Matthias R. Brust
Detecting Target-Area Link-Flooding DDoS Attacks using Traffic Analysis and Supervised Learning
Mar 01, 2019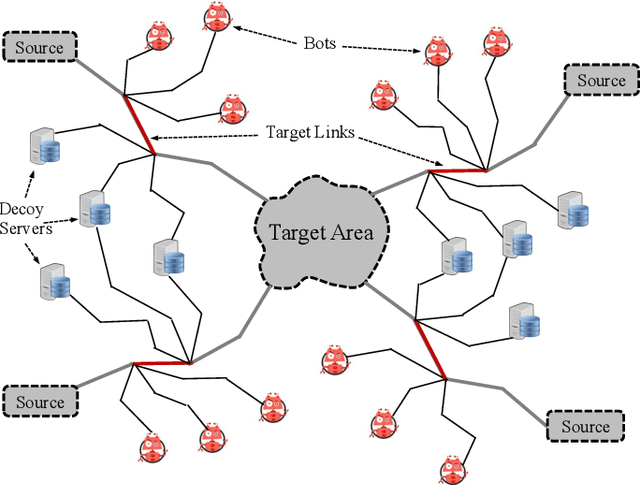
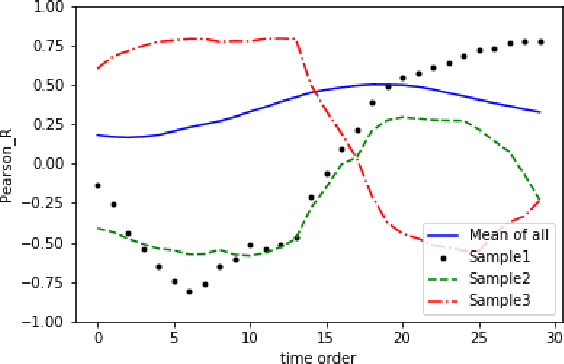
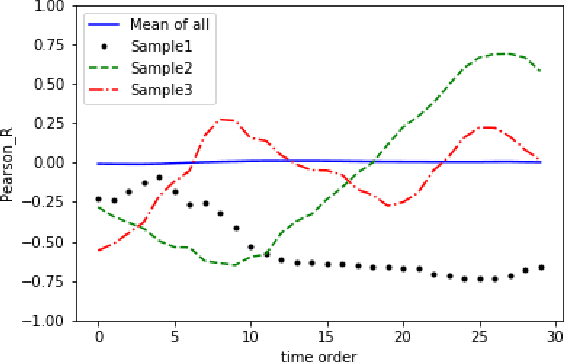
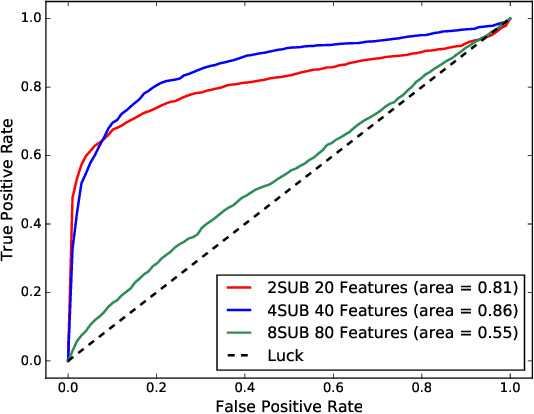
Abstract:A novel class of extreme link-flooding DDoS (Distributed Denial of Service) attacks is designed to cut off entire geographical areas such as cities and even countries from the Internet by simultaneously targeting a selected set of network links. The Crossfire attack is a target-area link-flooding attack, which is orchestrated in three complex phases. The attack uses a massively distributed large-scale botnet to generate low-rate benign traffic aiming to congest selected network links, so-called target links. The adoption of benign traffic, while simultaneously targeting multiple network links, makes detecting the Crossfire attack a serious challenge. In this paper, we present analytical and emulated results showing hitherto unidentified vulnerabilities in the execution of the attack, such as a correlation between coordination of the botnet traffic and the quality of the attack, and a correlation between the attack distribution and detectability of the attack. Additionally, we identified a warm-up period due to the bot synchronization. For attack detection, we report results of using two supervised machine learning approaches: Support Vector Machine (SVM) and Random Forest (RF) for classification of network traffic to normal and abnormal traffic, i.e, attack traffic. These machine learning models have been trained in various scenarios using the link volume as the main feature set.
* arXiv admin note: text overlap with arXiv:1801.00235
Defending against Intrusion of Malicious UAVs with Networked UAV Defense Swarms
Sep 02, 2018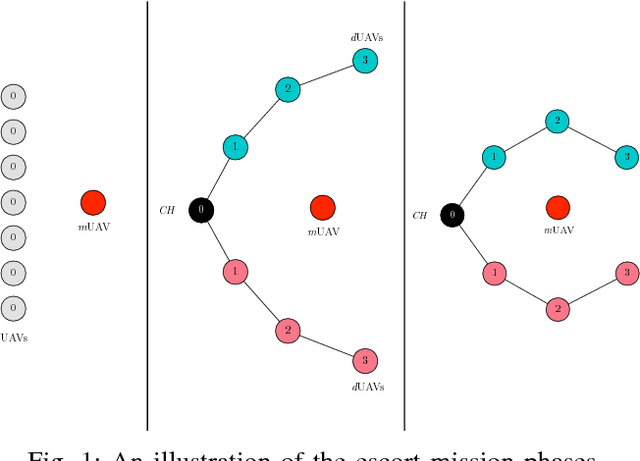
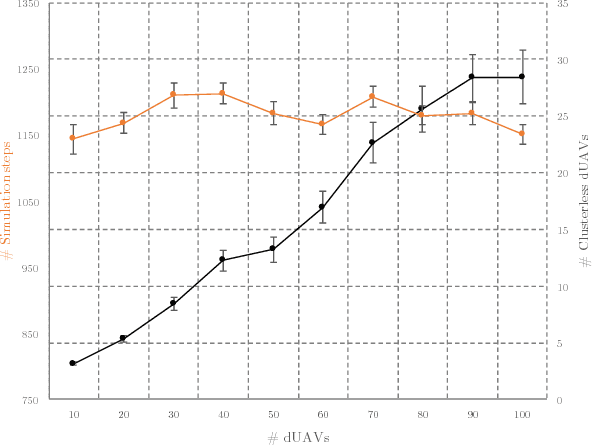
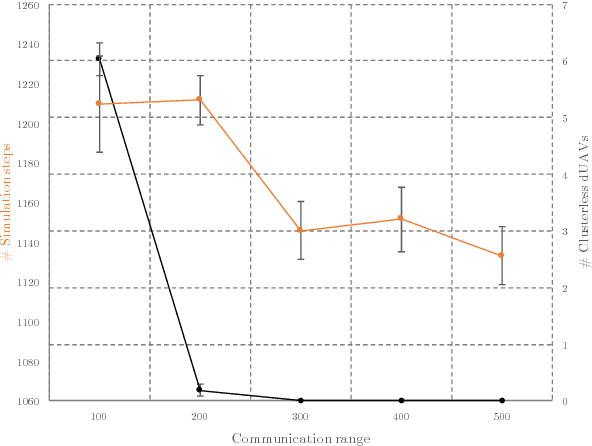
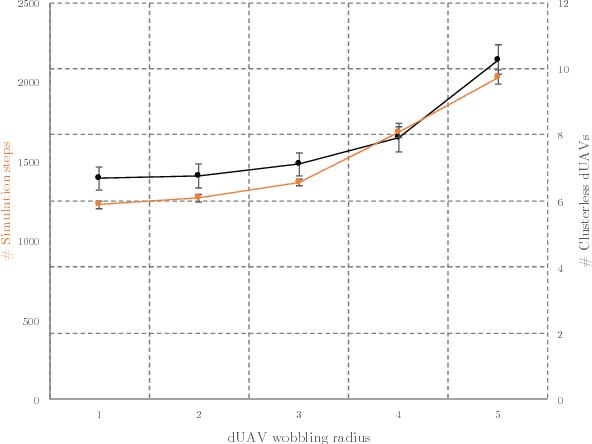
Abstract:Nowadays, companies such as Amazon, Alibaba, and even pizza chains are pushing forward to use drones, also called UAVs (Unmanned Aerial Vehicles), for service provision, such as package and food delivery. As governments intend to use these immense economic benefits that UAVs have to offer, urban planners are moving forward to incorporate so-called UAV flight zones and UAV highways in their smart city designs. However, the high-speed mobility and behavior dynamics of UAVs need to be monitored to detect and, subsequently, to deal with intruders, rogue drones, and UAVs with a malicious intent. This paper proposes a UAV defense system for the purpose of intercepting and escorting a malicious UAV outside the flight zone. The proposed UAV defense system consists of a defense UAV swarm, which is capable to self-organize its defense formation in the event of intruder detection, and chase the malicious UAV as a networked swarm. Modular design principles have been used for our fully localized approach. We developed an innovative auto-balanced clustering process to realize the intercept- and capture-formation. As it turned out, the resulting networked defense UAV swarm is resilient against communication losses. Finally, a prototype UAV simulator has been implemented. Through extensive simulations, we show the feasibility and performance of our approach.
A Networked Swarm Model for UAV Deployment in the Assessment of Forest Environments
Jul 15, 2016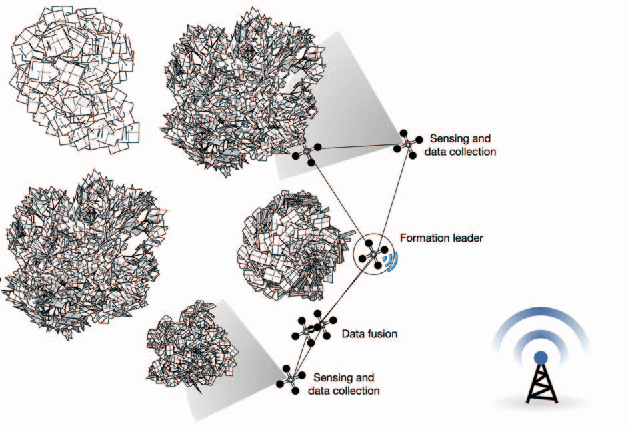
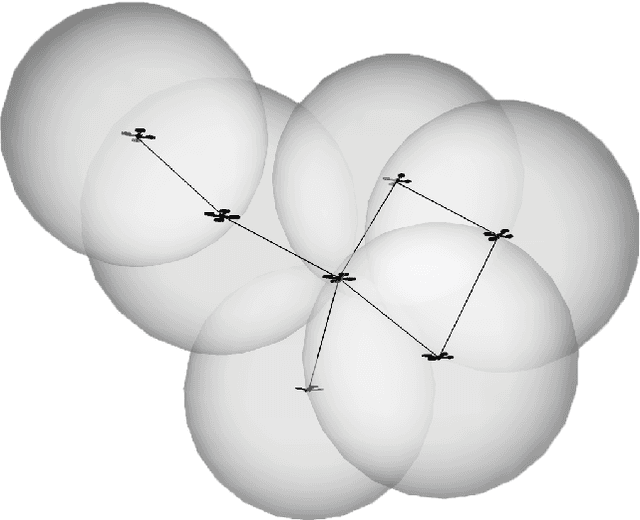
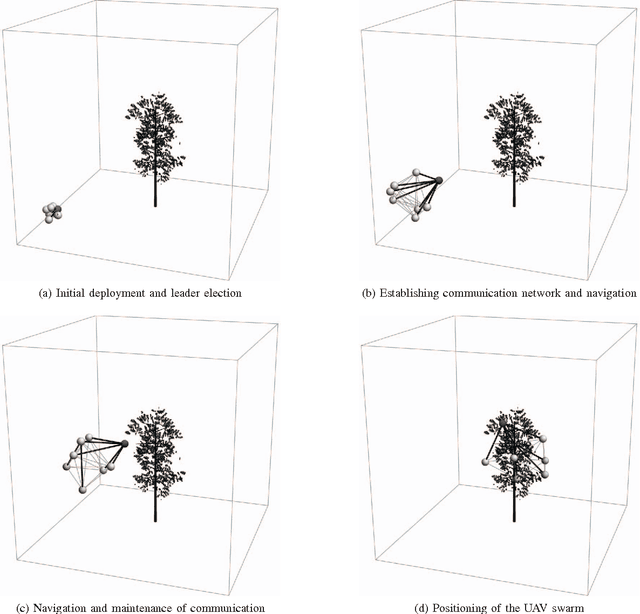
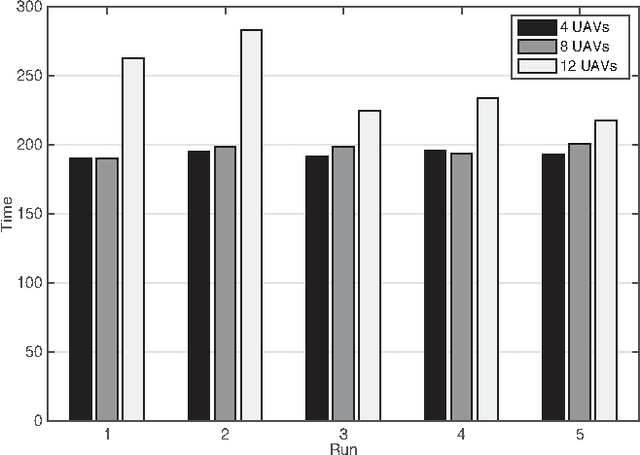
Abstract:Autonomous Unmanned Aerial Vehicles (UAVs) have gained popularity due to their many potential application fields. Alongside sophisticated sensors, UAVs can be equipped with communication adaptors aimed for inter-UAV communication. Inter-communication of UAVs to form a UAV swarm raises questions on how to manage its communication structure and mobility. In this paper, we consider therefore the problem of establishing an efficient swarm movement model and a network topology between a collection of UAVs, which are specifically deployed for the scenario of high-quality forest-mapping. The forest environment with its highly heterogeneous distribution of trees and obstacles represents an extreme challenge for a UAV swarm. It requires the swarm to constantly avoid possible collisions with trees, to change autonomously the trajectory, which can lead to disconnection to the swarm, and to reconnect to the swarm after passing the obstacle, while continue collecting environmental data that needs to be fused and assessed efficiently. In this paper, we propose a novel solution to the formation flight problem for UAV swarms. The proposed method provides an adaptive and reliable network structure, which maintains swarm connectivity and communicability. These characteristics are needed to achieve a detailed and accurate description of the environment from the data acquired by the UAV swarm. The main characteristics of our approach are high scalability regarding the number of UAVs in the swarm and the adaptive network topology within the swarm.
Consensus Dynamics in a non-deterministic Naming Game with Shared Memory
Dec 23, 2009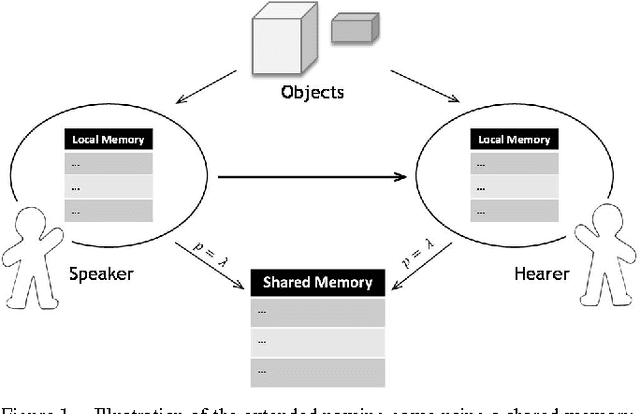
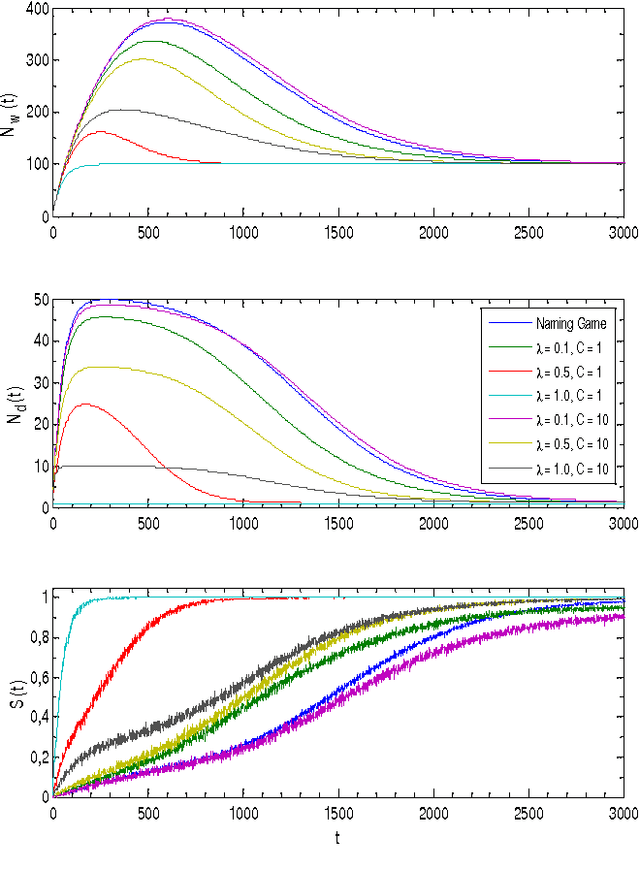
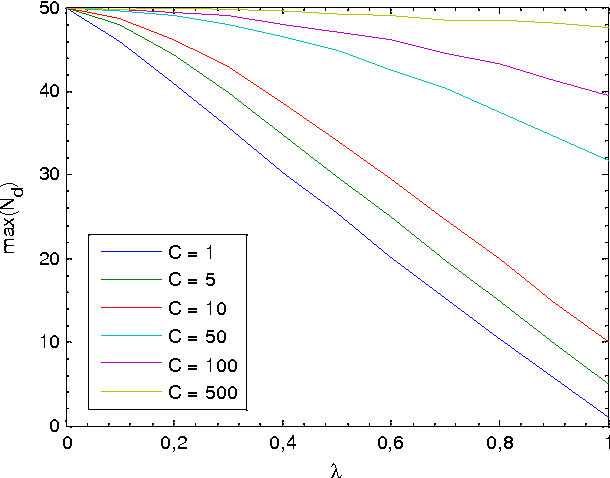
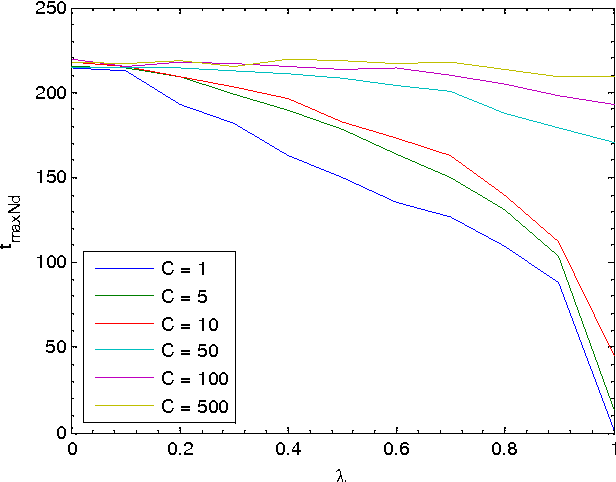
Abstract:In the naming game, individuals or agents exchange pairwise local information in order to communicate about objects in their common environment. The goal of the game is to reach a consensus about naming these objects. Originally used to investigate language formation and self-organizing vocabularies, we extend the classical naming game with a globally shared memory accessible by all agents. This shared memory can be interpreted as an external source of knowledge like a book or an Internet site. The extended naming game models an environment similar to one that can be found in the context of social bookmarking and collaborative tagging sites where users tag sites using appropriate labels, but also mimics an important aspect in the field of human-based image labeling. Although the extended naming game is non-deterministic in its word selection, we show that consensus towards a common vocabulary is reached. More importantly, we show the qualitative and quantitative influence of the external source of information, i.e. the shared memory, on the consensus dynamics between the agents.
Optimal Design of Ad Hoc Injection Networks by Using Genetic Algorithms
Jul 20, 2007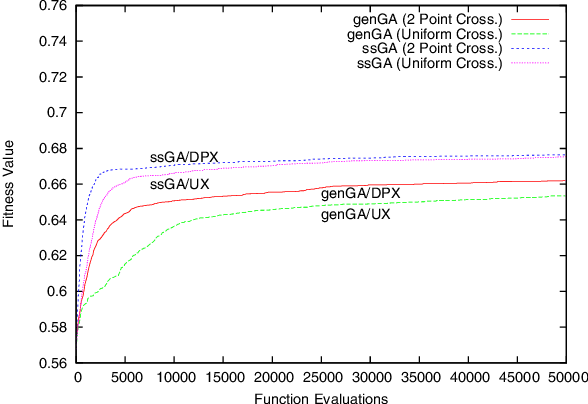
Abstract:This work aims at optimizing injection networks, which consist in adding a set of long-range links (called bypass links) in mobile multi-hop ad hoc networks so as to improve connectivity and overcome network partitioning. To this end, we rely on small-world network properties, that comprise a high clustering coefficient and a low characteristic path length. We investigate the use of two genetic algorithms (generational and steady-state) to optimize three instances of this topology control problem and present results that show initial evidence of their capacity to solve it.
* 1 page, 1 figure
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge