Mansoor Davoodi
Stochastic Multi-Objective Multi-Armed Bandits: Regret Definition and Algorithm
Jun 16, 2025Abstract:Multi-armed bandit (MAB) problems are widely applied to online optimization tasks that require balancing exploration and exploitation. In practical scenarios, these tasks often involve multiple conflicting objectives, giving rise to multi-objective multi-armed bandits (MO-MAB). Existing MO-MAB approaches predominantly rely on the Pareto regret metric introduced in \cite{drugan2013designing}. However, this metric has notable limitations, particularly in accounting for all Pareto-optimal arms simultaneously. To address these challenges, we propose a novel and comprehensive regret metric that ensures balanced performance across conflicting objectives. Additionally, we introduce the concept of \textit{Efficient Pareto-Optimal} arms, which are specifically designed for online optimization. Based on our new metric, we develop a two-phase MO-MAB algorithm that achieves sublinear regret for both Pareto-optimal and efficient Pareto-optimal arms.
Stable Trajectory Clustering: An Efficient Split and Merge Algorithm
Apr 30, 2025Abstract:Clustering algorithms group data points by characteristics to identify patterns. Over the past two decades, researchers have extended these methods to analyze trajectories of humans, animals, and vehicles, studying their behavior and movement across applications. This paper presents whole-trajectory clustering and sub-trajectory clustering algorithms based on DBSCAN line segment clustering, which encompasses two key events: split and merge of line segments. The events are employed by object movement history and the average Euclidean distance between line segments. In this framework, whole-trajectory clustering considers entire entities' trajectories, whereas sub-trajectory clustering employs a sliding window model to identify similar sub-trajectories. Many existing trajectory clustering algorithms respond to temporary anomalies in data by splitting trajectories, which often obscures otherwise consistent clustering patterns and leads to less reliable insights. We introduce the stable trajectory clustering algorithm, which leverages the mean absolute deviation concept to demonstrate that selective omission of transient deviations not only preserves the integrity of clusters but also improves their stability and interpretability. We run all proposed algorithms on real trajectory datasets to illustrate their effectiveness and sensitivity to parameter variations.
Hole Detection and Healing in Hybrid Sensor Networks
Jun 20, 2021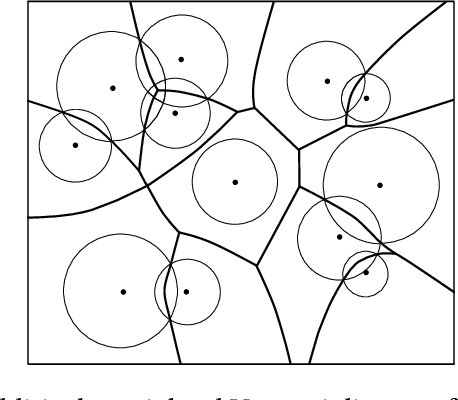
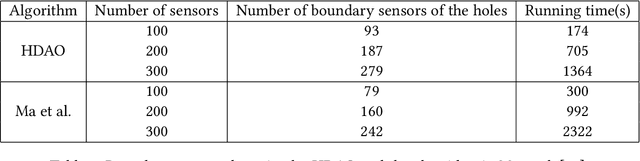
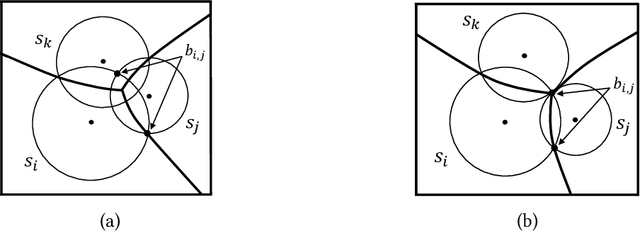
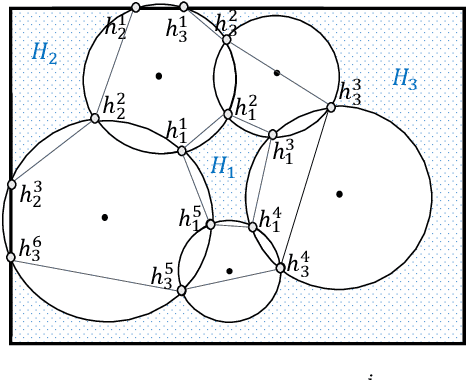
Abstract:Although monitoring and covering are fundamental goals of a wireless sensor network (WSN), the accidental death of sensors or the running out of their energy would result in holes in the WSN. Such holes have the potential to disrupt the primary functions of WSNs. This paper investigates the hole detection and healing problems in hybrid WSNs with non-identical sensor sensing ranges. In particular, we aim to propose centralized algorithms for detecting holes in a given region and maximizing the area covered by a WSN in the presence of environmental obstacles. To precisely identify the boundary of the holes, we use an additively weighted Voronoi diagram and a polynomial-time algorithm.Furthermore, since this problem is known to be computationally difficult, we propose a centralized greedy 1/2-approximation algorithm to maximize the area covered by sensors. Finally, we implement the algorithms and run simulations to show that our approximation algorithm efficiently covers the holes by moving the mobile sensors.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge