Marcin Niemiec
Building a Bridge between the Two Schools: Realizing a Practical Path to Include Literacy-based Skills within the STEM Curricula
Jan 24, 2026Abstract:Developing students as well-rounded professionals is increasingly important for our modern society. Although there is a great consensus that technical and professional ("soft") skills should be developed and intertwined in the core of computer science subjects, there are still few examples of alike teaching methodologies at technical schools. This contribution investigates the integration of technical and professional skills while teaching specialized curricula in computer science. We propose a broadly applicable, step-by-step methodology that connects core technical concepts (e.g., information entropy, network security) with fine arts practices such as music, video production, gaming, and performing arts (e.g., Oxford-style debates). The methodology was applied in several computer science courses at technical universities, where quantitative and qualitative assessments, including student questionnaires and exam scores, showed improved learning outcomes and increased student engagement compared to traditional methods. The results indicate that this art-based integration can effectively bridge the historical divide between the two schools of thought, offering a practical direction for educators. Within this context, we also identify open issues that will guide future research on topics such as instructor engagement, female motivation in technical subjects, and scalability of these approaches.
Synchronization of Tree Parity Machines using non-binary input vectors
Apr 22, 2021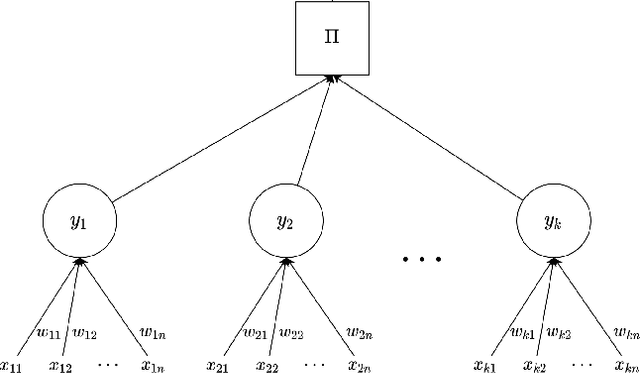
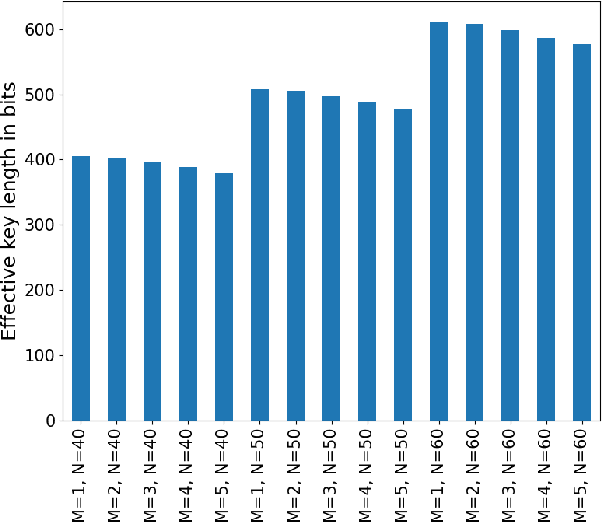
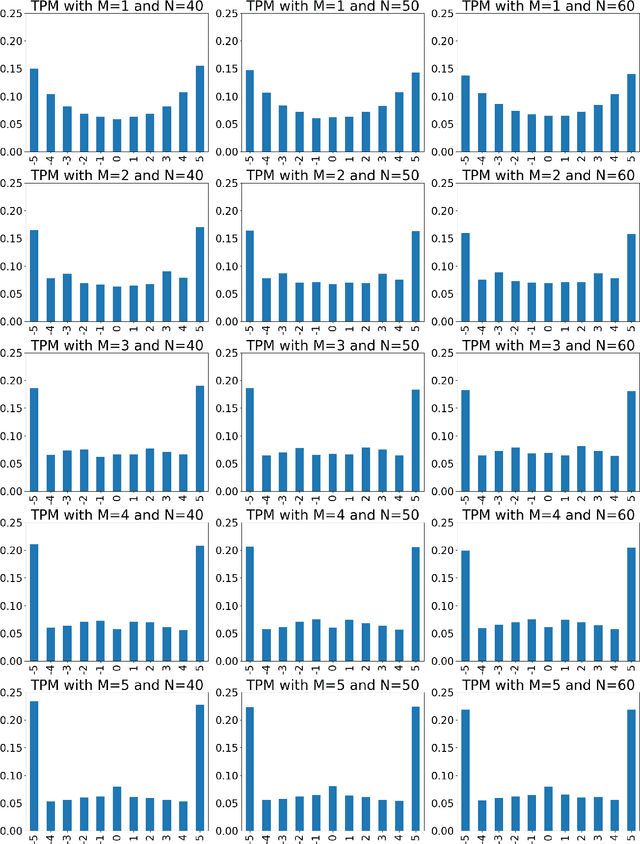
Abstract:Neural cryptography is the application of artificial neural networks in the subject of cryptography. The functionality of this solution is based on a tree parity machine. It uses artificial neural networks to perform secure key exchange between network entities. This article proposes improvements to the synchronization of two tree parity machines. The improvement is based on learning artificial neural network using input vectors which have a wider range of values than binary ones. As a result, the duration of the synchronization process is reduced. Therefore, tree parity machines achieve common weights in a shorter time due to the reduction of necessary bit exchanges. This approach improves the security of neural cryptography
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge