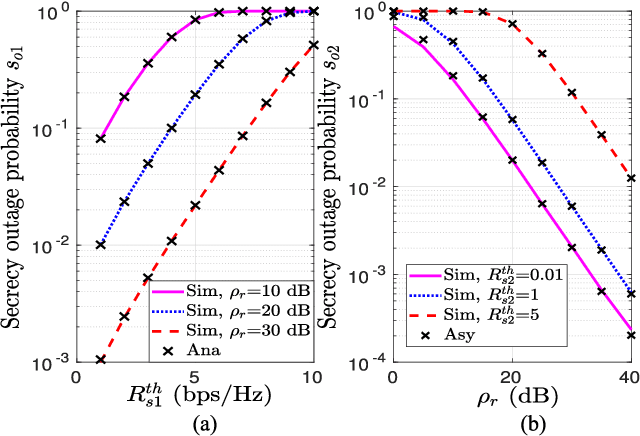
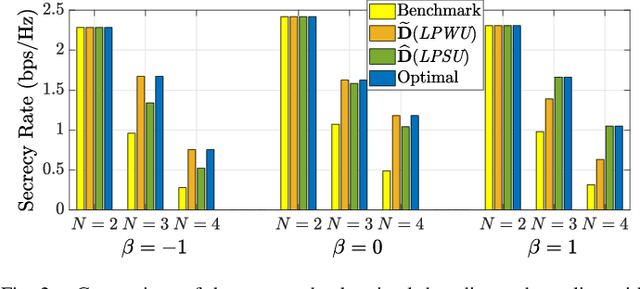
Abstract:Observing the significance of spectrally-efficient secure non-orthogonal multiple access (NOMA), this paper proposes a novel quality of service (QoS) aware secure NOMA protocol that maximizes secrecy fairness among untrusted users. Considering a base station (BS) and two users, a novel decoding order is designed that provides security to both users. With the objective of ensuring secrecy fairness between users, while satisfying their QoS requirements under BS transmit power budget constraint, we explore the problem of minimizing the maximum secrecy outage probability (SOP). Closed-form expression of pair outage probability (POP) and optimal power allocation (PA) minimizing POP are obtained. To analyze secrecy performance, analytical expressions of SOP for both users are derived, and individual SOP minimization problems are solved using concept of generalized-convexity. High signal-to-noise ratio approximation of SOP and asymptotically optimized solution minimizing this approximation is also found. Furthermore, a global-optimal solution from secrecy fairness standpoint is obtained at low computational complexity, and tight approximation is derived to get analytical insights. Numerical results present useful insights on globally optimized PA which ensure secrecy fairness and provide performance gain of about 55.12%, 69.30%, and 19.11%, respectively, compared to fixed PA and individual users' optimal PAs. Finally, a tradeoff between secrecy fairness performance and QoS demands is presented.
* 14 pages, 12 figures
Decoding Orders and Power Allocation for Untrusted NOMA: A Secrecy Perspective
Mar 30, 2021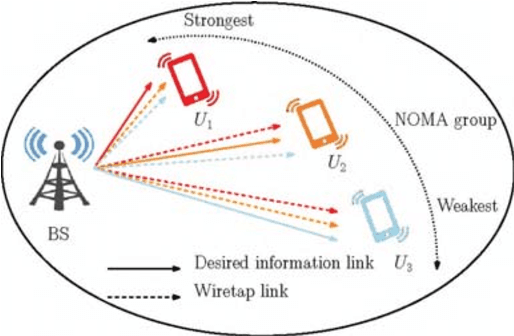
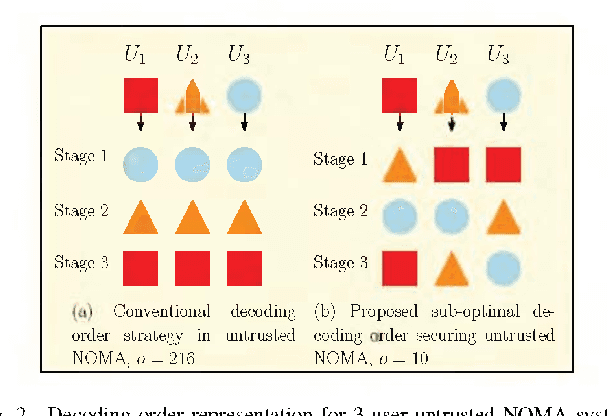
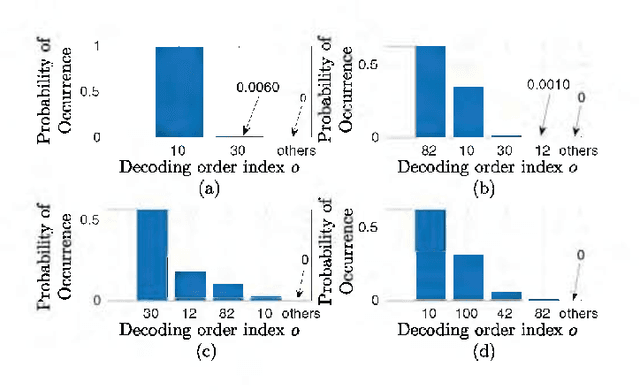
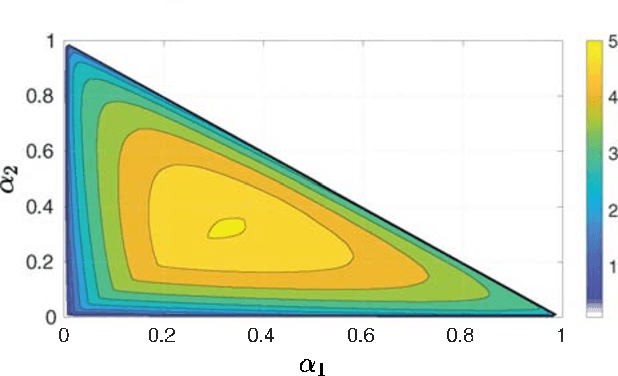
Abstract:The amalgamation of non-orthogonal multiple access (NOMA) and physical layer security is a significant research interest for providing spectrally-efficient secure fifth-generation networks. Observing the secrecy issue among multiplexed NOMA users, which is stemmed from successive interference cancellation based decoding at receivers, we focus on safeguarding untrusted NOMA. Considering the problem of each user's privacy from each other, the appropriate secure decoding order and power allocation (PA) for users are investigated. Specifically, a decoding order strategy is proposed which is efficient in providing positive secrecy at all NOMA users. An algorithm is also provided through which all the feasible secure decoding orders in accordance with the proposed decoding order strategy can be obtained. Further, in order to maximize the sum secrecy rate of the system, the joint solution of decoding order and PA is obtained numerically. Also, a sub-optimal decoding order solution is proposed. Lastly, numerical results present useful insights on the impact of key system parameters and demonstrate that average secrecy rate performance gain of about 27 dB is obtained by the jointly optimized solution over different relevant schemes.
* Conference paper, 6 pages,7 figures
Decoding Orders for Securing Untrusted NOMA
Mar 30, 2021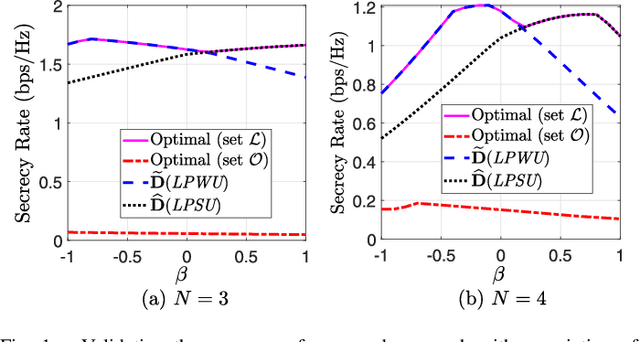
Abstract:This letter focuses on exploring a new decoding order to resolve the secrecy issue among untrusted nonorthogonal multiple access users. In this context, firstly, we identify the total number of possible decoding orders analytically. Then, we propose a decoding order strategy ensuring positive secrecy rate for all users, and obtain the number of feasible secure decoding orders based on this proposed strategy numerically. Thereafter, we present a suboptimal policy to avoid the computational complexity involved in finding the best secure decoding order. Numerical results illustrate that the suboptimal solution provides a performance gain of about 137% over therelevant benchmark.
* IEEE Networking Letters, 4 Pages, 2 Figures
Secrecy Fairness Aware NOMA for Untrusted Users
Mar 30, 2021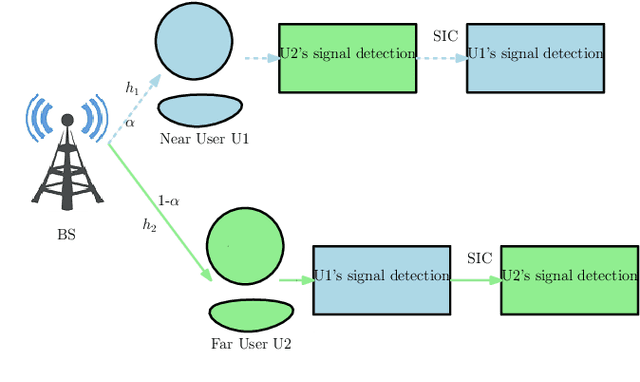
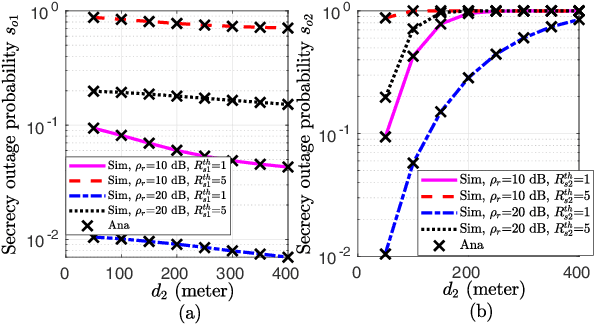
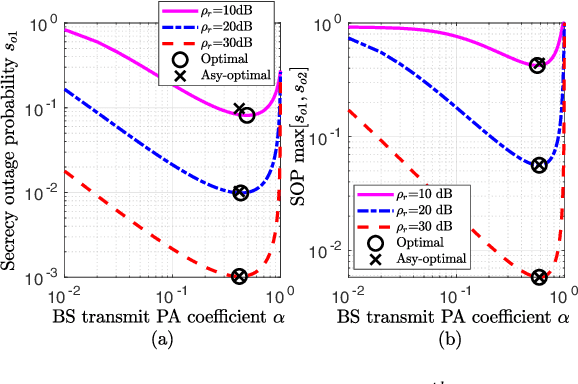
Abstract:Spectrally-efficient secure non-orthogonal multiple access (NOMA) has recently attained a substantial research interest for fifth generation development. This work explores crucial security issue in NOMA which is stemmed from utilizing the decoding concept of successive interference cancellation. Considering untrusted users, we design a novel secure NOMA transmission protocol to maximize secrecy fairness among users. A new decoding order for two users' NOMA is proposed that provides positive secrecy rate to both users. Observing the objective of maximizing secrecy fairness between users under given power budget constraint, the problem is formulated as minimizing the maximum secrecy outage probability (SOP) between users. In particular, closed-form expressions of SOP for both users are derived to analyze secrecy performance. SOP minimization problems are solved using pseudoconvexity concept, and optimized power allocation (PA) for each user is obtained. Asymptotic expressions of SOPs, and optimal PAs minimizing these approximations are obtained to get deeper insights. Further, globally-optimized power control solution from secrecy fairness perspective is obtained at a low computational complexity and, asymptotic approximation is obtained to gain analytical insights. Numerical results validate the correctness of analysis, and present insights on optimal solutions. Finally, we present insights on global-optimal PA by which fairness is ensured and gains of about 55.12%, 69.30%, and 19.11%, respectively are achieved, compared to fixed PA and individual users' optimal PAs.
* Conference paper, IEEE GLOBECOM2019, 6pages, 6 figures
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge