Nikolaos Athanasios Anagnostopoulos
Emerging Threats and Countermeasures in Neuromorphic Systems: A Survey
Jan 23, 2026Abstract:Neuromorphic computing mimics brain-inspired mechanisms through spiking neurons and energy-efficient processing, offering a pathway to efficient in-memory computing (IMC). However, these advancements raise critical security and privacy concerns. As the adoption of bio-inspired architectures and memristive devices increases, so does the urgency to assess the vulnerability of these emerging technologies to hardware and software attacks. Emerging architectures introduce new attack surfaces, particularly due to asynchronous, event-driven processing and stochastic device behavior. The integration of memristors into neuromorphic hardware and software implementations in spiking neural networks offers diverse possibilities for advanced computing architectures, including their role in security-aware applications. This survey systematically analyzes the security landscape of neuromorphic systems, covering attack methodologies, side-channel vulnerabilities, and countermeasures. We focus on both hardware and software concerns relevant to spiking neural networks (SNNs) and hardware primitives, such as Physical Unclonable Functions (PUFs) and True Random Number Generators (TRNGs) for cryptographic and secure computation applications. We approach this analysis from diverse perspectives, from attack methodologies to countermeasure strategies that integrate efficiency and protection in brain-inspired hardware. This review not only maps the current landscape of security threats but provides a foundation for developing secure and trustworthy neuromorphic architectures.
Ear Recognition
Jan 26, 2021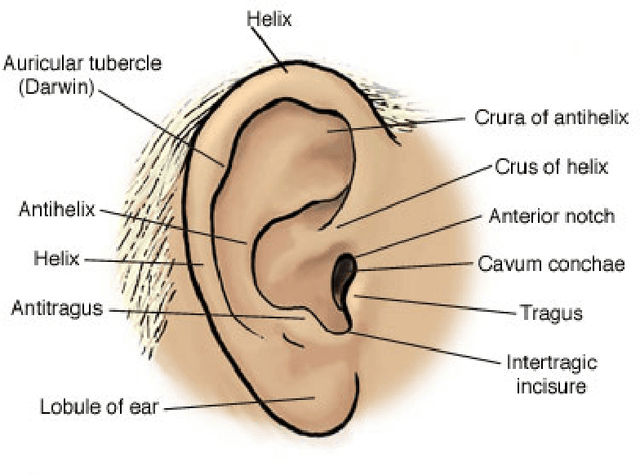
Abstract:Ear recognition can be described as a revived scientific field. Ear biometrics were long believed to not be accurate enough and held a secondary place in scientific research, being seen as only complementary to other types of biometrics, due to difficulties in measuring correctly the ear characteristics and the potential occlusion of the ear by hair, clothes and ear jewellery. However, recent research has reinstated them as a vivid research field, after having addressed these problems and proven that ear biometrics can provide really accurate identification and verification results. Several 2D and 3D imaging techniques, as well as acoustical techniques using sound emission and reflection, have been developed and studied for ear recognition, while there have also been significant advances towards a fully automated recognition of the ear. Furthermore, ear biometrics have been proven to be mostly non-invasive, adequately permanent and accurate, and hard to spoof and counterfeit. Moreover, different ear recognition techniques have proven to be as effective as face recognition ones, thus providing the opportunity for ear recognition to be used in identification and verification applications. Finally, even though some issues still remain open and require further research, the scientific field of ear biometrics has proven to be not only viable, but really thriving.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge