Walling up Backdoors in Intrusion Detection Systems
Paper and Code
Oct 17, 2019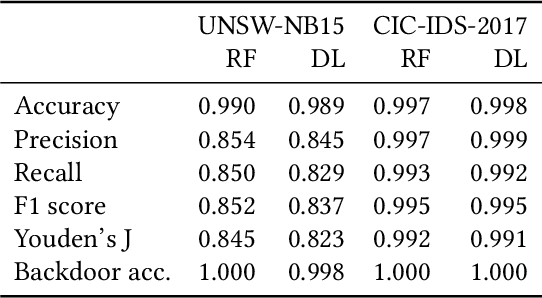
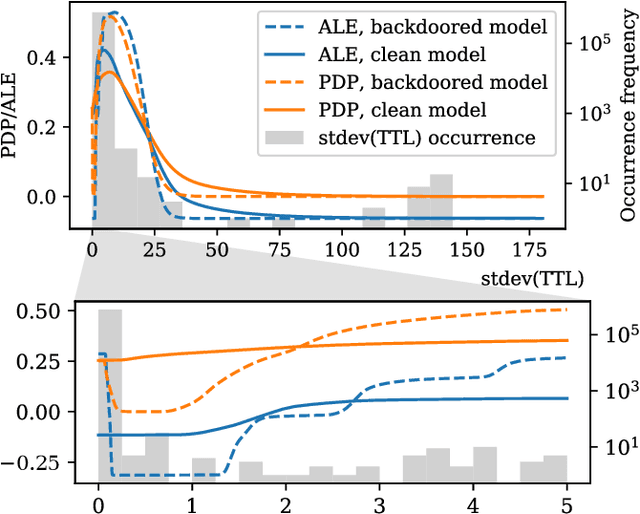
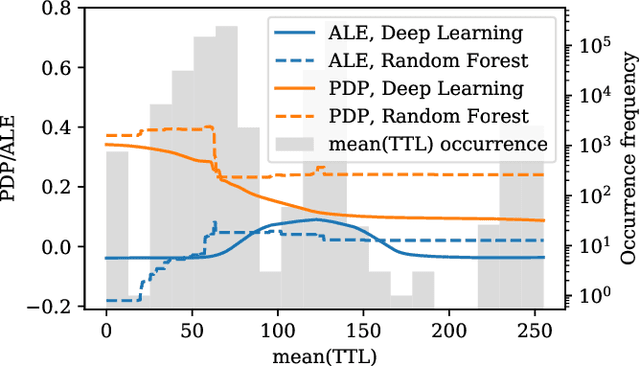
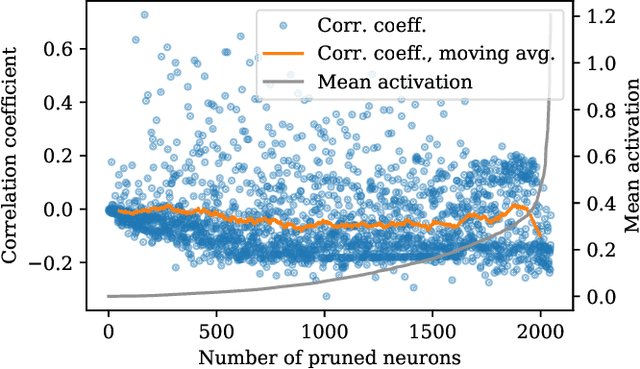
Interest in poisoning attacks and backdoors recently resurfaced for Deep Learning (DL) applications. Several successful defense mechanisms have been recently proposed for Convolutional Neural Networks (CNNs), for example in the context of autonomous driving. We show that visualization approaches can aid in identifying a backdoor independent of the used classifier. Surprisingly, we find that common defense mechanisms fail utterly to remove backdoors in DL for Intrusion Detection Systems (IDSs). Finally, we devise pruning-based approaches to remove backdoors for Decision Trees (DTs) and Random Forests (RFs) and demonstrate their effectiveness for two different network security datasets.
* 3rd ACM CoNEXT Workshop on Big DAta, Machine Learning and
Artificial Intelligence for Data Communication Networks (Big-DAMA '19),
December 9, 2019, Orlando, FL, USA
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge