Rausley A. A. de Souza
Composite Generalized Quadratic Noise Modulation via Signal Addition: Towards Higher Dimensional Noise Modulations
Oct 02, 2025Abstract:This letter proposes superposing two Generalized Quadratic Noise Modulators (GQNM) by simply adding their outputs. It creates a 16-ary noise modulator that resembles QAM modulators in classical communication. It modulates the information bits on four different means and four different variances. It could also be applied to reach higher-order modulations than 16-ary schemes by adding the outputs of more than two modulators, which is not discussed in detail in this letter and left for future work. By selecting the parameters necessary for satisfying the theoretical distinguishability conditions provided in the paper, we can reach better performances in comparison to the Kirchhoff-Law Johnson Noise (KLJN) modulator and the GQNM modulator, which is verified by the simulations. The better result in terms of smaller Bit Error Probability (BEP) is achieved by increasing the complexity in the modulator, the transmitter, and the detectors in the receiver.
3D 8-Ary Noise Modulation Using Bayesian- and Kurtosis-based Detectors
Oct 02, 2025Abstract:This paper presents a novel three-dimensional (3D) 8-ary noise modulation scheme that introduces a new dimension: the mixture probability of a Mixture of Gaussian (MoG) distribution. This proposed approach utilizes the dimensions of mean and variance, in addition to the new probability dimension. Within this framework, each transmitted symbol carries three bits, each corresponding to a distinct sub-channel. For detection, a combination of specialized detectors is employed: a simple threshold based detector for the first sub-channel bit (modulated by the mean), a Maximum-Likelihood (ML) detector for the second sub-channel bit (modulated by the variance), a Kurtosis-based, Jarque-Bera (JB) test, and Bayesian Hypothesis (BHT)-based detectors for the third bit (modulated by the MoG probability). The Kurtosis- and JB-based detectors specifically distinguish between Gaussian (or near-Gaussian) and non-Gaussian MoG distributions by leveraging higher-order statistical measures. The Bit Error Probabilities (BEPs) are derived for the threshold-, Kurtosis-, and BHT-based detectors. The optimum threshold for the Kurtosis-based detector is also derived in a tractable manner. Simulation results demonstrate that a comparably low BEP is achieved for the third sub-channel bit relative to existing two-dimensional (2D) schemes. Simultaneously, the proposed scheme increases the data rate by a factor of 1.5 and 3 compared to the Generalized Quadratic noise modulator and the classical binary KLJN noise modulator, respectively. Furthermore, the Kurtosis-based detector offers a low-complexity solution, achieving an acceptable BEP of approximately 0.06.
On the Secrecy Performance of $α$-$\mathcal{F}$ Channels with Pointing Errors
Mar 19, 2025Abstract:This paper investigates the physical layer security (PLS) performance of $\alpha$-$\mathcal{F}$ fading channels with pointing errors under passive and active eavesdropping scenarios. Novel analytical expressions are derived for key PLS metrics, including the probability of strictly positive secrecy capacity, the average secrecy capacity, and the secure outage probability. An asymptotic analysis is also investigated to provide further insights into the system behavior under high signal-to-noise ratio conditions. The analytical results are validated through Monte Carlo simulations, with several performance curves presented for a range of channel and system parameters. All expressions derived in this work are original and have not been previously published.
Low-Complexity Dynamic Directional Modulation: Vulnerability and Information Leakage
May 31, 2023



Abstract:In this paper, the privacy of wireless transmissions is improved through the use of an efficient technique termed dynamic directional modulation (DDM), and is subsequently assessed in terms of the measure of information leakage. Recently, a variation of DDM termed low-power dynamic directional modulation (LPDDM) has attracted significant attention as a prominent secure transmission method due to its ability to further improve the privacy of wireless communications. Roughly speaking, this modulation operates by randomly selecting the transmitting antenna from an antenna array whose radiation pattern is well known. Thereafter, the modulator adjusts the constellation phase so as to ensure that only the legitimate receiver recovers the information. To begin with, we highlight some privacy boundaries inherent to the underlying system. In addition, we propose features that the antenna array must meet in order to increase the privacy of a wireless communication system. Last, we adopt a uniform circular monopole antenna array with equiprobable transmitting antennas in order to assess the impact of DDM on the information leakage. It is shown that the bit error rate, while being a useful metric in the evaluation of wireless communication systems, does not provide the full information about the vulnerability of the underlying system.
Semantic-Functional Communications in Cyber-Physical Systems
May 31, 2023Abstract:This paper explores the use of semantic knowledge inherent in the cyber-physical system (CPS) under study in order to minimize the use of explicit communication, which refers to the use of physical radio resources to transmit potentially informative data. It is assumed that the acquired data have a function in the system, usually related to its state estimation, which may trigger control actions. We propose that a semantic-functional approach can leverage the semantic-enabled implicit communication while guaranteeing that the system maintains functionality under the required performance. We illustrate the potential of this proposal through simulations of a swarm of drones jointly performing remote sensing in a given area. Our numerical results demonstrate that the proposed method offers the best design option regarding the ability to accomplish a previously established task -- remote sensing in the addressed case -- while minimising the use of radio resources by controlling the trade-offs that jointly determine the CPS performance and its effectiveness in the use of resources. In this sense, we establish a fundamental relationship between energy, communication, and functionality considering a given end application.
An Efficient Machine Learning-based Channel Prediction Technique for OFDM Sub-Bands
May 31, 2023Abstract:The acquisition of accurate channel state information (CSI) is of utmost importance since it provides performance improvement of wireless communication systems. However, acquiring accurate CSI, which can be done through channel estimation or channel prediction, is an intricate task due to the complexity of the time-varying and frequency selectivity of the wireless environment. To this end, we propose an efficient machine learning (ML)-based technique for channel prediction in orthogonal frequency-division multiplexing (OFDM) sub-bands. The novelty of the proposed approach lies in the training of channel fading samples used to estimate future channel behaviour in selective fading.
Semantic-functional Communications for Multiuser Event Transmissions via Random Maps
Apr 07, 2022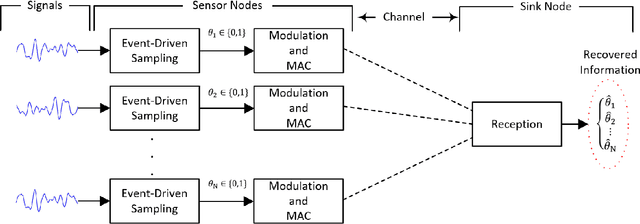
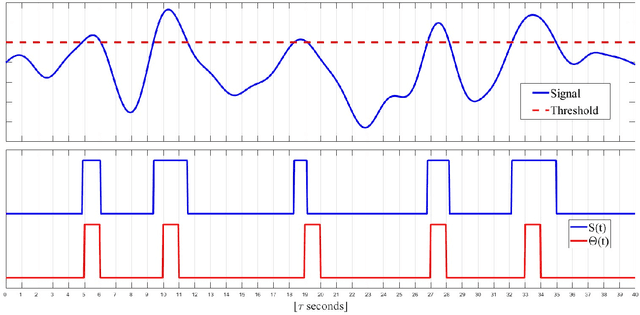
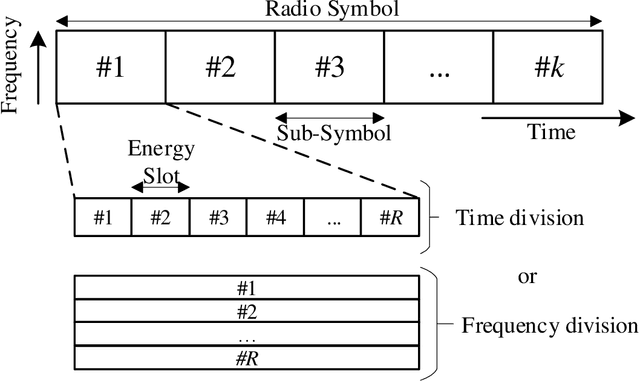
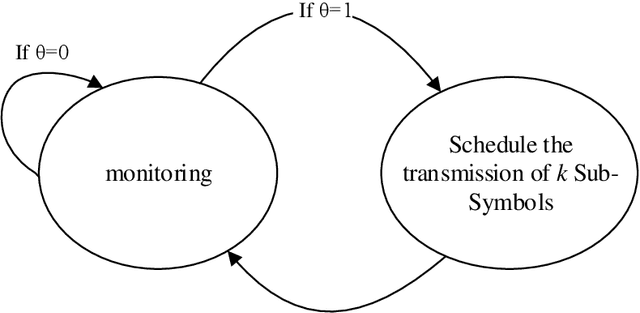
Abstract:This work introduces a new perspective for physical media sharing in multiuser communication by jointly considering (i) the meaning of the transmitted message and (ii) its function at the end user. Specifically, we have defined a scenario where multiple users (sensors) are continuously transmitting their own states concerning a predetermined event. On the receiver side there is an alarm monitoring system, whose function is to decide whether such a predetermined event has happened in a certain time period and, if yes, in which user. The media access control protocol proposed constitutes an alternative approach to the conventional physical layer methods, because the receiver does not decode the received waveform directly; rather, the relative position of the absence or presence of energy within a multidimensional resource space carries the (semantic) information. The protocol introduced here provides high efficiency in multiuser networks that operate with event-triggered sampling by enabling a constructive reconstruction of transmission collisions. We have demonstrated that the proposed method leads to a better event transmission efficiency than conventional methods like TDMA and slotted ALOHA. Remarkably, the proposed method achieves 100\% efficiency and 0\% error probability in almost all the studied cases, while consistently outperforming TDMA and slotted ALOHA.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge