Raja Kumar Murugesan
A Data Quarantine Model to Secure Data in Edge Computing
Nov 15, 2021



Abstract:Edge computing provides an agile data processing platform for latency-sensitive and communication-intensive applications through a decentralized cloud and geographically distributed edge nodes. Gaining centralized control over the edge nodes can be challenging due to security issues and threats. Among several security issues, data integrity attacks can lead to inconsistent data and intrude edge data analytics. Further intensification of the attack makes it challenging to mitigate and identify the root cause. Therefore, this paper proposes a new concept of data quarantine model to mitigate data integrity attacks by quarantining intruders. The efficient security solutions in cloud, ad-hoc networks, and computer systems using quarantine have motivated adopting it in edge computing. The data acquisition edge nodes identify the intruders and quarantine all the suspected devices through dimensionality reduction. During quarantine, the proposed concept builds the reputation scores to determine the falsely identified legitimate devices and sanitize their affected data to regain data integrity. As a preliminary investigation, this work identifies an appropriate machine learning method, Linear Discriminant Analysis (LDA), for dimensionality reduction. The LDA results in 72.83% quarantine accuracy and 0.9 seconds training time, which is efficient than other state-of-the-art methods. In future, this would be implemented and validated with ground truth data.
A Comparative Analysis of Machine Learning Algorithms for Intrusion Detection in Edge-Enabled IoT Networks
Nov 02, 2021
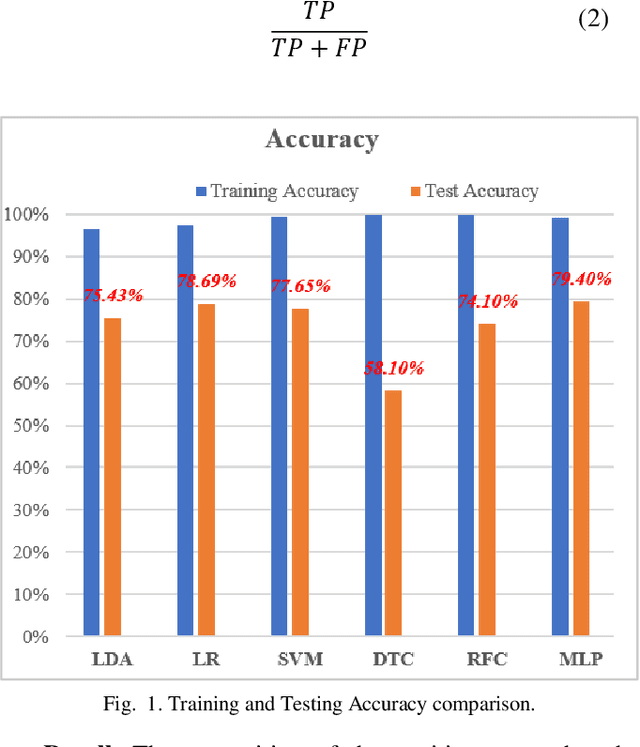
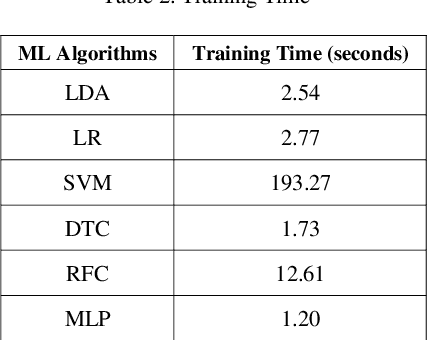
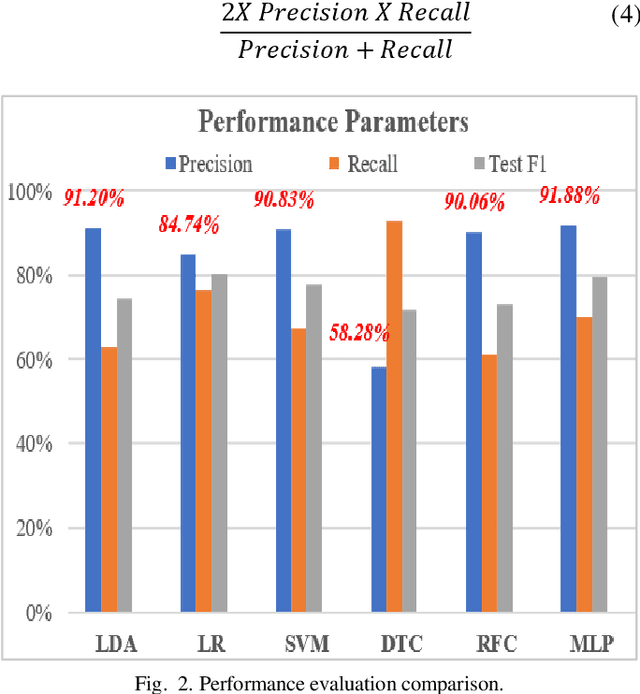
Abstract:A significant increase in the number of interconnected devices and data communication through wireless networks has given rise to various threats, risks and security concerns. Internet of Things (IoT) applications is deployed in almost every field of daily life, including sensitive environments. The edge computing paradigm has complemented IoT applications by moving the computational processing near the data sources. Among various security models, Machine Learning (ML) based intrusion detection is the most conceivable defense mechanism to combat the anomalous behavior in edge-enabled IoT networks. The ML algorithms are used to classify the network traffic into normal and malicious attacks. Intrusion detection is one of the challenging issues in the area of network security. The research community has proposed many intrusion detection systems. However, the challenges involved in selecting suitable algorithm(s) to provide security in edge-enabled IoT networks exist. In this paper, a comparative analysis of conventional machine learning classification algorithms has been performed to categorize the network traffic on NSL-KDD dataset using Jupyter on Pycharm tool. It can be observed that Multi-Layer Perception (MLP) has dependencies between input and output and relies more on network configuration for intrusion detection. Therefore, MLP can be more appropriate for edge-based IoT networks with a better training time of 1.2 seconds and testing accuracy of 79%.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge