Majid H. Khoshafa
Max-Min Secrecy Rate and Secrecy Energy Efficiency Optimization for RIS-Aided VLC Systems: RSMA Versus NOMA
May 08, 2025Abstract:Integrating VLC with the RIS significantly enhances physical layer security by enabling precise directional signal control and dynamic adaptation to the communication environment. These capabilities strengthen the confidentiality and security of VLC systems. This paper presents a comprehensive study on the joint optimization of VLC AP power allocation, RIS association, and RIS elements orientation angles for secure VLC systems, while considering RSMA and power-domain NOMA schemes. Specifically, two frameworks are proposed to maximize both the minimum secrecy rate (SR) and the minimum secrecy energy efficiency (SEE) by jointly optimizing power allocation, RIS association, and RIS elements orientation angles for both power-domain NOMA and RSMA-based VLC systems. The proposed frameworks consider random device orientation and guarantee the minimum user-rate requirement. The proposed optimization frameworks belong to the class of mixed integer nonlinear programming, which has no known feasible solution methodology to guarantee the optimal solution. Moreover, the increased degree of freedom and flexibility from the joint consideration of power control, RIS association and element orientation results in a large set of decision variables and constraints, which further complicates the optimization problem. To that end, we utilize a genetic algorithm-based solution method, which through its exploration and exploitation capabilities can obtain a good quality solution. Additionally, comprehensive simulations show that the RSMA scheme outperforms the power-domain NOMA scheme across both the SR and SEE metrics over various network parameters. Furthermore, useful insights on the impact of minimum user rate requirement, number of RIS elements, and maximum VLC AP transmit power on the minimum SR and SEE performances are provided.
Beyond Diagonal RIS-Aided Wireless Communications Systems: State-of-the-Art and Future Research Directions
Mar 11, 2025



Abstract:Integrating BD-RIS into wireless communications systems has attracted significant interest due to its transformative potential in enhancing system performance. This survey provides a comprehensive analysis of BD-RIS technology, examining its modeling, structural characteristics, and network integration while highlighting its advantages over traditional diagonal RIS. Specifically, we review various BD-RIS modeling approaches, including multiport network theory, graph theory, and matrix theory, and emphasize their application in diverse wireless scenarios. The survey also covers BD-RIS's structural diversity, including different scattering matrix types, transmission modes, intercell architectures, and circuit topologies, showing their flexibility in improving network performance. We delve into the potential applications of BD-RIS, such as enhancing wireless coverage, improving PLS, enabling multi-cell interference cancellation, improving precise sensing and localization, and optimizing channel manipulation. Further, we explore BD-RIS architectural development, providing insights into new configurations focusing on channel estimation, optimization, performance analysis, and circuit complexity perspectives. Additionally, we investigate the integration of BD-RIS with emerging wireless technologies, such as millimeter-wave and terahertz communications, integrated sensing and communications, mobile edge computing, and other cutting-edge technologies. These integrations are pivotal in advancing the capabilities and efficiency of future wireless networks. Finally, the survey identifies key challenges, including channel state information estimation, interference modeling, and phase-shift designs, and outlines future research directions. The survey aims to provide valuable insights into BD-RIS's potential in shaping the future of wireless communications systems.
RIS-Assisted Physical Layer Security in Emerging RF and Optical Wireless Communication Systems: A Comprehensive Survey
Mar 15, 2024



Abstract:Physical layer security (PLS) has received a growing interest from the research community for its ability to safeguard data confidentiality without relying on key distribution or encryption/decryption. However, the evolution towards the 5G technology and beyond poses new security challenges that must be addressed in order to fulfill the unprecedented performance requirements of future wireless networks. Among the potential enabling technologies, RIS has attracted extensive attention due to its ability to proactively and intelligently reconfigure the wireless propagation environment to combat dynamic wireless channel impairments. Consequently, the RIS technology can be adopted to improve the information-theoretic security of both RF and OWC systems. This survey paper provides a comprehensive overview of the information-theoretic security of RIS-based RF and optical systems. The article first discusses the fundamental concepts of PLS and RIS technologies, followed by their combination in both RF and OWC systems. Subsequently, some optimization techniques are presented in the context of the underlying system model, followed by an assessment of the impact of RIS-assisted PLS through a comprehensive performance analysis. Given that the computational complexity of future communication systems that adopt RIS-assisted PLS is likely to increase rapidly as the number of interactions between the users and infrastructure grows, ML is seen as a promising approach to address this complexity issue while sustaining or improving the network performance. A discussion of recent research studies on RIS-assisted PLS-based systems embedded with ML is presented. Furthermore, some important open research challenges are proposed and discussed to provide insightful future research directions, with the aim of moving a step closer towards the development and implementation of the forthcoming 6G wireless technology.
RIS-Aided Physical Layer Security Improvement in Underlay Cognitive Radio Networks
Sep 26, 2022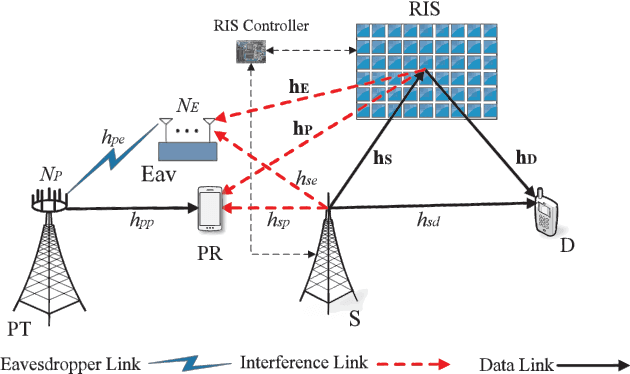
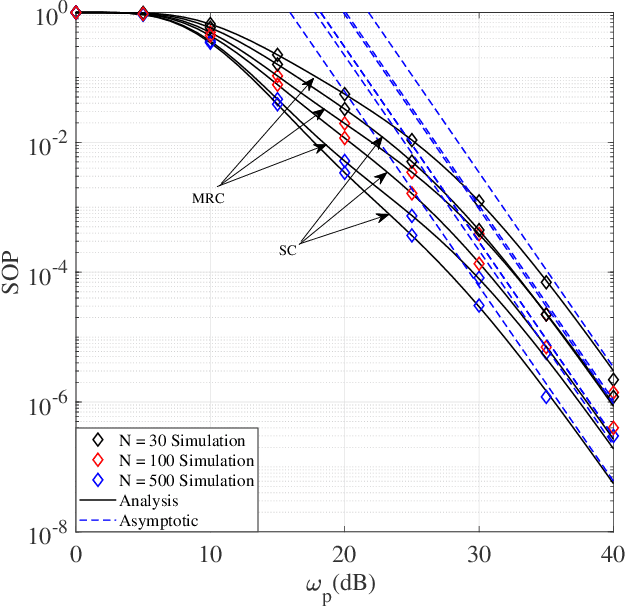
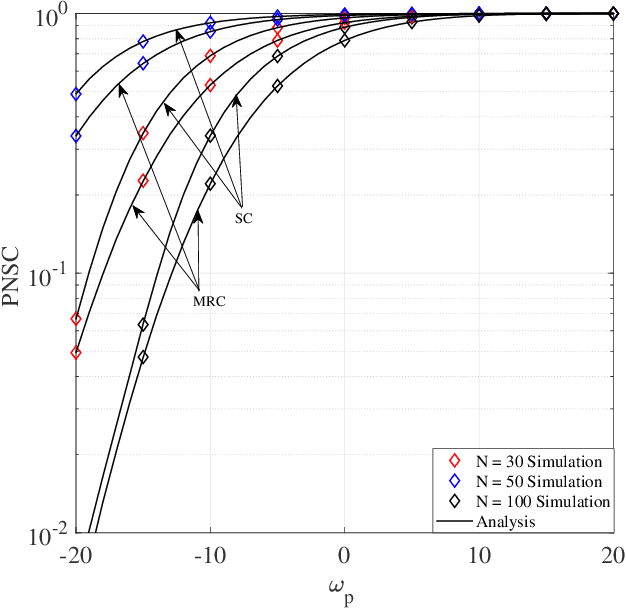
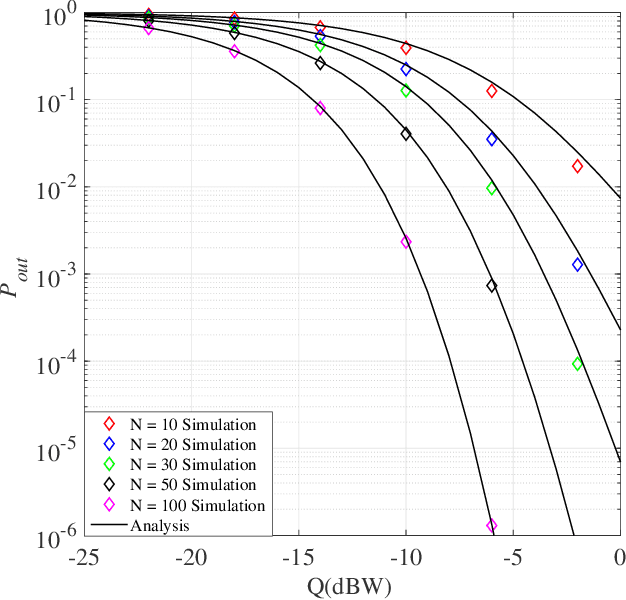
Abstract:In this paper, a reconfigurable intelligent surface (RIS)-aided underlay cognitive radio network is investigated. An RIS is utilized to improve the secondary network (SN) reliability and robustness while simultaneously increasing the physical layer security of the primary network (PN). Toward this end, closedform expressions for the SN outage probability, PN secrecy outage probability, and PN probability of non-zero secrecy capacity are derived. To increase the eavesdropping signals of the PN, the eavesdropper uses two combining techniques, namely maximal ratio combining and selection combining. Furthermore, the advantages of the proposed system model are verified through numerical and simulation results.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge