Jung-Yeon Hwang
A Symmetric Keyring Encryption Scheme for Biometric Cryptosystems
Sep 28, 2018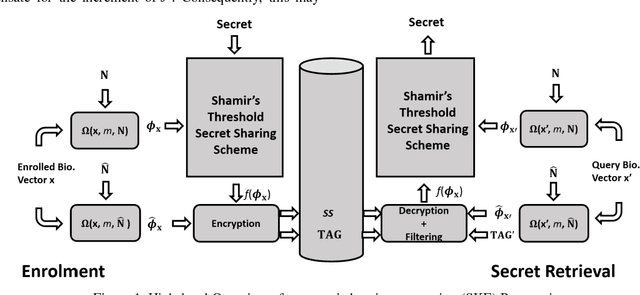
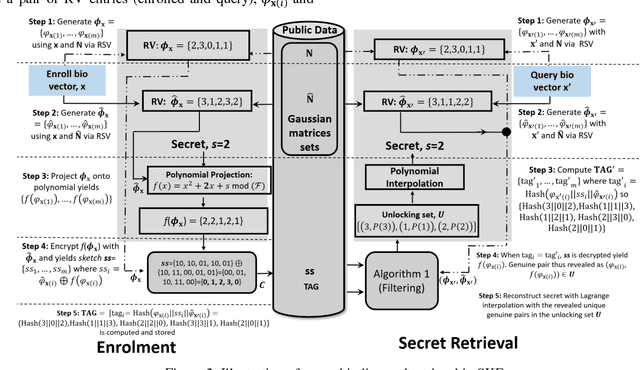
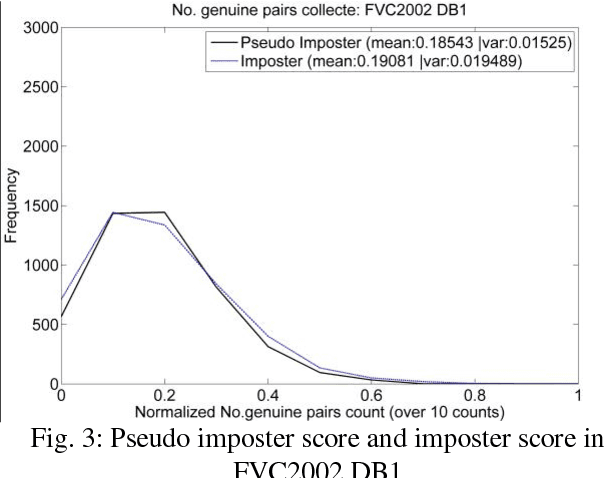
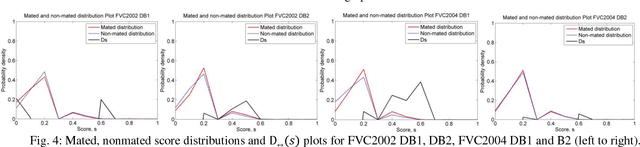
Abstract:In this paper, we propose a novel biometric cryptosystem for vectorial biometrics named symmetric keyring encryption (SKE) inspired by Rivest's keyring model (2016). Unlike conventional biometric secret-binding primitives, such as fuzzy commitment and fuzzy vault, the proposed scheme reframes the biometric secret-binding problem as a fuzzy symmetric encryption problem with a notion called resilient vector pair. In this study, the pair resembles the encryption-decryption key pair in symmetric key cryptosystems. This notion is realized using the index of maximum hashed vectors - a special instance of the ranking-based locality-sensitive hashing function. With a simple filtering mechanism and [m,k] Shamir's secret-sharing scheme, we show that SKE, both in theoretical and empirical evaluation, can retrieve the exact secret with overwhelming probability for a genuine input yet negligible probability for an imposter input. Though SKE can be applied to any vectorial biometrics, we adopt the fingerprint vector as a case of study in this work. The experiments have been performed under several subsets of FVC 2002, 2004, and 2006 datasets. We formalize and analyze the threat model of SKE that encloses several major security attacks.
Ranking Based Locality Sensitive Hashing Enabled Cancelable Biometrics: Index-of-Max Hashing
Sep 17, 2017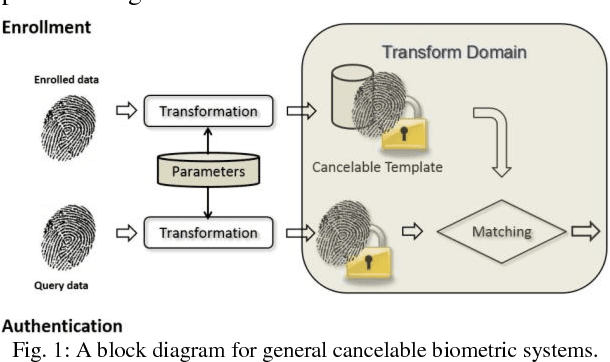
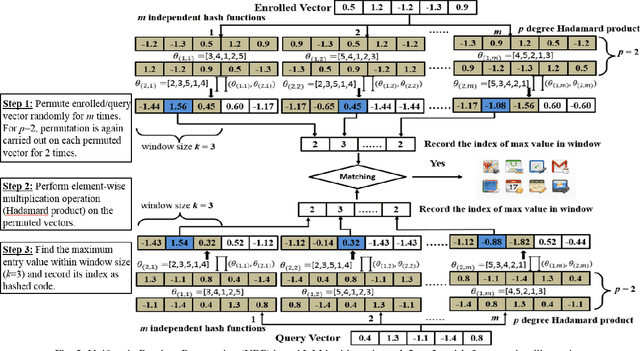
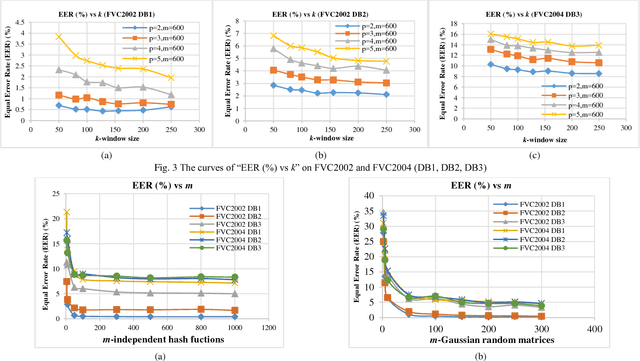
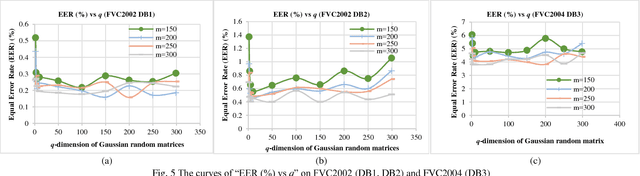
Abstract:In this paper, we propose a ranking based locality sensitive hashing inspired two-factor cancelable biometrics, dubbed "Index-of-Max" (IoM) hashing for biometric template protection. With externally generated random parameters, IoM hashing transforms a real-valued biometric feature vector into discrete index (max ranked) hashed code. We demonstrate two realizations from IoM hashing notion, namely Gaussian Random Projection based and Uniformly Random Permutation based hashing schemes. The discrete indices representation nature of IoM hashed codes enjoy serveral merits. Firstly, IoM hashing empowers strong concealment to the biometric information. This contributes to the solid ground of non-invertibility guarantee. Secondly, IoM hashing is insensitive to the features magnitude, hence is more robust against biometric features variation. Thirdly, the magnitude-independence trait of IoM hashing makes the hash codes being scale-invariant, which is critical for matching and feature alignment. The experimental results demonstrate favorable accuracy performance on benchmark FVC2002 and FVC2004 fingerprint databases. The analyses justify its resilience to the existing and newly introduced security and privacy attacks as well as satisfy the revocability and unlinkability criteria of cancelable biometrics.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge