Process Mining Analysis of Puzzle-Based Cybersecurity Training
Paper and Code
Mar 29, 2022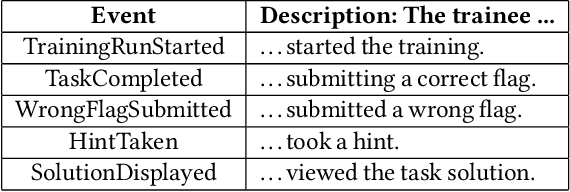
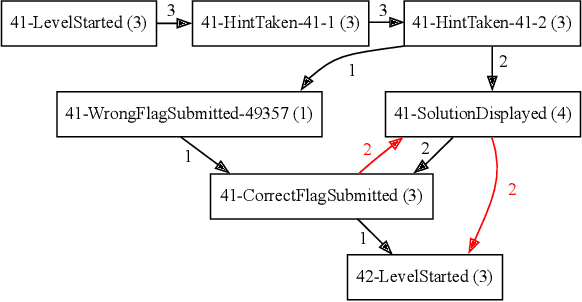
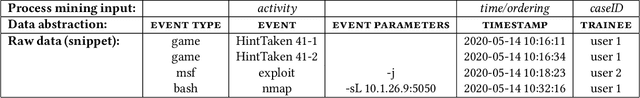

The hands-on cybersecurity training quality is crucial to mitigate cyber threats and attacks effectively. However, practical cybersecurity training is strongly process-oriented, making the post-training analysis very difficult. This paper presents process-mining methods applied to the learning analytics workflow. We introduce a unified approach to reconstruct behavioral graphs from sparse event logs of cyber ranges. Furthermore, we discuss significant data features that affect their practical usability for educational process mining. Based on that, methods of dealing with the complexity of process graphs are presented, taking advantage of the puzzle-based gamification of in-class training sessions.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge