Khalid T. Mursi
Lightweight Strategy for XOR PUFs as Security Primitives for Resource-constrained IoT device
Oct 04, 2022



Abstract:Physical Unclonable Functions (PUFs) are promising security primitives for resource-constrained IoT devices. And the XOR Arbiter PUF (XOR-PUF) is one of the most studied PUFs, out of an effort to improve the resistance against machine learning attacks of probably the most lightweight delay-based PUFs - the Arbiter PUFs. However, recent attack studies reveal that even XOR-PUFs with large XOR sizes are still not safe against machine learning attacks. Increasing PUF stages or components and using different challenges for different components are two ways to improve the security of APUF-based PUFs, but more stages or components lead to more hardware cost and higher operation power, and different challenges for different components require the transmission of more bits during operations, which also leads to higher power consumption. In this paper, we present a strategy that combines the choice of XOR Arbiter PUF (XOR-PUF) architecture parameters with the way XOR-PUFs are used to achieve lightweights in hardware cost and energy consumption as well as security against machine learning attacks. Experimental evaluations show that with the proposed strategy, highly lightweight component-differentially challenged XOR-PUFs can withstand the most powerful machine learning attacks developed so far and maintain excellent intra-device and inter-device performance, rendering this strategy a potential blueprint for the fabrication and use of XOR-PUFs for resource-constrained IoT applications.
A New Security Boundary of Component Differentially Challenged XOR PUFs Against Machine Learning Modeling Attacks
Jun 02, 2022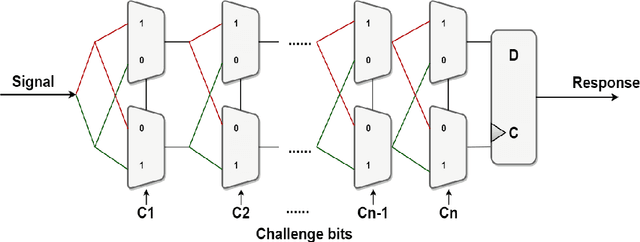
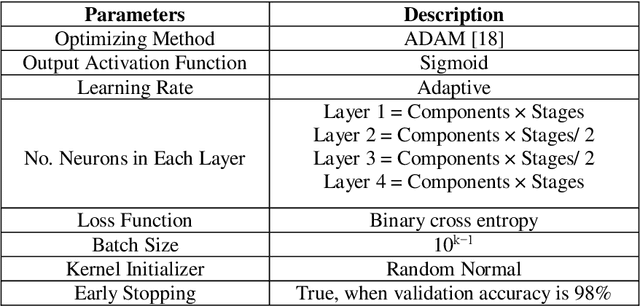

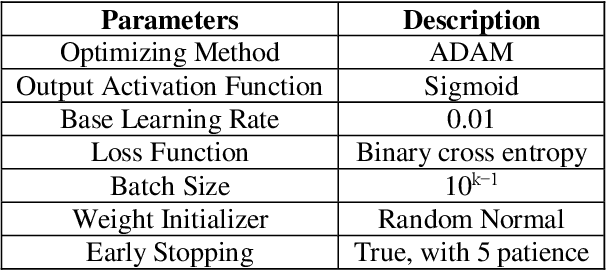
Abstract:Physical Unclonable Functions (PUFs) are promising security primitives for resource-constrained network nodes. The XOR Arbiter PUF (XOR PUF or XPUF) is an intensively studied PUF invented to improve the security of the Arbiter PUF, probably the most lightweight delay-based PUF. Recently, highly powerful machine learning attack methods were discovered and were able to easily break large-sized XPUFs, which were highly secure against earlier machine learning attack methods. Component-differentially-challenged XPUFs (CDC-XPUFs) are XPUFs with different component PUFs receiving different challenges. Studies showed they were much more secure against machine learning attacks than the conventional XPUFs, whose component PUFs receive the same challenge. But these studies were all based on earlier machine learning attack methods, and hence it is not clear if CDC-XPUFs can remain secure under the recently discovered powerful attack methods. In this paper, the two current most powerful two machine learning methods for attacking XPUFs are adapted by fine-tuning the parameters of the two methods for CDC-XPUFs. Attack experiments using both simulated PUF data and silicon data generated from PUFs implemented on field-programmable gate array (FPGA) were carried out, and the experimental results showed that some previously secure CDC-XPUFs of certain circuit parameter values are no longer secure under the adapted new attack methods, while many more CDC-XPUFs of other circuit parameter values remain secure. Thus, our experimental attack study has re-defined the boundary between the secure region and the insecure region of the PUF circuit parameter space, providing PUF manufacturers and IoT security application developers with valuable information in choosing PUFs with secure parameter values.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge